Exploring SSCP Domain 3: Risk Identification, Monitoring, and Analysis for a Career in IT Security
Modern businesses are exposed to a variety of threats and risks in their day-to-day IT operations. The risk management process is one of the most significant components of any organization because it is responsible for the security of all of the data stored there. The success of the organization’s projects depends on effective risk management. As a result, the security practitioner is expected to identify risks to information systems and develop and execute controls to reduce those risks. For this, security professionals need to be well-versed in risk, response, and recovery concepts and best practices. This article will cover the third domain of SSCP: Risk Identification, Monitoring, and Analysis, and what you can expect in the SSCP exam from this domain.

Domains of SSCP
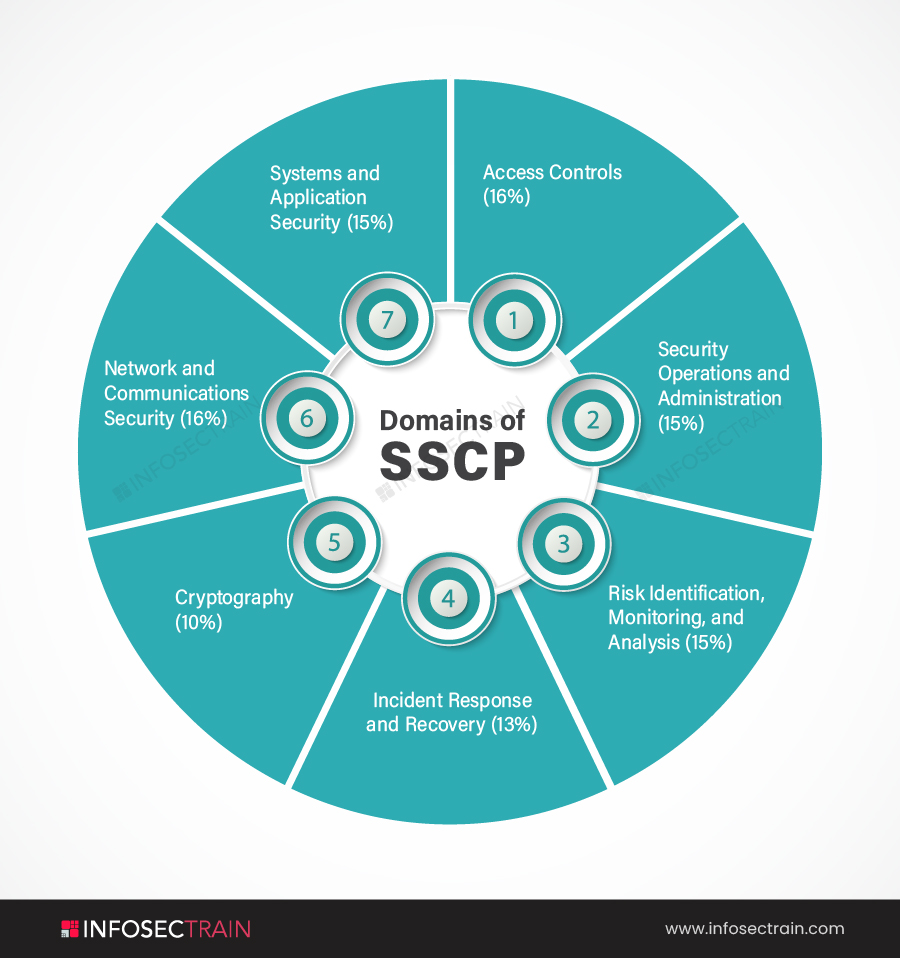
The seven SSCP domains are:
- Domain 1: Access Controls (16%)
- Domain 2: Security Operations and Administration (15%)
- Domain 3: Risk Identification, Monitoring, and Analysis (15%)
- Domain 4: Incident Response and Recovery (13%)
- Domain 5: Cryptography (10%)
- Domain 6: Network and Communications Security (16%)
- Domain 7: Systems and Application Security (15%)
Domain 3: Risk Identification, Monitoring, and Analysis
Domain 3 of the SSCP certification exam is Risk Identification, Monitoring, and Analysis. The Risk Identification, Monitoring, and Analysis domain comprise a 15% weightage of the SSCP certification. This domain is concerned with the systematic assessment techniques which are used to identify and monitor threats continuously. Every business is vulnerable to potential threats. This domain will highlight the importance of implementing controls to mitigate or eliminate threats or vulnerabilities, lowering the overall risk for the organization. You will learn about risk management concepts, risk assessment, and standard risk management approaches used by businesses, such as insurance, risk reduction, and possibly risk avoidance. It will also discuss the necessity of monitoring and evaluating log files to find events and incidents as they occur and ways for participating in risk reduction and risk response operations. Overall, this domain is concerned with how the security practitioner is expected to contribute to the organizational risk management process, identify information system risks, and develop and implement controls to minimize identified risks. It is an important topic from an exam perspective. The subtopics covered in Risk Identification, Monitoring, and Analysis domains are:
- Understand the risk management process
- Perform security assessment activities
- Operate and maintain monitoring systems
- Analyze monitoring results
1. Understand the Risk Management Process
This subsection will discuss the risk management process in-depth. The concept of IT security in an organization’s IT operations focuses on risk management. A risk management process outlines a company’s procedures for detecting and controlling threats to its digital assets, such as confidential corporate data, personally identifiable information (PII) of customers, and intellectual property. This part will cover the fundamentals of risk management, characteristics of risk visibility and reporting, and risk analysis approaches and risk management frameworks. It will also cover how to deal with risks and the various steps taken to mitigate them. Accept, reduce/mitigate, transfer, and avoid are the four types of risk treatment.
2. Perform Security Assessment Activities
This subsection will cover all the security testing and evaluation approaches. Any organization’s security depends on how well it assesses security risks. This section will teach you how to recognize, measure, and control losses caused by adverse events. It will teach how to examine, analyze, choose, and evaluate risk-mitigation measures. You will learn how to collect data, detect security events, assign priority levels, take appropriate steps, and report your findings to the relevant people. It will go into SIEM (security information and event management) systems, visualization and reporting, software testing, etc. This section will also discuss auditing, an independent assessment of a company’s records and actions. This section will also cover the security audits to find weaknesses in technical and administrative information systems and networks. It will discuss how to incorporate audit findings into the risk management process.
3. Operate and Maintain Monitoring Systems
This subsection will go through audit logging, security events, audit trails, retention periods, and acceptable media concepts and procedures. It will discuss events of interest as part of continuous monitoring activities. It will also discuss how to safeguard records from being tampered with, keep them secure, and back up the logs we generate. It will also cover topics such as the fundamentals of source systems used in continuous monitoring, legal and regulatory concerns, and more.
4. Analyze Monitoring Results
This subsection will cover the monitoring of the identified risk. Passive, active, and real-time risk monitoring are the three types of risk monitoring. It will also cover tools like enterprise risk management, which uses dashboards, graphs, risk registers, scorecards, and risk maps to create baselines. This section will go through monitoring tools and approaches that can help reduce the amount of data in audit records and distill relevant information from raw data. It will discuss the concepts of visualization, metrics, and trends to analyze monitoring results. It will go over the fundamentals of event data analysis and their purpose, and how to communicate and report monitoring analysis data in the best way possible.
SSCP with InfosecTrain
Enroll in the SSCP certification training course at InfosecTrain. We are one of the leading security training providers in the world. With the help of our highly educated and trained instructors, you may earn prestigious ISC2 SSCP certifications. This training course will teach you how to identify risks for IT firms to build plans to mitigate possible threats before they occur.







 1800-843-7890 (India)
1800-843-7890 (India)