Exploring SSCP Domain 7: Systems and Application Security for a Career in IT Security
Malicious code refers to any code in any part of a software system designed to create unwanted effects, security breaches, or system harm. Malicious code is a hazard to application security that cannot be effectively handled by traditional antivirus software alone, necessitating more robust security measures. The Systems and Application Security domain are concerned with various countermeasures for various types of malware or malicious code that cause security breaches. This article will cover the seventh domain of SSCP: Network and Communications Security, and what you can expect in the SSCP exam from this domain.

Domains of SSCP
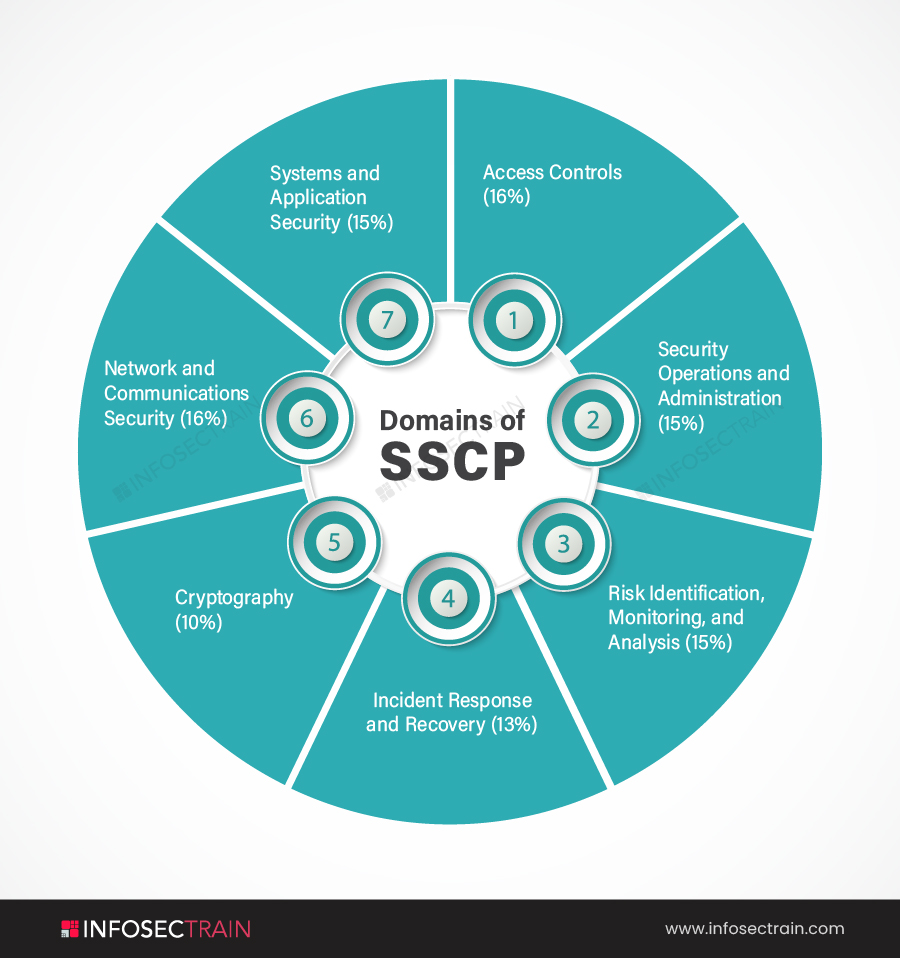
The seven SSCP domains are:
- Domain 1: Access Controls (16%)
- Domain 2: Security Operations and Administration (15%)
- Domain 3: Risk Identification, Monitoring, and Analysis (15%)
- Domain 4: Incident Response and Recovery (13%)
- Domain 5: Cryptography (10%)
- Domain 6: Network and Communications Security (16%)
- Domain 7: Systems and Application Security (15%)
Domain 7: Systems and Application Security
Domain 7 of the SSCP certification exam is Systems and Application Security. The Systems and Application Security domain comprise 15% of the total weightage in the SSCP certification exam. This domain will introduce the necessity of securing endpoints from various malicious code attacks and how to use various countermeasures to lessen endpoint threats. Endpoints, such as host workstations, digital wireless devices, printers, scanners, and point-of-sale equipment, form the termination point of a network connection. This domain will also discuss implementing controls and countermeasures to identify and prevent malicious code from attacking the network and its hosts. The subtopics covered in the Systems and Application Security domain are:
- Identify and analyze malicious code and activity
- Implement and operate endpoint device security
- Operate and configure cloud security
- Operate and secure virtual environments
1. Identify and Analyze Malicious Code and Activity
This subsection will provide in-depth knowledge of malicious codes and malware and the various countermeasures like scanners, anti-malware, code signing, sandboxing, and more. This section teaches how to detect and identify malware and computer code that could compromise an organization’s IT systems. It also covers techniques for introducing these variants into systems and tools and processes for limiting exposure to this type of behavior, including user training to aid their efforts. It will discuss exploitation, insider threats, spoofing, phishing, spam, and botnets, as well as malicious web activity, payloads, malcode mitigation, and frequent mistakes. This domain will also discuss malicious activity countermeasures such as user awareness, system hardening, patching, sandboxing, isolation.
2. Implement and Operate Endpoint Device Security
This subsection will describe endpoint device security in detail and the processes to operate it. Today’s endpoint security systems are built to identify, assess, block quickly, and contain active attacks. Endpoint security is the technique of preventing malicious actors and threats from attacking entry points or endpoints of an end-user device such as desktops, laptops, and smartphones. The section will also cover the Mobile Device Management (MDM) process such as COPE, BYOD. It will discuss the benefits and drawbacks of Host-Based Intrusion Detection Systems (HIDS). The section will also cover various topics like host-based firewalls, application whitelisting, endpoint encryption, Trusted Platform Module (TPM), Mobile Device Management (MDM), and Secure Browsing.
3. Operate and Configure Cloud Security
This subsection will discuss the process for configuring cloud security. This section covers an introduction to the five essential characteristics of clouds, cloud deployment, and service models. It will cover virtualization and its different types. The area will also discuss the country-related legal and privacy concerns. The section will classify discovered sensitive data, mapping, the definition of controls, application of defined controls for Personally Identifiable Information (PII). It will also cover data storage and transmission, encryption, key management, masking/obfuscation and anonymization, data deletion procedures and mechanisms, and more. Lastly, the section will explain the shared responsibility model.
4. Operate and Secure Virtual Environments
This subsection will explain the process for securing virtual environments and big data systems. Virtualization allows users to share a single physical instance of any resource across several machines. Virtualization is a method by which we create a virtual environment of storage devices and server operating systems. This section will go through the Software-Defined Network (SDN) and how it works, virtual appliances, continuity and resilience, attacks and countermeasures, common virtualization attacks, secure virtualization recommendations, and best practices, and shared storage.
SSCP with InfosecTrain
Enroll in the SSCP certification training course at InfosecTrain. We are one of the leading security training providers in the world. With the help of our highly educated and trained instructors, you may earn prestigious (ISC)2 SSCP certifications. The SSCP certification training course will teach you about harmful or malicious computer code and how to defend your company from it, as well as endpoint device security, cloud infrastructure security, securing big data platforms, and securing virtual environments.







 1800-843-7890 (India)
1800-843-7890 (India)