How to Become a Security Architect?
As we celebrate technological advancements, organizations lacking security are like a golden goose for the nefarious elements of the cyber world. Getting started with a security adventure is a great career choice if you are accessorized with the right skills. You’re heading in the right direction if you’re eyeing the Security Architect profile.

Security Architect
Security Architects evaluate the information infrastructure and computer systems in their organizations, defining strengths and limitations. On Local Area Networks (LAN), Wide Area Networks (WAN), and Virtual Private Networks (VPN), they perform penetration tests and risk assessments. They also test the effectiveness and reliability of routers, firewalls, and similar systems.
Security Architects have to consider themselves to be hackers and think like them to find the possible threats and flaws in an organization’s security posture. They test the limits of current computer and network security systems. Security Architects design and execute architectural improvements to improve security structures after identifying flaws in existing systems. These experts also design and implement utterly new security architectures. They incorporate their understanding of security hardware and software, organizational needs, and cybersecurity threats with company policies and industry standards.
Security Architect Career
If you want to become a Security Architect, you must start the career path by getting a Bachelor’s degree in Information Technology, Computer Science, Cybersecurity, or a closely related field. Alternatively, you can gain comparable expertise by obtaining appropriate industry certifications. You can become a Security Administrator, Systems Administrator, or Network Administrator in the IT field, and you can enter the Security Architect domain.
How to become a Security Architect?
Rome was not built in a day, so, the same way, you cannot become a Security Architect overnight. Being a Security Architect means being a true generalist of all security positions. In a business, a Security Architect has both strategic and tactical responsibilities. But how to become a Security Architect?
Well, it’s not so tricky, but the second you’ll assume that you know everything is the second you’re heading for crash landings, and you may end up missing a vulnerability. To become a Security Architect and excel in your career, you must have some knowledge, understanding, and certifications. Taking the little steps is very crucial. Here are some little steps that you must take into account:
- It would help if you first gained a general understanding of technology.
- The security architect must be familiar with all of the different security solutions that are implemented in a company.
- To determine if a company is in compliance, you must first understand what it means to have an audit framework and processes.
- You must also be familiar with the various security procedures, ranging from incident response to disaster recovery.
- It would help if you comprehended how a SAN (Storage Area Network) interacts with multiple applications.
- You must understand how an application is planned and constructed.
- If a new Operating System is about to be released, you must be aware of the enhancements that will be available as well as their effect on your organization.
- To investigate Firewalls and Intrusion Prevention Systems, you must first understand networking.
- Since security is more of a quality management practice, you must also consider all aspects of business outside of security.
- If you want to keep a project under budget, you’ll need to know how to read financial statements.
Certification path
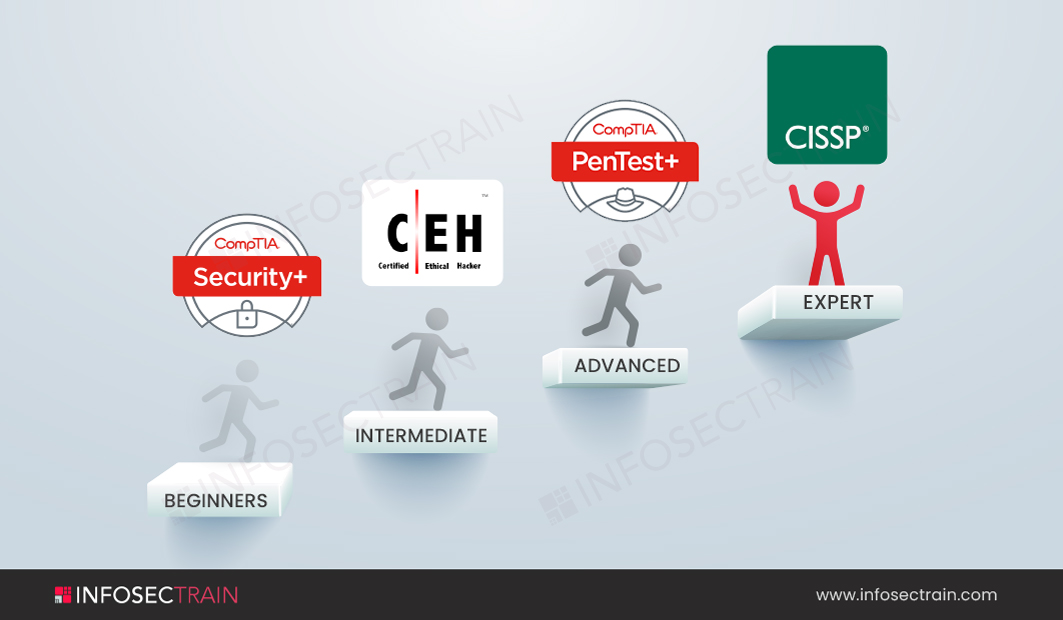
- Beginner Level Certification: You can begin the journey towards becoming a Security Architect by completing the CompTIA Security+ certification. CompTIA Security+ is the most recent edition of the exam that certifies cybersecurity professionals’ basic technical skills. Candidates can learn about the most recent threats, assaults, and vulnerabilities, risk reduction principles, how to architect a stable hybrid environment, incident response and governance, and compliance.

- Intermediate Level Certification: Once you have completed the beginner level certification, you can move to the intermediate level that is the Certified Ethical Hacker (CEH) certification. The EC-Council Certified Ethical Hacker credential verifies your knowledge of core security concepts. It provides you two of the most highly sought-after security designations: Certified Ethical Hacker and Penetration Tester. This globally recognized security credential verifies the ability to spot flaws in a company’s network infrastructure and effectively defend against cyber-attacks.

- Advanced Level Certification: Then comes the advanced level that is the CompTIA PenTest+ certification. CompTIA’s PenTest Advanced certification is based on penetration testing, management abilities, and the ability to gain hands-on experience in cloud, desktop, and server environments. From a business standpoint, the training covers vulnerability assessment management and penetration testing.
- Expert Level Certification: Last but not least is the advanced level that is Certified Information Systems Security Professional (CISSP) certification. By discussing the essential elements of the eight domains that make up a Common Body of Knowledge (CBK) for information systems security professionals, the CISSP certification will broaden your knowledge. The most well-known credential in the field of information security provides participants with in-demand technological and administrative skills for designing, architecting, and managing an organization’s security posture.







 1800-843-7890 (India)
1800-843-7890 (India)