Information Gathering Using Recon-ng Tool
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience functions, interactive help, and command completion, Recon-ng provides a powerful environment in which open source web-based reconnaissance can be conducted quickly and thoroughly. Recon-ng has a look and feel similar to the Metasploit Framework, reducing the learning curve for leveraging the framework. However, it is quite different. Recon-ng is not intended to compete with existing frameworks, as it is designed exclusively for web-based open source reconnaissance. If you want to exploit, use the Metasploit Framework. If you want to Social Engineer, us the Social Engineer Toolkit. If you want to conduct reconnaissance, use Recon-ng.

To start Recon-ng in kali linux in the terminal type.
Command:
recon-ng
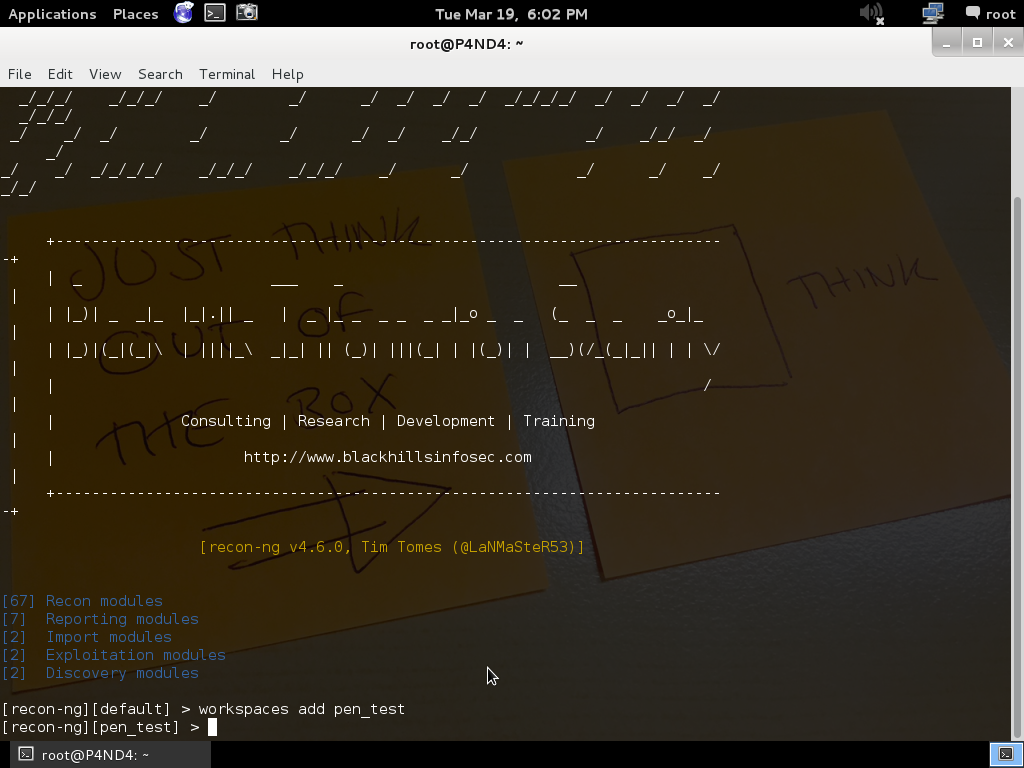
To add work space type
Command:
workspaces add pen_test
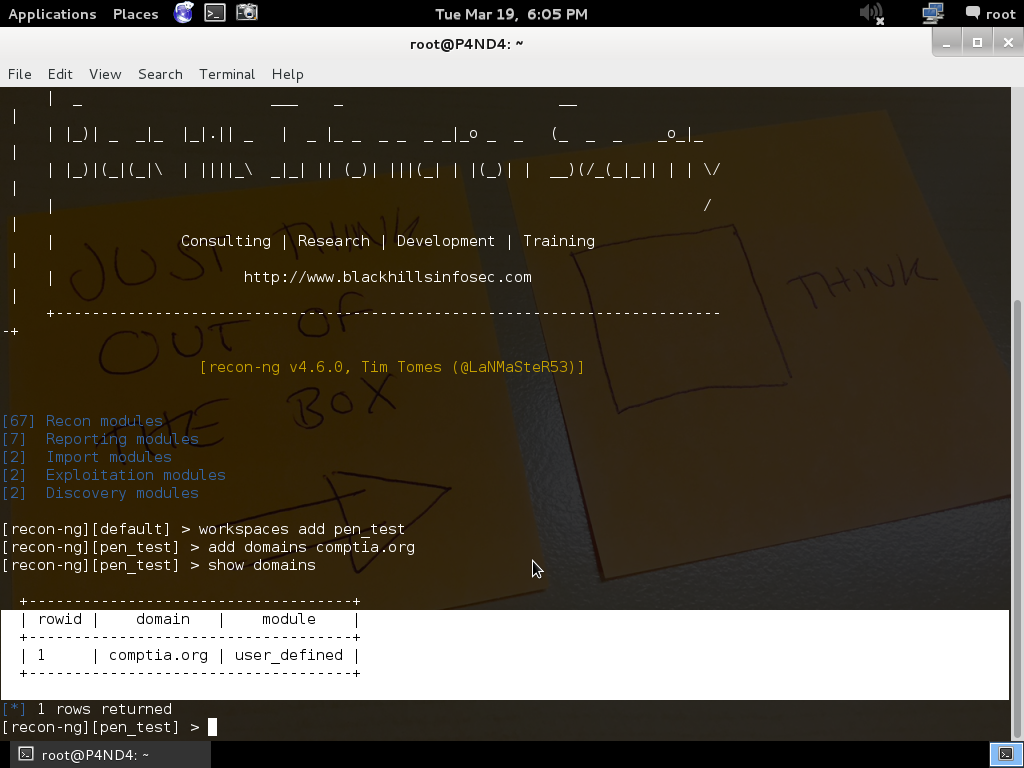
To add domains about which you want to gather information type
Command:
add domains comptia.org (here we are taking example of comptia website)
To check whether the domain is added successfully type
command:
show domains
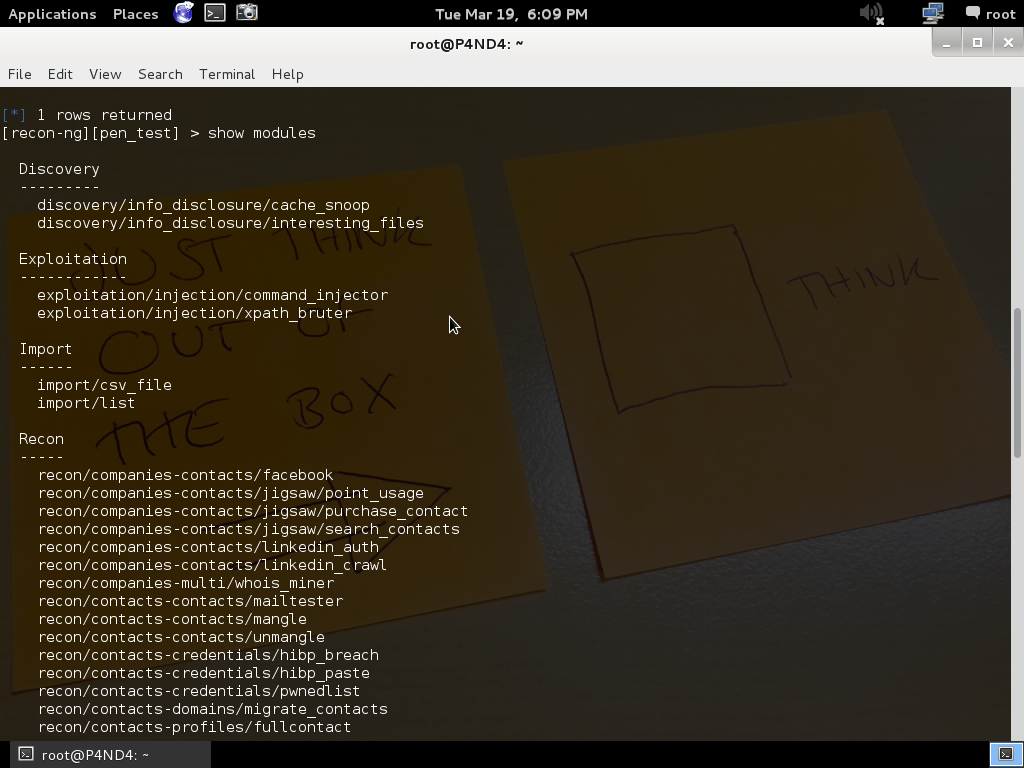
Now to check the modules available type
Command :
show modules
A module is a specific task that recon-ng will execute based on the parameters you provide it.the Recon category has the most modules so far.
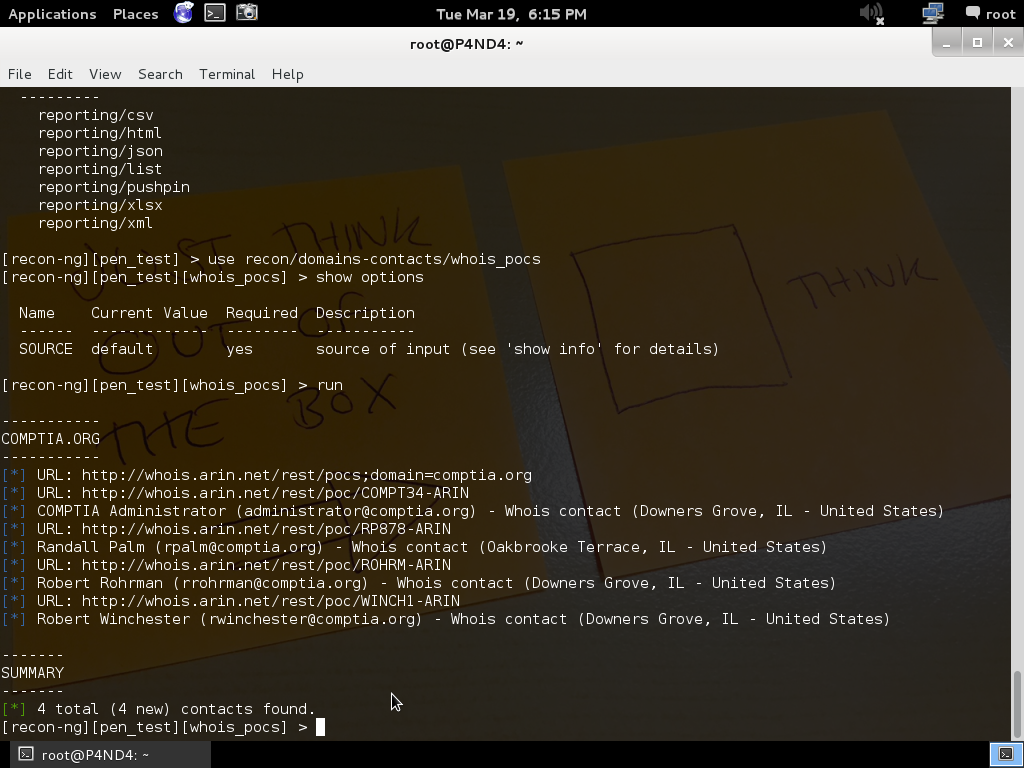
search the domain for contact information.
Command
use recon/domains-contacts/whois_pocs
show options (it will show source option )
run (contacts & email addresses will be displayed)
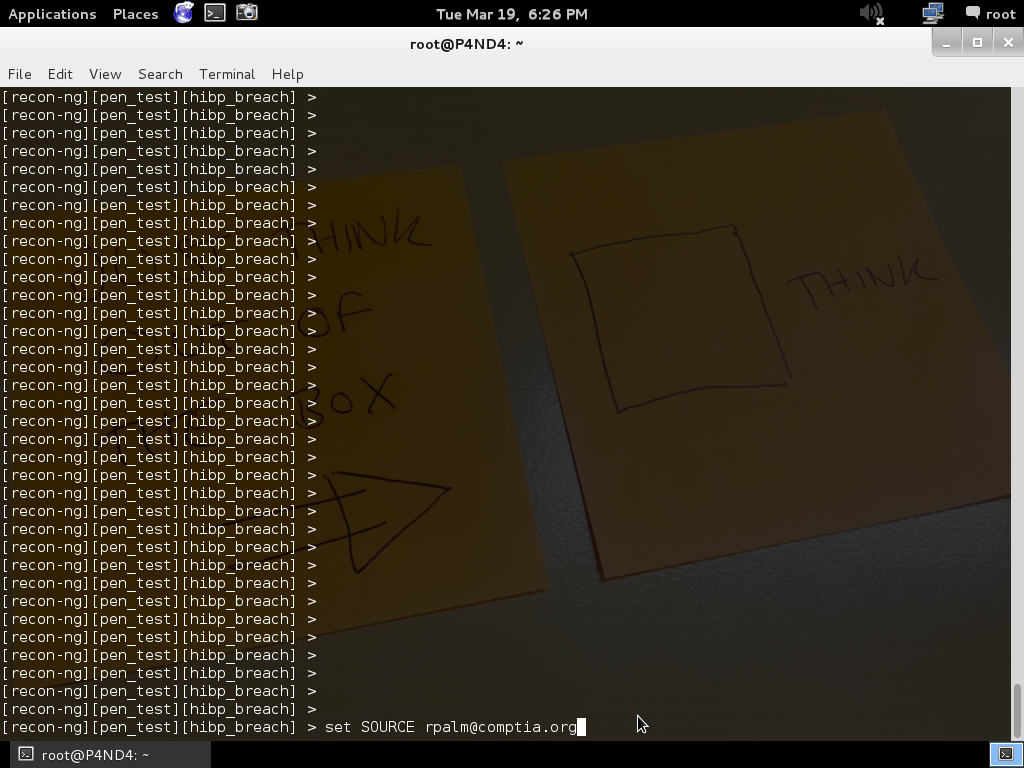
Search account for evidence of compromise
Command:
use recon/contacts-credentials/hibp_breach
This module search that have I been pawned ??HIBP database to see if a particular email account is known to have been effected by any major breaches in last few years.
set source email address (enter email address you found in previous step to check whether I was compromised in last few years or not.)
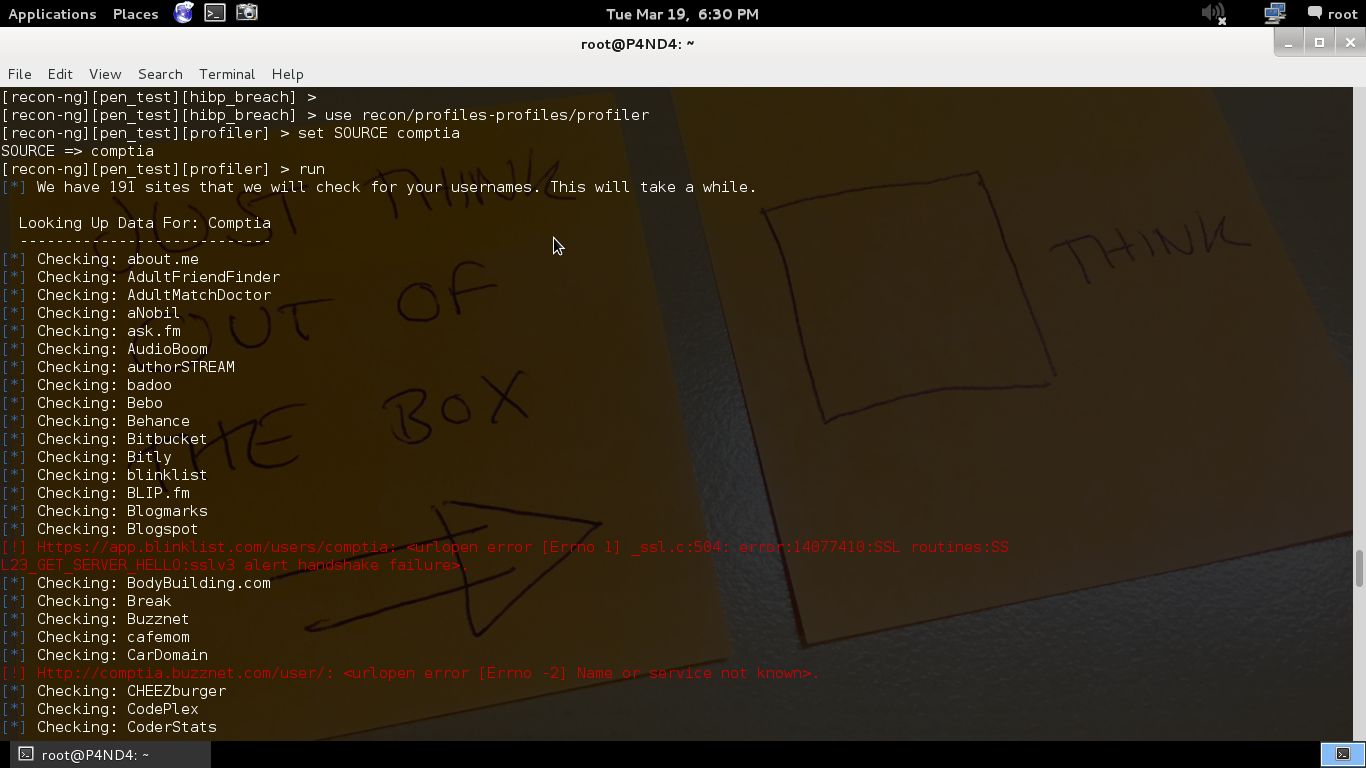
Identify organization’s social media presence
Command
use recon/profiles-profiles/profiler
set source comptia (here domain will be domain name without the top level domain suffix)
run
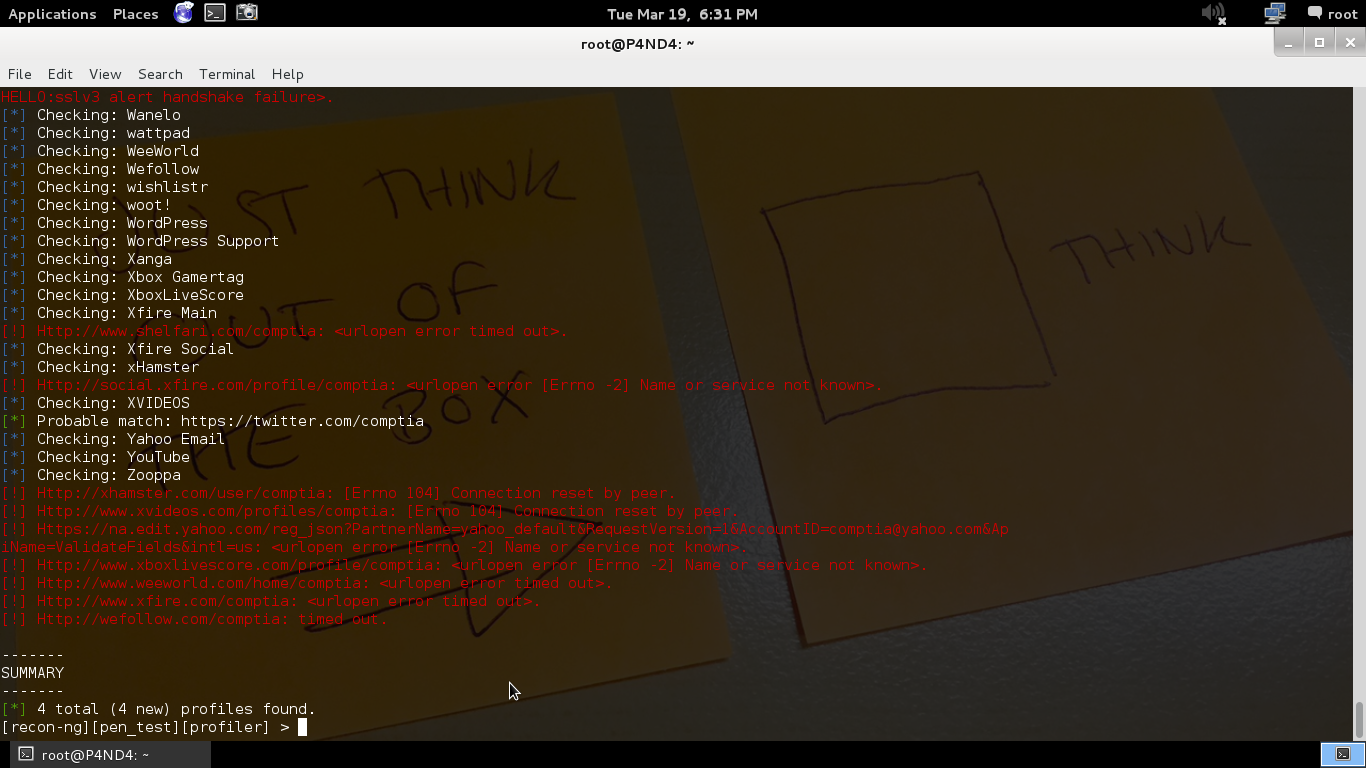 In the same way you can use different modules to gather the information about the organization like.
In the same way you can use different modules to gather the information about the organization like.
Identify organization mail based DNS Records
Command:
recon/domains-hosts/mx_spf_ip
run
Search subdomains
Command :
recon/domains-hosts/brute_hosts
run
At last to generate report of your findings type
Command :
use reporting /html
show options
set creator (your name)
set customer (clients name )
set filename /root/desktop/recon_report.html
run
To open the report double click recon_report.html.
For collecting additional information like email addresses and host information run the harvester tool which we have discussed in our earlier article. For More updates on cyber security stay tuned….
Certified Ethical Hacker (CEH v10) Online Training & Certification Course






 1800-843-7890 (India)
1800-843-7890 (India)