Exploring SSCP Domain 5: Cryptography for a Career in IT Security
The ability to securely store and communicate sensitive data has proven to be a vital aspect of all firms’ success. Cryptography is the process of protecting data using techniques that ensure its integrity, secrecy, validity, and non-repudiation and the recovery of encrypted data in its original form. This article will cover the fifth domain of SSCP: Cryptography and what you can expect in the SSCP exam from this domain.

Domains of SSCP
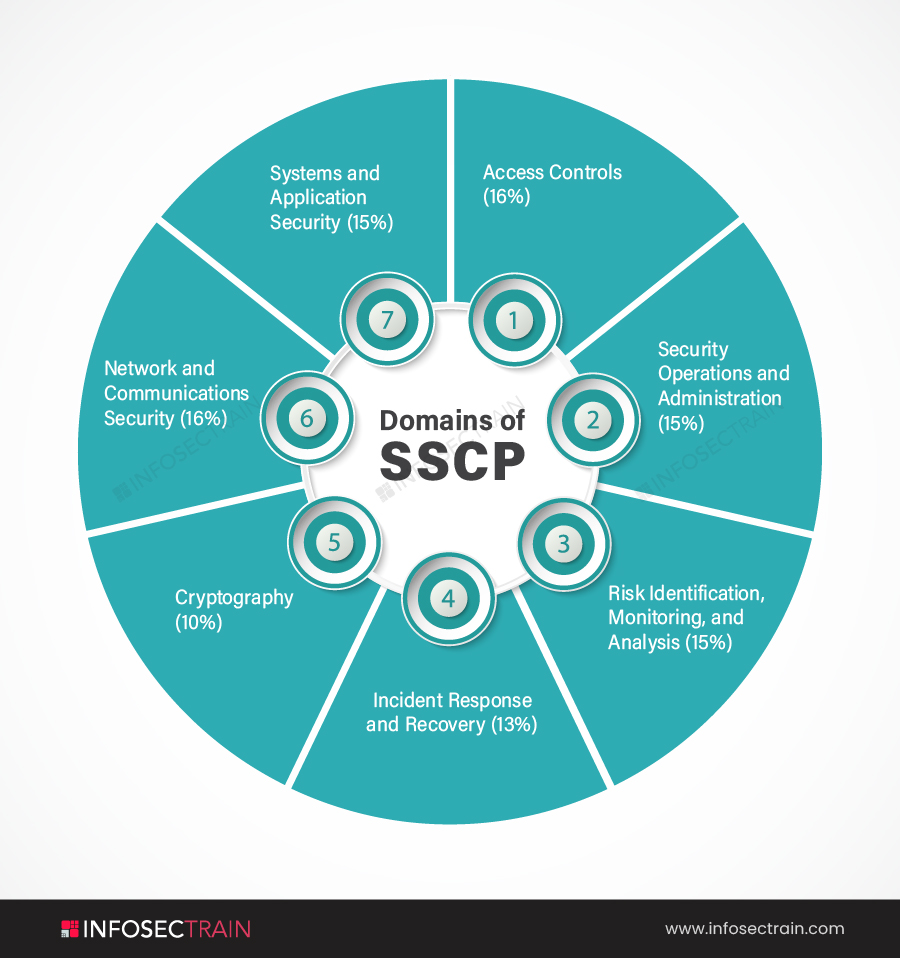
The seven SSCP domains are:
- Domain 1: Access Controls (16%)
- Domain 2: Security Operations and Administration (15%)
- Domain 3: Risk Identification, Monitoring, and Analysis (15%)
- Domain 4: Incident Response and Recovery (13%)
- Domain 5: Cryptography (10%)
- Domain 6: Network and Communications Security (16%)
- Domain 7: Systems and Application Security (15%)
Domain 5: Cryptography
Domain 5 of the SSCP certification exam is Cryptography. The Cryptography domain comprises a weightage of 10% in the Systems Security Certified Practitioner (SSCP) certification exam. This domain will overview the concepts and requirements of confidentiality and how to achieve it with cryptographic methods. Confidentiality is a crucial responsibility of all IT security personnel. This section will go over cryptographic techniques, key usage, and the different types of cryptographic systems. You will learn that public-key infrastructure is used every time someone logs into an e-commerce site. It will go through how to use digital certificates, ensure data integrity, and what techniques can be used to safeguard data while at rest or in transit. The domain will teach how to use cryptographic measures to give authentication. It will also cover non-repudiation to assure that the sender of a message cannot deny that they sent it. The subtopics covered in the Cryptography domain are:
- Understand fundamental concepts of cryptography
- Understand reasons and requirements for cryptography
- Understand and support secure protocols
- Understand Public Key Infrastructure (PKI) systems
1. Understand Fundamental Concepts of Cryptography
This subsection will provide an overview of the fundamental terms and concepts of cryptography. Cryptography is the practice and study of ways for securing communications while third parties are present. It will address encryption techniques for securing sensitive data, ensuring data integrity and authenticity, and establishing non-repudiation and proof of message origin. It will cover the difference between hashing and encryption and go over symmetric and asymmetric cryptography. It covers the two basic encryption methods, symmetric and asymmetric encryption. It will teach about how various cryptographic algorithms work and how RSA works. It will also cover multiple terms such as non-repudiation, digital signatures, digital certificates, and proof of origin. The section will also go over cryptographic attacks, concepts of cryptanalysis, and countermeasures to protect sensitive data from unauthorized access.
2. Understand Reasons and Requirements for Cryptography
This subsection will cover data confidentiality, integrity, and availability, as well as authenticity and non-repudiation. A secure system should guarantee these. Cryptography can assist in providing these assurances when utilized effectively. Data in transit and data at rest are protected by cryptography, ensuring their confidentiality and integrity. It will also teach about using cryptography to protect against repudiation by establishing trust between senders and recipients. This section will discuss how an unauthorized exposure of that information would affect any organization’s confidentiality, integrity, or availability. Sensitive data is confidential data that must be kept safe and out of the hands of anyone who does not have the authorization to see it. This section will also address cryptography regulations designed to protect individuals and organizations from having their personal information shared without their permission.
3. Understand and Support Secure Protocols
This subsection will cover various services and protocols to secure data. A secure protocol is a set of operations that ensures data security. The section will discuss how cryptographic protocols like SSL/TLS protect communications from harmful eavesdropping and tampering by providing confidentiality and integrity guarantees. The area will cover common use cases. It will also cover various limitations and vulnerabilities of the services and protocols used in cryptography.
4. Understand Public Key Infrastructure (PKI) Systems
This subsection will go over fundamental key management concepts, key administration and validation, and Public Key Infrastructure (PKI) systems. The control of cryptographic keys is referred to as key management in a cryptosystem. It covers the key generation, exchange, storage, use, crypto-shredding (destruction), and replacement. Cryptographic protocol design, key servers, user procedures, and other vital protocols are also covered. This section will also go over the Web of Trust (WOT) to help determine which websites are safe or not. WOT will protect from frauds, malware, phishing, and identity theft. It will cover Pretty Good Privacy (PGP), Gnu Privacy Guard (GPG), and more.
SSCP with InfosecTrain
Enroll in the SSCP certification training course at InfosecTrain. We are one of the leading security training providers in the world. With the help of our highly educated and trained instructors, you may earn prestigious (ISC)2 SSCP certifications. This SSCP training course will teach you how to use cryptography to help secure any individuals or sensitive organizational data, various protocols, cryptographic laws involved, and more.







 1800-843-7890 (India)
1800-843-7890 (India)