How To Prevent Zero-Day Attacks?
Cybercrimes or cyberattacks are increasing rapidly with continually expanding IT services. These days, one of the most common attacks that a company experiences is a zero-day attack. Zero-day describes a situation in which security teams or security experts are unaware of software vulnerabilities and have “0” days to work on a security patch or upgrade to address the vulnerabilities. Suppose the software vulnerabilities are not promptly identified and resolved. In that case, they may have significant adverse effects on the business, including financial loss, data theft, the shutdown of operations, unauthorized access to the network or system, and damaged reputations.

The most prevalent systems that hackers can target with zero-day attacks are:
- Operating systems
- Hardware
- Internet of Things (IoT) devices
- Firmware
- Business SaaS
- Web browsers
- Open-source software
This blog will provide an overview of zero-day attacks and the methods to provide protection against zero-day attacks.
What is a Zero-Day attack?
A zero-day or a day-zero attack is an attack that exploits undisclosed security vulnerabilities for which no patches are available. It implies that hackers are aware of the software vulnerabilities before the software developer patches them and can deploy malware to take advantage of the software vulnerabilities.
Along with the zero-day attack, you should be aware of the zero-day vulnerability and zero-day exploit.
Zero-day vulnerability: A zero-day vulnerability is an undiscovered software vulnerability that hackers can use to launch attacks before the developer is unaware.
Zero-day exploit: Zero-day exploit is the method a hacker employs to attack a system using the zero-day vulnerability.
Zero-day attack prevention methods
Let us discuss some essential tips to protect against zero-day attacks.
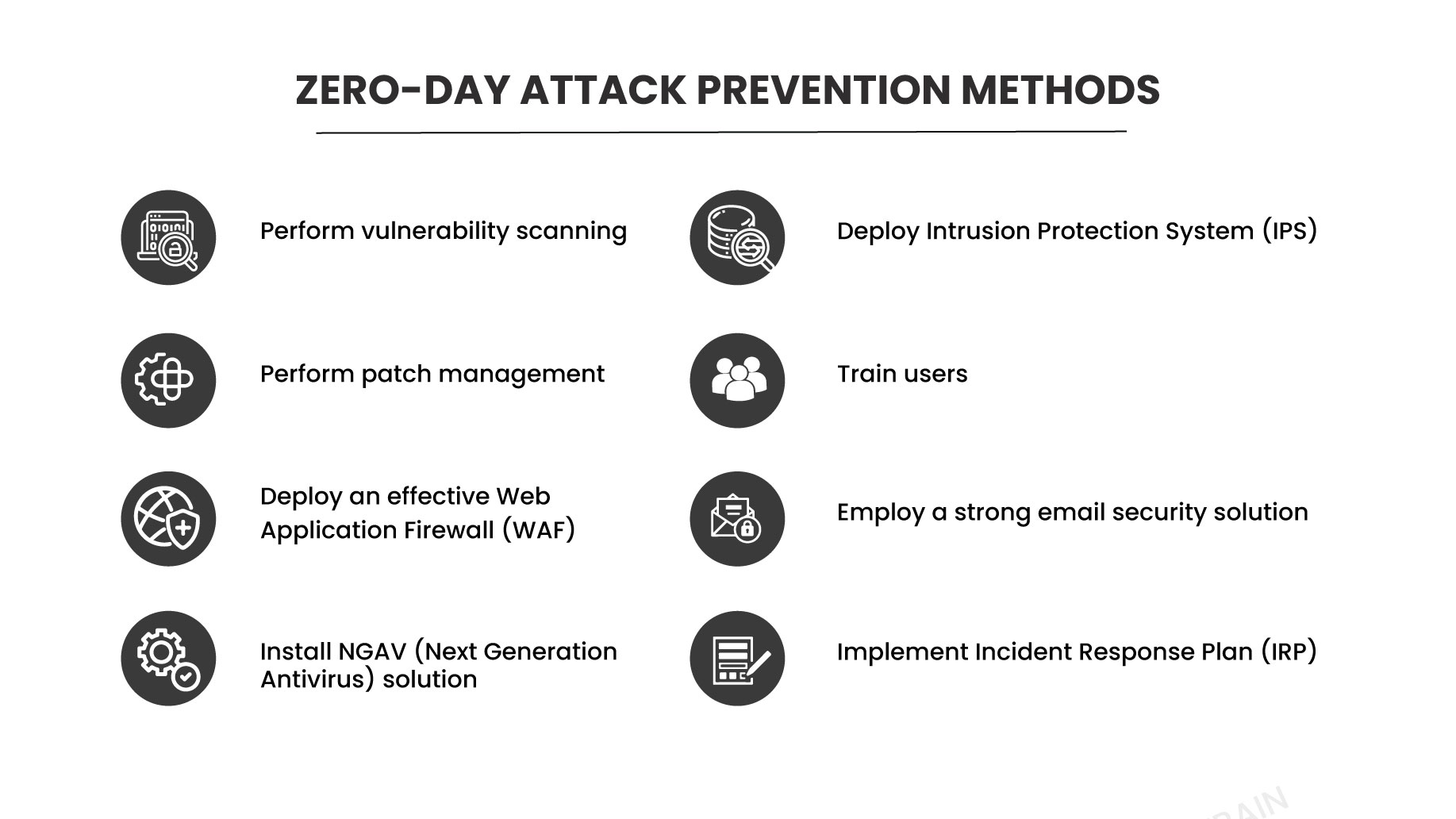
1. Perform vulnerability scanning
The most critical step to prevent the zero-day attack is to scan for vulnerabilities. With the aid of security professionals, who can simulate attacks on the software code and check code for flaws, vulnerability scanning helps to uncover zero-day exploits rapidly. It helps in identifying new security flaws, vulnerabilities, and security configuration errors in updated software. However, since this solution does not capture every zero-day attack, enterprises need to do code reviews and take prompt action after receiving the scan result to stop an exploit.
2. Perform patch management
After detecting the newly identified software vulnerabilities, businesses must install software patches as soon as possible to fix and reduce the risk of known security vulnerabilities. However, it cannot prevent zero-day attacks, but it can considerably reduce the risk of zero-day attacks. In the patch management process, it is crucial for businesses to rapidly and efficiently apply patches; otherwise, the longer this process takes, the risk of a zero-day attack increases.
3. Deploy an effective Web Application Firewall (WAF)
Deploy a powerful Web Application Firewall (WAF) (WAF) technology on the endpoints or network edge that can monitor, filter, and prevent incoming and outgoing HTTP/S traffic as well as block other malicious requests. It is crucial to defend your software or system from zero-day vulnerabilities. An effective WAF enables your company to respond to threats in real time and adapt quickly to stay updated with emerging threats.
4. Install Next-Generation Antivirus (NGAV) solution
Install the new and enhanced Next-Generation Antivirus (NGAV) solution to keep your systems safe and secure, as traditional antivirus software is inadequate against zero-day threats. It prevents attacks by monitoring and responding to hacker tactics, techniques, and procedures (TTP). It employs various cutting-edge techniques, including threat intelligence, machine learning, and behavioral analytics, to combat evolving attacks. It significantly reduces the overall attack surface and prevents many severe attacks before they reach other areas.
5. Deploy Intrusion Protection System (IPS)
Use an Intrusion Prevention System (IPS) to continuously monitor a network in real-time and prevent malicious code from infiltrating the network. It preventively blocks known vulnerabilities and zero-day attacks using signature-based and anomaly detection technology. It detects malicious behavior, records identified risks and takes preventive measures to prevent vulnerability exploits.
6. Train users
Within an enterprise, numerous attackers take advantage of human error in zero-day attacks in zero-day attacks. Hackers deploy zero-day attacks to deceive or manipulate people into disclosing sensitive or confidential information. Therefore, it is vital for enterprises to educate their employees and clients about zero-day exploits and other emerging risks or threats to improve the security of their systems and organizations. Also, deliver sufficient training to your employees or clients on the risks of downloading malicious files and opening malicious attachments.
7. Employ a strong email security solution
The most common threat vector for every enterprise today is email. The hacker employs a zero-day attack to access the user’s system, typically through an email security breach such as phishing, spam, and Business Email Compromise (BEC). Therefore, it is imperative to use an efficient email security solution to protect your emails and your organization’s confidential information from hackers, spam, malicious emails, and viruses.
8. Implement Incident Response Plan (IRP)
Implement the Incident Response Plan (IRP) to respond quickly to zero-day attacks and minimize emerging risks. All business sizes can benefit from the IRP, which offers a systematic method for identifying and preventing zero-day attacks. IRP includes the six key steps:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons learned
How can InfosecTrain help you?
To protect yourself and your organization from emerging cyberattacks, such as zero-day attacks, you should understand these cyberattacks. InfosecTrain provides various IT security and cybersecurity certification training courses through which you can comprehend emerging cyberattacks and understand their prevention methods. You can enroll in InfosecTrain’s Certified Ethical Hacker (CEH) certification training course, in which you will learn about zero-day attacks along with various other types of cyberattacks or threats and how to protect yourself and your organizations against these cyberattacks.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Jul-2025 | 16-Aug-2025 | 09:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)