Exploring CEH Module 3: Scanning Networks
After selecting a target and initial reconnaissance, as described in the Footprinting and Reconnaissance module, attackers search for access points into the target system, determining the system’s activity status to streamline scanning efforts. Scanning, a deeper reconnaissance form, reveals information about the target’s operating systems. This module provides an overview of network scanning techniques, including live system checks, port and service discovery, and strategies to circumvent IDS and firewalls.

What is Network Scanning?
Network scanning is a critical process in cybersecurity for acquiring in-depth information about a target by employing advanced reconnaissance tactics. Network scanning encompasses procedures for detecting hosts, ports, and services within a network and is also instrumental in discovering the Operating Systems (OS) on the active machines. This is a crucial step for information collection for an attacker, facilitating the construction of a comprehensive profile of the target organization. During the scanning process, an attacker collects specific IP addresses that are reachable across the network, the system architecture of the target’s OS, and the services active on each system.
First, we will explore a selection of network scanning tools featured in this module. Then, leveraging these tools, we will guide you through the process of conducting a comprehensive network scan. The following list highlights the top network scanning tools used for scanning.
1. Nmap: Nmap can identify devices running on a network, discover open ports, detect security risks, and more.
2. Hping3: Hping3 allows users to send custom TCP/IP packets and analyze the responses, making it useful for network testing, firewall testing, manual packet crafting, and network performance analysis.
3. Nessus: Nessus is used to detect potential vulnerabilities in networked devices, such as weaknesses in firewalls, malware infections, and outdated software. It is known for its extensive plugin library that automates the detection of vulnerabilities.
4. Zenmap: Zenmap is crafted to make Nmap easy to use for beginners yet it retains sophisticated features that appeal to experienced users of Nmap. It helps visualize network topologies and vulnerabilities through intuitive graphical representations.
5. Angry IP scanner: Angry IP scanner is an open-source and multi-platform network scanner designed to be fast and simple to use. It scans IP addresses and ports and has many other features.
6. Netcat: Netcat is a flexible networking tool that operates over TCP/IP and is reliable for various programs and scripts. Due to its wide range of functionalities, it’s often called the “Swiss army knife” of networking tools.
Types of Scanning
1. Network Scanning
Do you ever think about knowing which device is active on the network? Network scanning is the technique that lets you pinpoint all devices currently active on your network. It typically involves sending pings to all possible IP addresses within a network to identify active devices. A manual ARP scan can be used to discover local subnets. Automated scanning tools are recommended to detect devices across multiple subnets. ICMP scans, which are more complex and may include echo, timestamp, or subnet mask requests, are useful for mapping network topology. Let’s see how Nmap is used in network scanning.
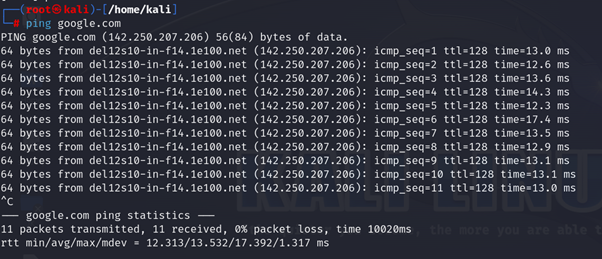
- Ping: It sends an ICMP echo request to the target system and reverts the echo if the system is live.
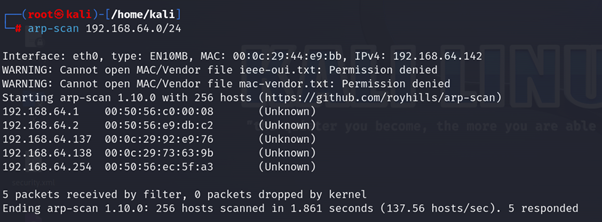
- ARP scan: ARP Scan is used to identify other active hosts on a local network.
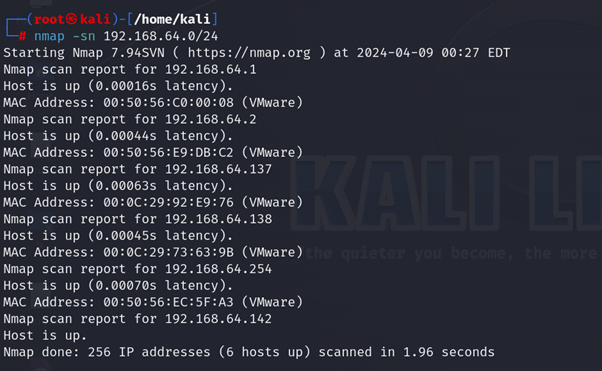
- Ping Sweep: A Ping Sweep, also known as an ICMP Sweep or Ping Scan, enables simultaneous scanning of multiple systems on a server to gather information efficiently in a single operation.
2. Port Scanning
Once the host’s activity is confirmed, the user then proceeds to identify the operational ports and services within the network.
Different Techniques for Port Scanning
- Full scan (nmap target ip): The command nmap target_ip performs a scan on a specified target IP address using its default settings. This typically involves identifying open ports, detecting the target’s operating system, and possibly running services.
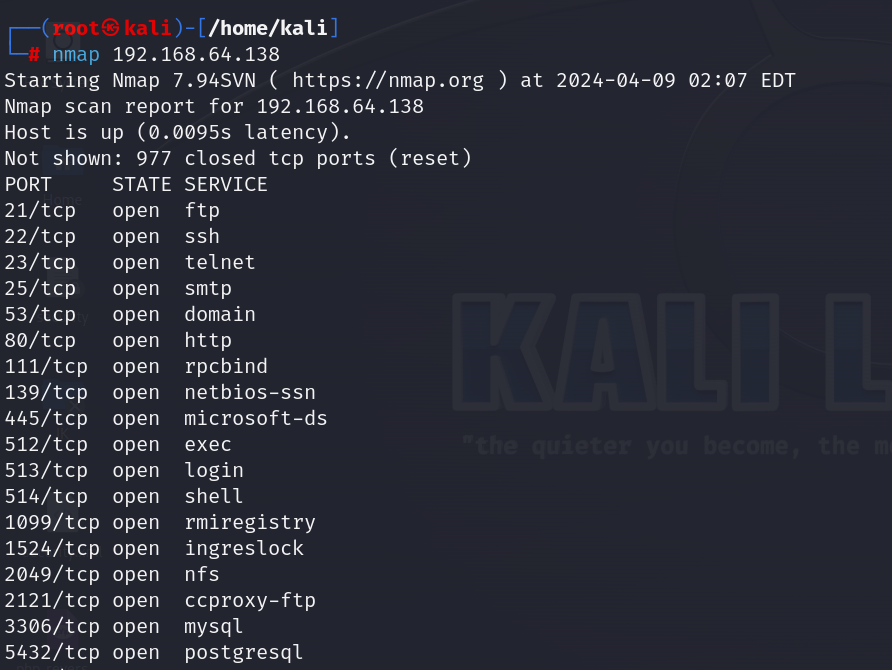
- TCP scan
Full scan (nmap -sT target ip): The command nmap -sT target_ip performs a TCP connect scan on the specified target IP address. This scan type attempts to establish a full TCP connection with each targeted port. It essentially completes the traditional three-way handshake process (SYN, SYN-ACK, ACK) used by TCP to initiate a connection. If the connection is successfully established, the port is considered open.
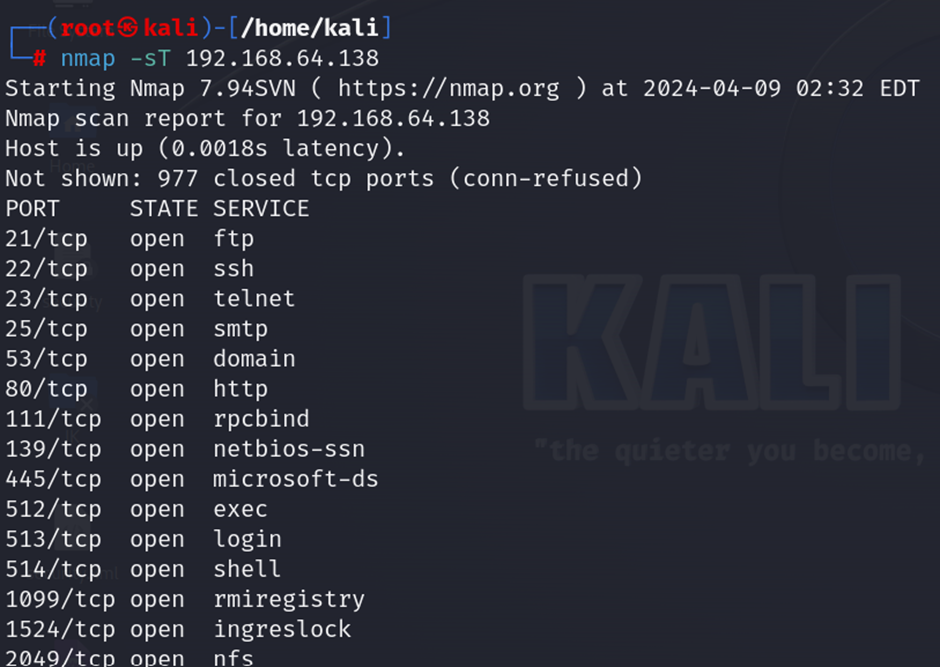
- Half-scan/stealth scan
nmap -sS target ip: The command nmap -sS target_ip performs a SYN scan on the specified target IP address. This type of TCP scan is often referred to as a “half-open” scan because it doesn’t complete the TCP connection. It sends a SYN packet (indicating the start of a TCP connection) to the target. If the target port is open, it will respond with a SYN-ACK packet, after which Nmap sends an RST packet to close the connection before it’s fully established.
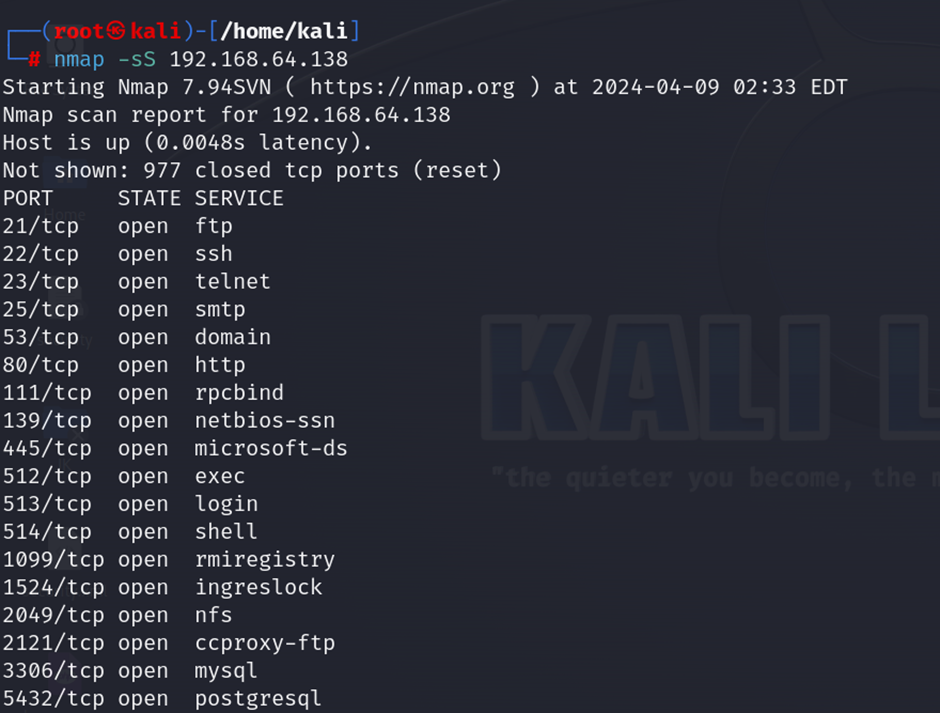
- FIN Scan
nmap -sF -target ip: The nmap -sF target_ip command performs a FIN scan using Nmap against the specified target IP address. A FIN scan sends TCP FIN packets to the target. According to TCP protocol standards, a closed port is expected to reply with an RST packet, while an open port will ignore the FIN packet. This behavior can be used to infer which ports are open.
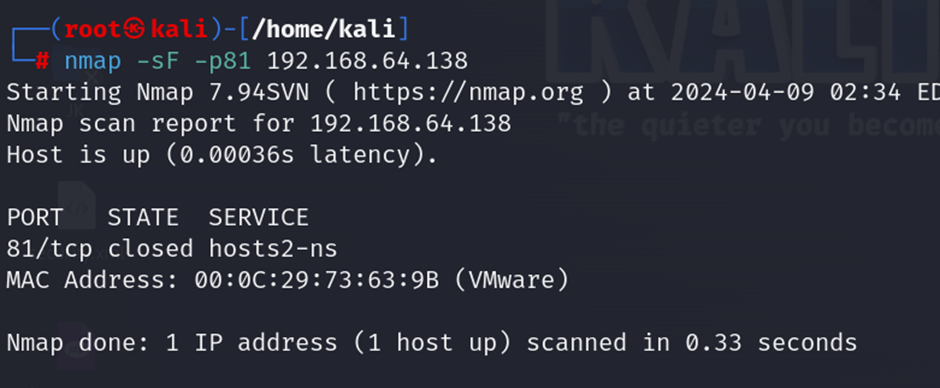
- UDP scan
nmap -sU target ip: The command nmap -sU target_ip uses Nmap to perform a UDP scan on a specified target. This scan type is designed to identify open UDP ports on the target system, which can help discover the services running on those ports.

- X-mas scan (nmap -sX -p80 ip): This command is used to identify open ports and detect potential vulnerabilities on a target machine’s IP address.
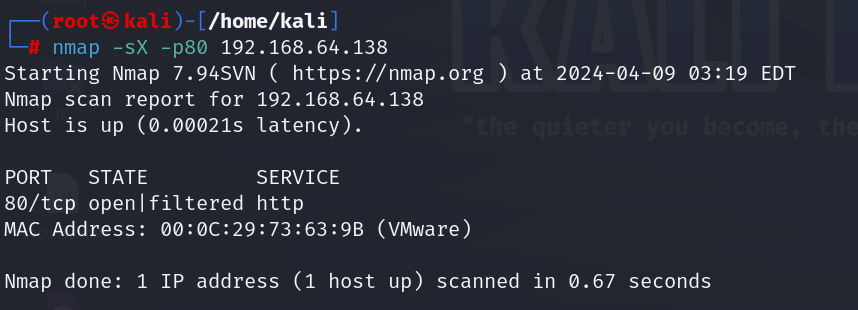
3. Vulnerability scanning
Vulnerability scanning is a crucial cybersecurity process aimed at identifying security weaknesses and flaws in systems and the software running on them.
Nmap target IP –script vuln: This command instructs Nmap to scan the specified target IP address and utilize scripts from its vulnerability scanning suite (–script vuln).
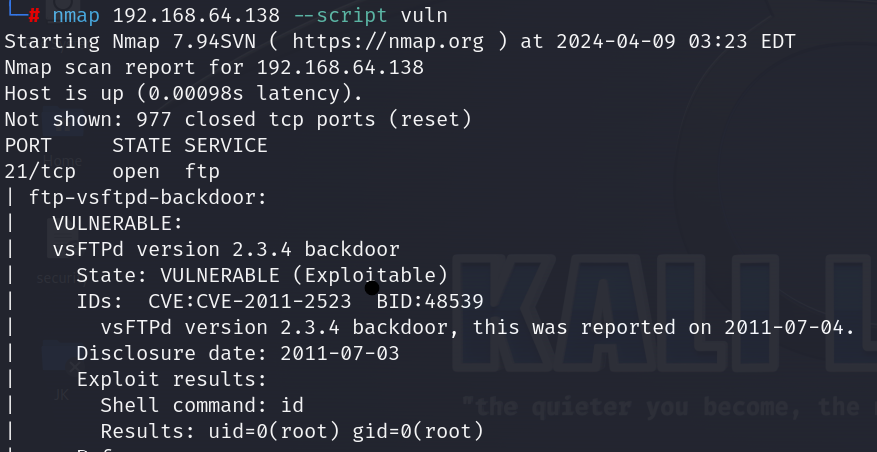
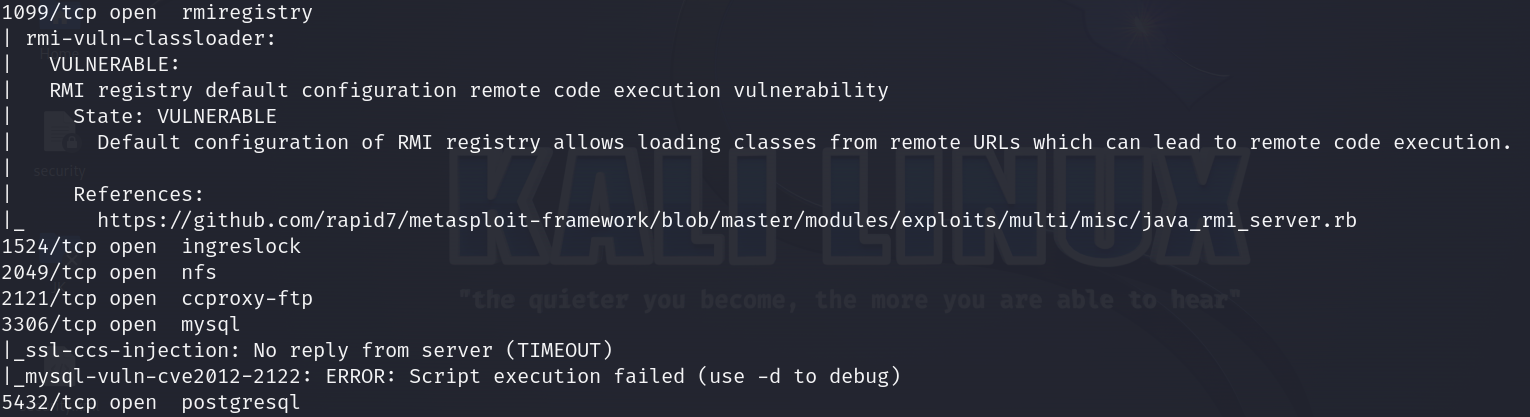
4. Operating System Fingerprinting
Operating System (OS) Fingerprinting is a technique used in network scanning and network management to determine the operating system of a remote computer. Active OS fingerprinting involves sending packets to a target and analyzing the responses. This method can provide detailed information about the target’s OS but carries a higher risk of detection by intrusion detection systems (IDS), intrusion prevention systems (IPS), or firewalls.
- nmap -O target_ip: The command nmap -O target_ip is used with Nmap to conduct an operating system detection scan on the specified target IP address. This option enables Nmap’s OS detection feature, which uses a combination of TCP/IP stack fingerprinting techniques to guess the operating system running on the target machine. It sends a series of TCP and UDP packets to the target and examines the responses to determine characteristics unique to specific operating systems.
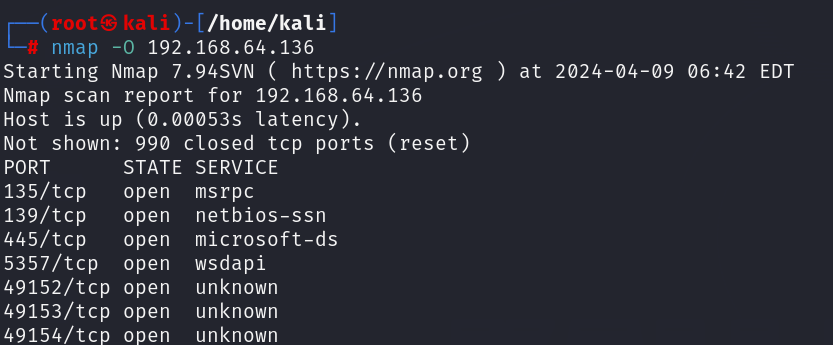
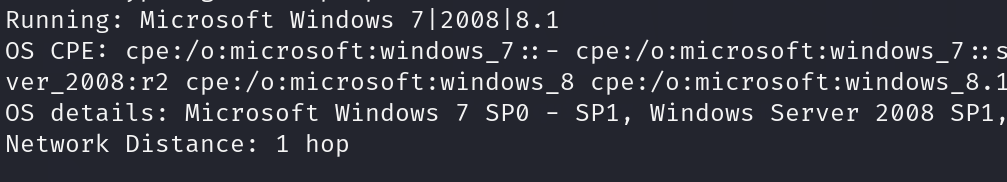
5. Service and Version Scanning
Service and Version Scanning is a process used in network security and administration to identify the services running on the ports of a targeted system and to determine the specific versions of those services.
- nmap -sV ip_address: The command nmap -sV ip_address is used with Nmap to perform a service version detection scan on the specified IP address.
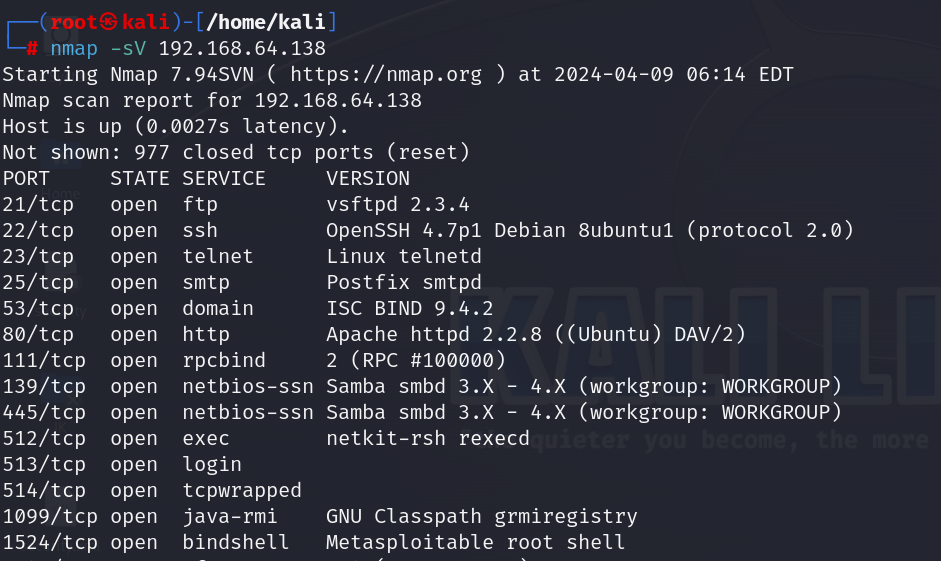
6. Packet Crafting
Packet crafting is a technique used for probing firewall rule sets and finding entry points into targeted systems or networks by manually generating packets to test network behaviors and devices rather than using existing network traffic.
hping3 -A ip_address: The hping3 -A ip_address command is used to send ACK packets to a specified IP address using hping3, a command-line network tool. This can be utilized to test firewalls, ports, and network behavior under certain conditions. The -A option specifically indicates that ACK packets will be sent, which is a part of the TCP handshake process, often used to see how a system responds to unsolicited TCP acknowledgments, aiding in network analysis and security testing.
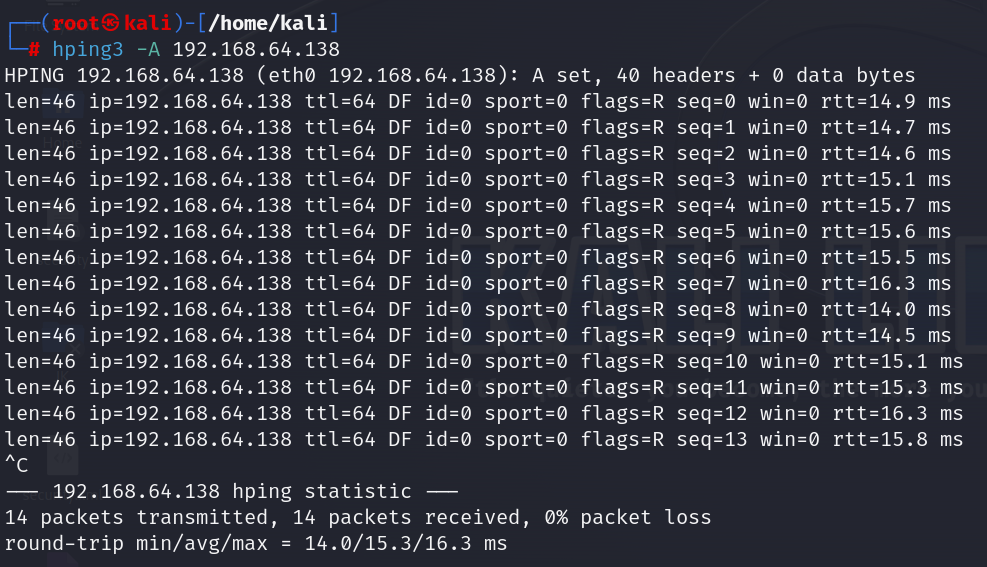
Note: Advance Nmap users don’t have to stick to just the standard scan options. The “–scanflags” feature with Nmap creates custom scans by choosing specific TCP flags. So what is a TCP flag?
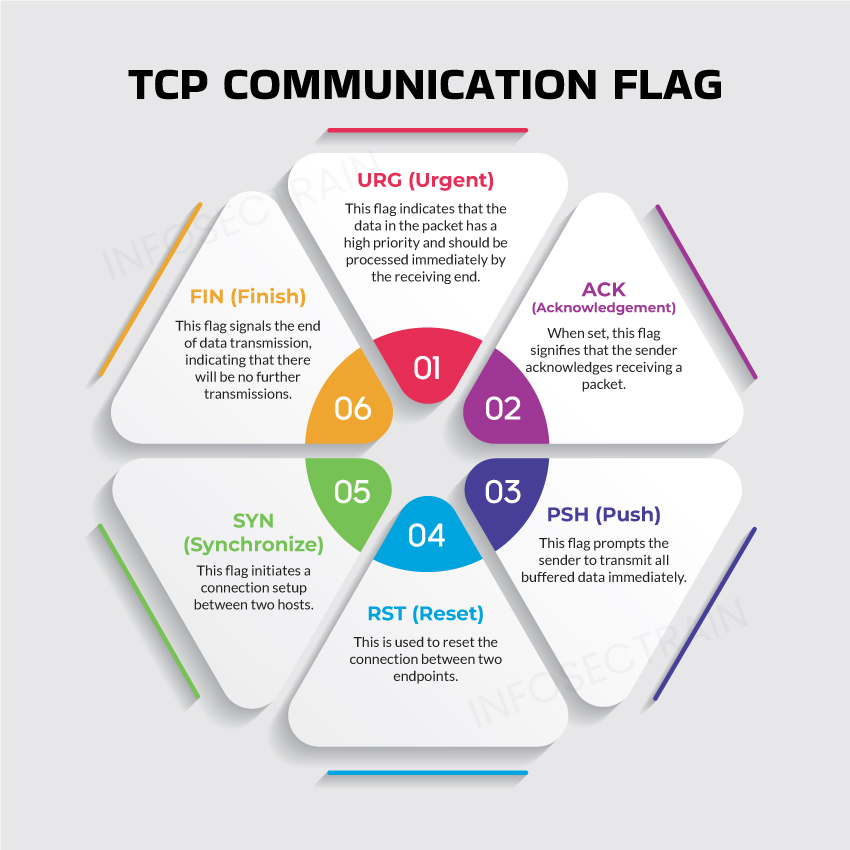
What is a TCP Flag?
The TCP header includes flags crucial for managing data transmission over a TCP connection. Six control flags facilitate communication between hosts and provide directives to the system. The flags SYN, ACK, FIN, and RST initiate, sustain, and conclude a connection. The remaining two flags, PSH and URG, are used for specific system instructions. Each flag occupies a single bit, leading to a total of six bits for the TCP Flags section in the header. Setting a flag’s value to ‘1’ activates that particular flag.
TCP/IP Communication
TCP/IP communication is designed to prioritize establishing a connection before starting data transfer. Here’s a summary of the initiation of a TCP session using the three-way handshake mechanism:
- The source sends a SYN packet to the destination to request a connection.
- The destination replies with a SYN/ACK packet, acknowledging the request.
- The source sends back an ACK packet, confirming the receipt of the SYN/ACK.
- This exchange opens the connection, allowing communication until a FIN or RST packet is sent to close it.
Master CEH with InfosecTrain
Ethical hacking is a complex and multi-phase process that requires deep knowledge and security certifications. Professionals can improve their security assessment and network architecture skills through ethical hacking courses, such as the Certified Ethical Hacker (CEH) training provided by InfosecTrain. This training provides individuals with the essential skills and methods needed to perform sanctioned hacking into organizations.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)