How to Choose The Right Threat Modelling Methodology For Your Organization?
Cyber vulnerability of a website is the worst nightmare of those working in IT profession. To save their hard work and smartly fence an organization’s network, the professionals look up to Threat Modelling methodology. We all understand it well that a security breach is not only done by the software bug but even the smallest flaw in the architecture of the application can make us lose a lot. With the growth of technology, variety of threats is also growing. As per a survey, in the second quarter of 2018, there has been 151% growth of the malware that exploits software vulnerabilities. Based on this tremendous rise in the threats, experts have estimated that by 2021 the cost of Cyber Crime damage will reach $6 trillion. Thus, it is high time now that organization should start adapting Threat Modelling Methodology to protect themselves.

There are various Threat Modelling Methodologies and it is important for the organizations to recognize the right Methodology for their specific challenge.
Before I explain the various methodologies, let’s first quickly understand what is Threat Modelling Methodology?
It is basically an architectural risk analysis which is systematic method for analysing the security of an application. It is impossible to build a secure application without understanding the threats. The main reason to use Threat Modelling Methods are:
- to provide abstraction of the system
- to list the profiles of potential attackers along with their goals and methods
- to prepare the catalog of potential threats which might harm the network
When/Why to implement Threat Modelling?
With the immense development in the cybersecurity methods, security issues can be fixed at any stage of development, but it is always better to fix the issues right at the design phase. Finding and fixing security issues after delivery can be expensive both financially and for the reputation of the organization. Threat Modelling is beneficial in eliminating security vulnerabilities in the design phase. Although it is challenging and time taking to scan an existing software with Threat Modelling, but it is important to scan the software as using any software without threat modelling or security engineering is like allowing the bug in the system. Threat- Model in any organization must be up-to-date. Whenever there is a change in application, related technologies, threat landscape etc. it must be reviewed and updated by Threat Modelling. Thus, we can summarize that Threat modelling implementation is important –
- to find security flaws when there is time to fix them.
- to save time, revenue and the reputation of the organization.
- to build a secure application.
- to bridge the gap between developers and security.
- to provide a document of all the identified threats and rated threats.
- to get the knowledge and awareness of the latest risks and vulnerabilities.
There is continuous development in the field of Threat Modelling and so you cannot expect to rely upon one kind of Threat Model for a long time. A particular kind of Threat Model can not assure to provide security from all kinds of threats. There are many Threat Modelling Methods and at times they are combined together to create a stronger and better view of potential threats. Once Threat Modelling is performed on the applications, it would surely help in detecting the threat at the earliest possible and will also minimize the adverse impact of threat on the application. Here is a list of some of the common Threat Modelling Methods along with their characteristics which will certainly help you to understand your requirement of the Threat Model.
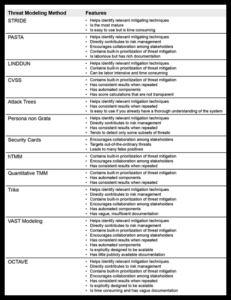
To Know more about the Threat Modelling Methodologies and other Cybersecurity Courses, you can visit the websites of InfosecTrain. It is one of the leading organisations to offer Cybersecurity solutions. It also offers training courses for various cybersecurity certifications. You can choose an online or regular training as per your convenience.






 1800-843-7890 (India)
1800-843-7890 (India)