Fundamental Principles of Information Security
Information security is crucial in today’s digital world to guard against threats like unauthorized access, misuse, or data loss. The fundamental principles of information security form the basis of a robust security strategy, encompassing best practices, methodologies, and techniques to safeguard critical information. This article explores key concepts that establish a resilient security foundation, from least privilege to encryption and access controls. These guidelines, which stress the need for a security-conscious culture, give businesses the tools they need to protect themselves from constantly changing threats and maintain the privacy, authenticity, and accessibility of their most valued data.

Table of Contents
What is Information Security?
Information Security vs. Cybersecurity
Principles of Information Security
What is Information Security?
Security is simply the state of being risk-free and protected. In essence, information security is safeguarding something or someone’s information. We can say information security is safeguarding a company’s information assets against all sorts of threats.
When creating an information security policy for the organization, we want to protect our organization’s information, keeping it safe from unwanted access and exploitation while granting access to the appropriate personnel. Users also want to protect their information from unwanted modification or deletion. The key elements of information security are confidentiality, integrity, and availability, which aid in protecting and preserving the organization’s information.
Information Security vs. Cybersecurity
Although the terms information security and cybersecurity are synonymous, they are not the same thing. Cybersecurity is a strategy used to protect against cyber threats, whereas information security is a broader term encompassing cybersecurity. Cybersecurity stand for protecting digital asset, and information security stands for protecting all kind of information and asset
Principles of Information Security
Three essential principles govern information security or three perspectives through which to view information security. The CIA Triad of information security consists of confidentiality, integrity, and availability.
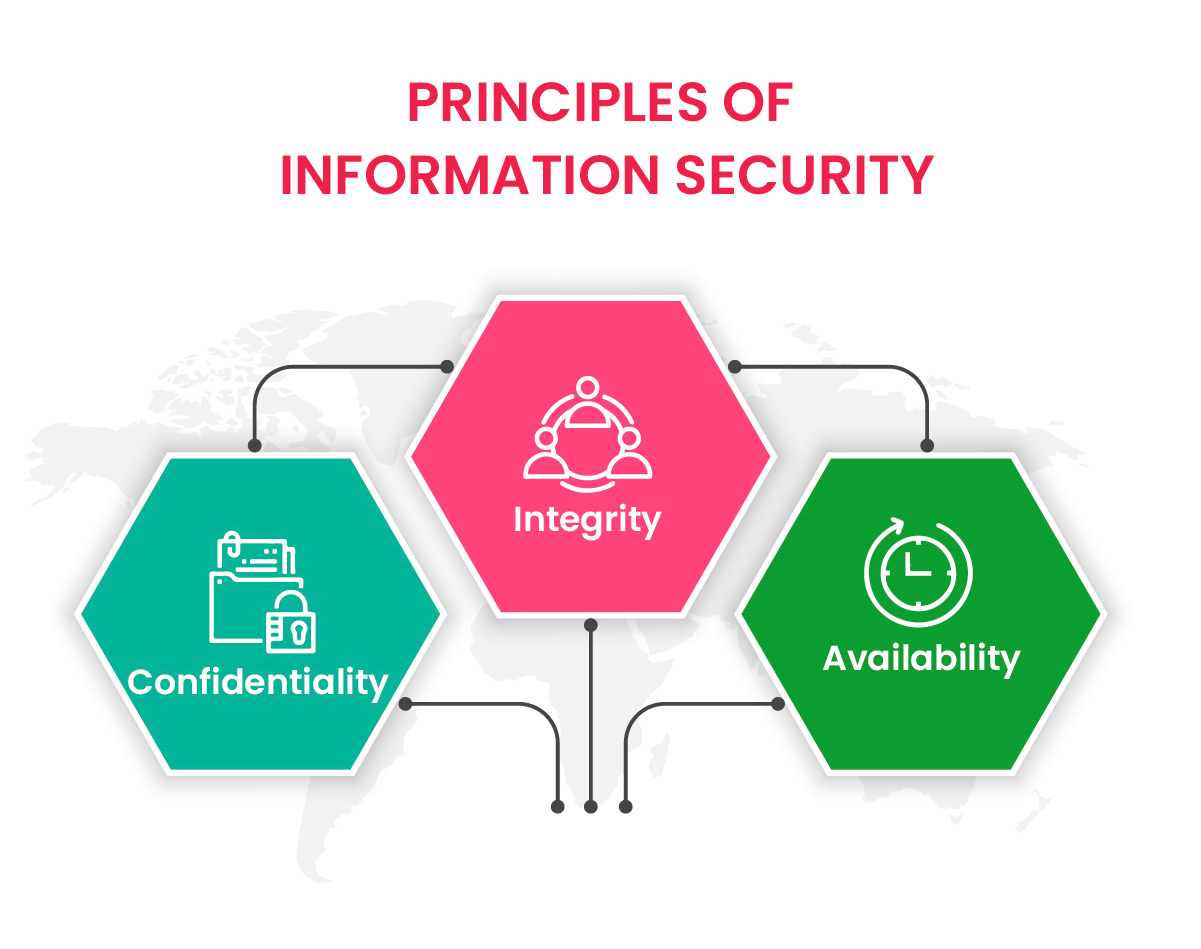
1. Confidentiality
The main concern of confidentiality is privacy, and the main objective of this principle is to keep information secure and only available to those who are authorized to access it. Unauthorized people must be kept from the data, which is accomplished by verifying the authorization of each individual who attempts to access the information. This requires putting in place some form of protection to maintain confidentiality. Among these controls are:
- Identification
- Authentication
- Authorization
- Encryption
Establish these measures to preserve the privacy of the data. What happens if the principle of confidentiality is violated? One potential scenario is a compromise of the information or data. When there are no precautions or restrictions to protect the information, anyone without authorization can readily access it. A hacker could access the system, extract Personally Identifiable Information (PII), and distribute it to others. A breach can harm your business in several ways, but the most obvious is financial. In actuality, a breach costs an average of $3.9 million.
2. Integrity
Accidents can occur, and authorized individuals can occasionally unintentionally change or delete data. According to the integrity principle, you should take precautions to avoid these mistakes and put systems in place to check the data’s accuracy. Integrity is maintained when the data is unaltered or, more accurately, not changed by any unauthorized entity. Thus, the information can be accessed when maintaining closed eyes.
Integrity and confidentiality go hand in hand. If unauthorized people can not access the information, they can not change it. Protection of the integrity of information or data may require additional procedures. While backup controls enable you to restore access to destroyed information, audit logs let you know who has changed a piece of information.
3. Availability
You do not want unauthorized users to access your data but authorized individuals to have access to it. Set up access control for the right people and train them on security measures so they can assist you in keeping the information secure. This feature allows authorized persons to access and modify the information within a specified time frame. The important aspect to remember here is that information is not easily accessible, and every organization has a unique time frame for when it can be accessible. Some of the factors that influence availability are as follows:
- Where to access the information: Depending on the time and location, different data may be accessible. A user might need to be physically present at an office building owned by the organization or in a specific nation to access a particular spreadsheet.
- How information can be accessed: User credentials or information provided by the user may affect how they access it. For example, someone can use two-way factor authentication to log in, requiring a username and password.
- When information can be accessed: Setting temporal limits for information may be essential. A temporary employee may only have access to a document for the duration of their employment. A vendor may have access to a video only while working on a project with the organization.
ISO 27001 with InfosecTrain
Organizations can prevent security threats and safeguard their brand by obtaining the crucial ISO 27001 certification. InfosecTrain is a well-known provider of IT security training. If you want to gain the knowledge to pass the ISO/IEC 27001:2022 Lead Auditor certification exam, join InfosecTrain’s ISO 27001 certification training courses.
TRAINING CALENDAR of Upcoming Batches For ISO 27001 : 2022 LA
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 26-Jul-2025 | 31-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 23-Aug-2025 | 21-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |






 1800-843-7890 (India)
1800-843-7890 (India)