Exploring SSCP Domain 6: Network and Communications Security for a Career in IT Security
An effective network and communications security solution lower the danger of data theft and sabotage in the workplace. Protecting your workstations from spyware is more accessible with network security. It also ensures the security of shared information. A cybersecurity professional’s job includes a substantial amount of network and communications security. This article will cover the sixth domain of SSCP: Network and Communications Security, and what you can expect in the SSCP exam from this domain.

Domains of SSCP
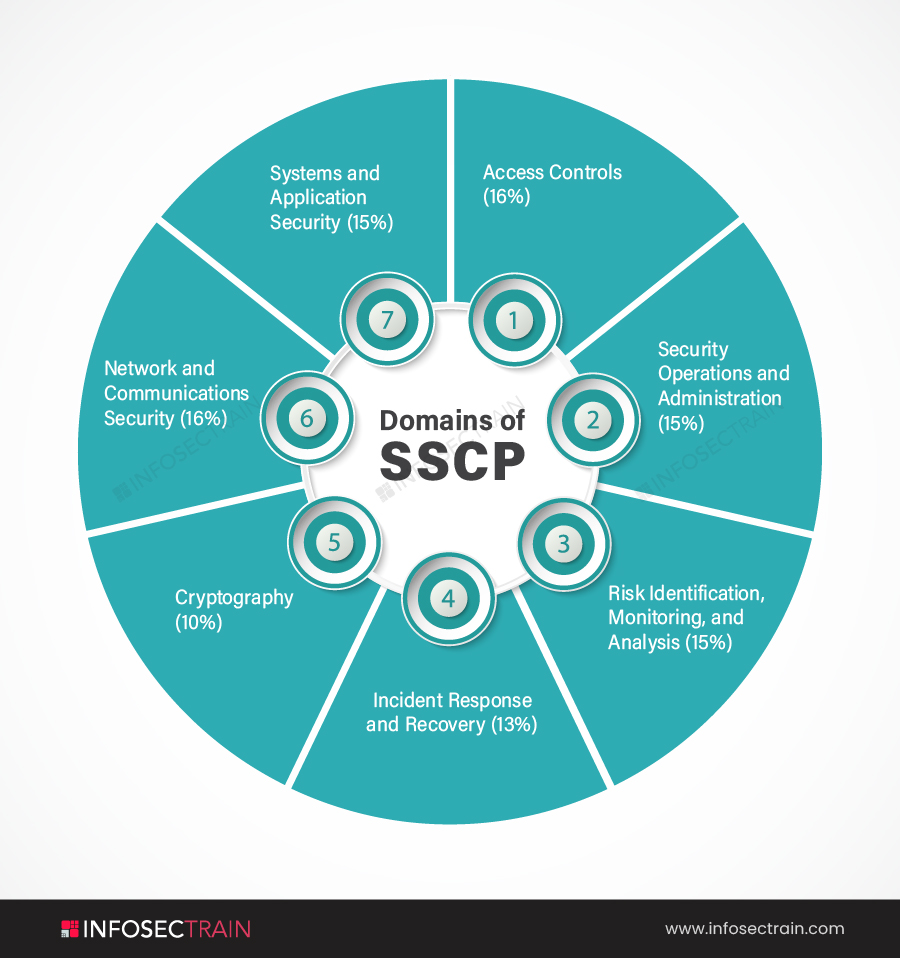
The seven SSCP domains are:
- Domain 1: Access Controls (16%)
- Domain 2: Security Operations and Administration (15%)
- Domain 3: Risk Identification, Monitoring, and Analysis (15%)
- Domain 4: Incident Response and Recovery (13%)
- Domain 5: Cryptography (10%)
- Domain 6: Network and Communications Security (16%)
- Domain 7: Systems and Application Security (15%)
Domain 6: Network and Communications Security
Domain 6 of the SSCP certification exam is Network and Communications Security. The Network and Communications Security domain comprise a weightage of 16% in the SSCP certification exam. This domain will introduce network models and hardware devices and the structure of data that flows over and through these devices. IT networks are composed of various hardware devices put together in different ways to form topologies, which are network models. Network devices use telecommunications signaling systems to transmit data between users and through devices. This area will cover wireless and cellular technology, the Bring Your Own Device concept and connecting personal digital devices to the workplace network. It will also cover convergent network communications, such as voice and media across a digital network, and the prioritizing of data that travels across a network. The subtopics covered in Network and Communications Security domain are:
- Understand and apply fundamental concepts of networking
- Understand network attacks and countermeasures
- Manage network access controls
- Manage network security
- Operate and configure network-based security devices
- Operate and configure wireless technologies
1. Understand and Apply Fundamental Concepts of Networking
This subsection will provide in-depth knowledge of the fundamental concepts of networking and introduce the design and implementation of network devices, protocols, and telecommunication services to transfer data through public and private networks. It will discuss the VPN technologies, OSI and TCP/IP models, and other related protocols in-depth. This subsection will look at network topologies and the different topologies, such as star, bus, and ring. Firewalls, routers, switches, gateways, and proxies are part of network hardware and access points. It will also cover the different data transmission media types such as fiber optic, coaxial, twisted-pair cable, etc., and the commonly used ports and protocols.
2. Understand Network Attacks and Countermeasures
This subsection will go over how to set up network security devices and recognize various forms of network attacks. This section will discuss the methods for preventing network-based attacks, detecting intrusions, and employing countermeasures that may be required to combat such attacks. This section will also cover ARP, brute force, worms, flooding, eavesdropping, sniffers, spamming, Dos/DDOS, and Spoofing.
3. Manage Network Access Controls
This subsection will explain the various network access control systems and how they should be managed and used to safeguard the system and data utilizing various confidentiality, integrity, and availability levels. It will cover the different network access control standards and protocols. This section will address understanding and working with remote access technologies, including RADIUS and TACACS, and basic network theory and operating information. This section also covers essential security functions such as email security and the use of NAT and VPNs.
4. Manage Network Security
This subsection will discuss the security measures used to ensure the integrity, availability, authentication, and confidentiality of the transmitted or communicated data. This section will cover the many methods of providing network services and the security that comes with them. Some are Frame Relay, X.25, ISDN, Synchronous Data Link Control (SDLC), and High-Level Data Link Control (HDLC). It will go over the physical and logical placement of network devices concerned with the transmission of data. It will also cover various segmentations such as VLAN, ACLs, and more. You will learn the advantages of VLAN and how to implement VLAN. This section will also discuss secure device management.
5. Operate and Configure Network-Based Security Devices
In this part, you will learn how to secure your network with firewall rules, switch and router configuration, network monitoring, and how to protect your telecommunications and comprehend the specific features and weaknesses of wireless networks. This section will go over the concepts of firewall and proxies implementations. This section will cover network intrusion detection and prevention systems. It will discuss Port Scanning, TCP Sequence Number Attacks, Network Security Tools and Tasks, Intrusion Detection Systems (IDS), Architecture of an Intrusion Detection System (IDS), Security Event Management (SEM)/Security Event and Incident Management (SEIM), Scanners, Discovery Scanning, Compliance Scanning, Vulnerability Scanning, and Penetration Testing, Scanning Tools, and Network Taps. It will also cover traffic-shaping devices.
6. Operate and Configure Wireless Technologies
This subsection will discuss transmission security in-depth. It will go over the wireless and cellular technologies, the procedures to set up and operate wireless technologies, transmission security, common vulnerabilities and countermeasures, and different wireless security issues. It will also cover Open System Authentication, Shared Key Authentication, Ad Hoc mode, infrastructure mode, Wired Equivalent Privacy Protocol (WEP), WiFi Protected Access (WPA) and WiFi Protected Access 2 (WPA2), A “Parking Lot” Attack, Shared Key Authentication Flaw, Service Set Identifier (SSID) Flaw, Vulnerability of Wired Equivalent Privacy Protocol (WEP), and wireless devices.
SSCP with InfosecTrain
Enroll in the SSCP certification training course at InfosecTrain. We are one of the leading security training providers in the world. With the help of our highly educated and trained instructors, you may earn prestigious ISC² SSCP certifications. You will be able to define and identify the networks and communications security required to secure network structure, data transmission methods, transport formats, and the security measures employed to maintain the integrity, availability, authentication, and confidentiality of the transmitted data after completing the SSCP certification training course.







 1800-843-7890 (India)
1800-843-7890 (India)