Firewall Testing with Hping3: A Comprehensive Guide
Firewalls serve as the first line of defense in network security, filtering and controlling incoming and outgoing traffic based on predetermined security rules. However, even the most robust firewall configurations can have vulnerabilities. Hping3, a powerful open-source network tool, allows Ethical Hackers and Penetration Testers to assess firewall security by generating TCP, UDP, and ICMP packets with custom parameters.

This guide provides a step-by-step method for utilizing Hping3 for firewall testing.
Understanding Hping3
Hping3 is a command-line packet generator and analyzer for the TCP/IP protocol. Unlike traditional ping utilities, Hping3 supports TCP, UDP, and ICMP, allowing testers to craft customized packets for detailed firewall and intrusion detection testing.
Features of Hping3
- Packet crafting for TCP, UDP, ICMP, and raw IP protocols
- Ability to modify source/destination IP addresses and ports
- Stateful and stateless firewall testing
- Traceroute functionality with customizable flags
- Port scanning and packet fragmentation
- TCP/IP fingerprinting
- Test firewall rules and IDS/IPS behavior
- Conduct DoS testing in a controlled environment
Step-by-Step Guide to Firewall Testing with Hping3
Installation
Hping3 is available for Linux and Windows (via Cygwin). Install it using:
| sudo apt update && sudo apt install hping3 sudo yum install hping3 |

For Windows, use Cygwin or a Linux VM.
Firewall Testing Techniques with Hping3
The target is elm.sa.
1. Basic Ping Scan
Most firewalls block standard ICMP requests. Use Hping3 to check if a host is responding:
| hping3 -1 elm.sa -c 4 |
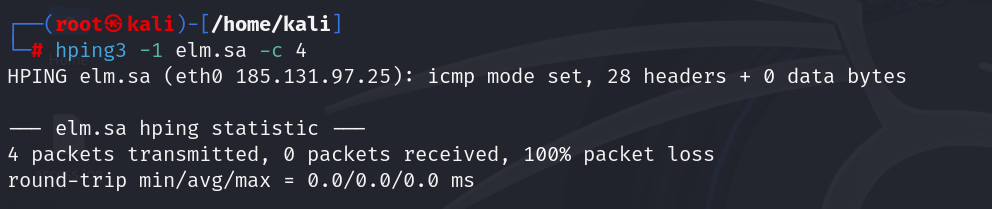
Parameters:
- -1: Uses ICMP (ping mode)
- -c: count
Result: If no response is received, the firewall is likely blocking ICMP echo requests.
2. TCP SYN Scan
SYN scans help identify open ports while avoiding detection by some logging mechanisms.
| hping3 -S elm.sa -p 80 -c 3 |

Parameters:
- -S: Sends SYN (connection request) packets
- -p 80: Targets port 80 (HTTP)
Result:
- If a SYN-ACK is received, the port is open.
- If a RST-ACK is received, the port is closed.
- No response might indicate packet filtering.
3. Stealth Scan (FIN Scan)
To check if the firewall blocks FIN packets:
| hping3 -F -p 80 elm.sa |

Parameters:
- -F: Sends FIN (finish) packets
Results:
- Firewalls may ignore FIN packets, but if a RST-ACK is received, the port is closed.
4. ACK Scan for Firewall Rule Detection
To test firewall rule sets:
| hping3 -A -p 80 elm.sa |

Parameters:
- -A: Sends ACK packets
Result:
- If no response is received, the firewall will filter packets.
- If a RST response is received, the port is unfiltered but closed.
5. UDP Scan
Since UDP is connectionless, firewalls often block or restrict UDP traffic. Test with:
| hping3 –udp -p 53 elm.sa |
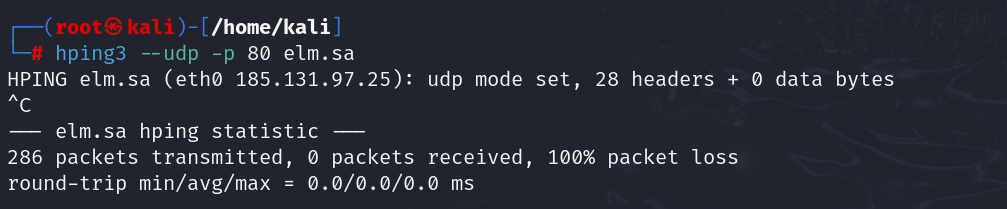
Parameters:
- –udp: Uses UDP packets
- -p 53: Targets port 53 (DNS)
Result:
- If no response is received, the firewall will block UDP.
- If an ICMP “port unreachable” is returned, the port is closed.
6. Testing Stateful vs. Stateless Firewalls
A stateful firewall tracks connection states, while a stateless firewall filters based on predefined rules. To determine firewall behavior:
| hping3 -S elm.sa -p 80 –fast |

Parameters:
- –fast: Sends packets faster for quicker testing
Result:
- If responses differ when sent in sequence, the firewall is stateful.
- Consistent responses: Firewall is stateless
7. Fragmented Packet Attack Simulation
Firewalls should reassemble fragmented packets, but some misconfigurations allow evasion:
| hping3 -S elm.sa -p 80 -f |
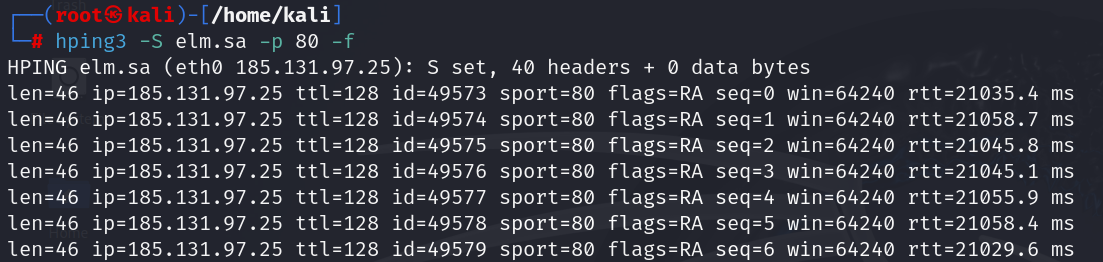
Parameters:
- -f: Sends fragmented packets
Result: If fragmented packets bypass filtering, the firewall may be misconfigured.
8. Spoofed Source IP Testing
To test if the firewall relies on simple source-based filtering:
| hping3 -S elm.sa -a -p 80 |
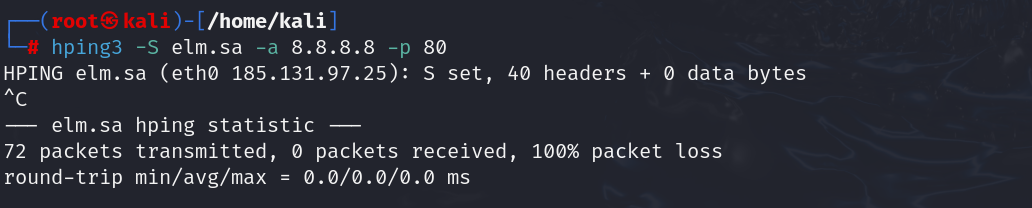
Parameters:
- -a <fake_IP>: Spoofs the source IP address
Result: If a response is received, the firewall allows spoofed traffic.
9. Testing IDS/IPS Behavior
Intrusion Detection and Prevention Systems (IDS/IPS) analyze traffic patterns and detect anomalies. Use Hping3 to evaluate their effectiveness:
| hping3 -S elm.sa -p 80 –rand-source –flood |
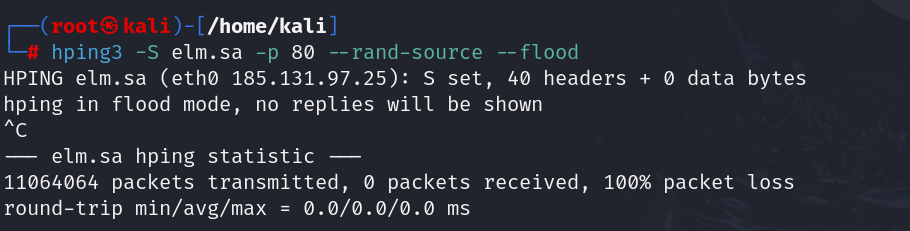
Parameters:
- –rand-source: Sends packets from random source IPs
- –flood: Sends packets continuously (DoS attack simulation)
Result:
- If alerts are generated, the IDS/IPS will function properly.
- If not, it may require tuning.
10. Conducting DoS Testing in a Controlled Environment
Simulating Denial-of-Service (DoS) attacks help assess how well firewalls mitigate excessive traffic. Controlled DoS tests can be performed using:
| hping3 –flood –rand-source -S elm.sa -p 443 |
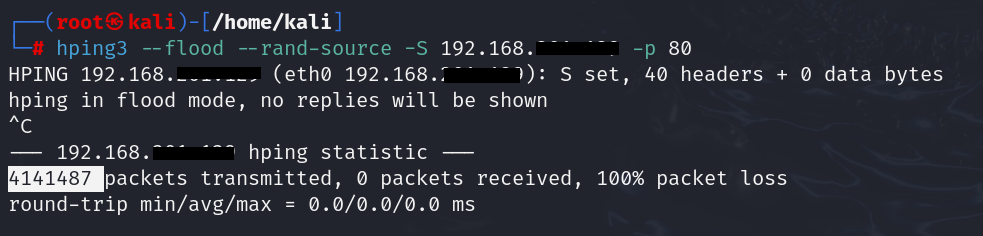
Parameters:
- –flood: Generates a high packet rate
- –rand-source: Randomizes source IPs
- -p 443: Targets port 443 (HTTPS)
Use this command cautiously and only in a lab environment with permission.
Here, performing DOS attack on 192.168.xxx.xxx in controlled environment from kali machine.
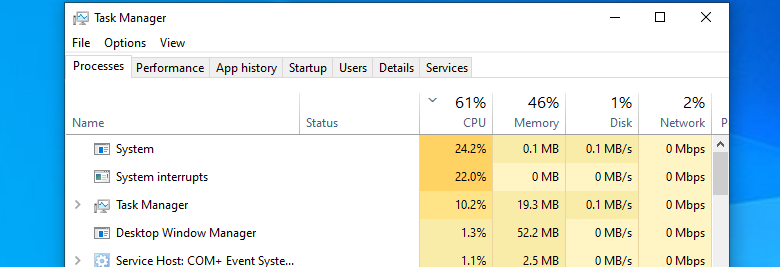
The victim system is getting sluggish here.
Analyzing Firewall Responses
Interpreting responses from Hping3 scans helps in determining firewall behavior:
| Response | Interpretation |
| No response | Packet dropped (Firewall or host not responding) |
| RST-ACK | Port closed but reachable |
| SYN-ACK | Port open |
| ICMP “port unreachable” | UDP port closed |
| Fragmentation allowed | Possible firewall misconfiguration |
Conclusion
Hping3 is an essential tool for Ethical Hackers and Penetration Testers to assess firewall security. By using various scanning techniques, security professionals can identify vulnerabilities and improve firewall configurations.
By mastering Hping3, you can enhance your ability to detect and remediate security gaps, making networks more resilient against potential threats.
Check out other related articles:
- Step-by-Step Guide for theHarvester Tool
- Steps for Effective DNS Footprinting
- The Ultimate Guide to SMTP and DNS Enumeration Practices
- Web Vulnerability Scanning with Nikto
- Mastering Network Discovery with Nmap: A Step-by-Step Guide
- What is Metasploit: A Practical Guide for Penetration Tester
- Shell GPT: A Practical Walkthrough
- Shodan: Information Gathering Tool
CEH v13 AI Certification Training with InfosecTrain
InfosecTrain‘s CEH v13 AI Certification Training provides hands-on learning of Hping3, a powerful packet crafting and firewall testing tool used in ethical hacking. With expert-led training, real-world labs, and AI-driven security insights, learners gain practical experience in assessing network defenses and detecting vulnerabilities. The training ensures cybersecurity professionals master Hping3 for ethical hacking, intrusion detection, and network security assessments effectively.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Jul-2025 | 31-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 16-Aug-2025 | 28-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |

 1800-843-7890 (India)
1800-843-7890 (India)