ISACA CRISC Domain 4: Information Technology and Security

Domains of CRISC
CRISC comprises the following four domains, which basically explains the entire Risk Management Life Cycle:
- Domain 1: Governance (26%)
- Domain 2: IT Risk Assessment (20%)
- Domain 3: Risk Response and Reporting (32%)
- Domain 4: Information Technology and Security(22%)
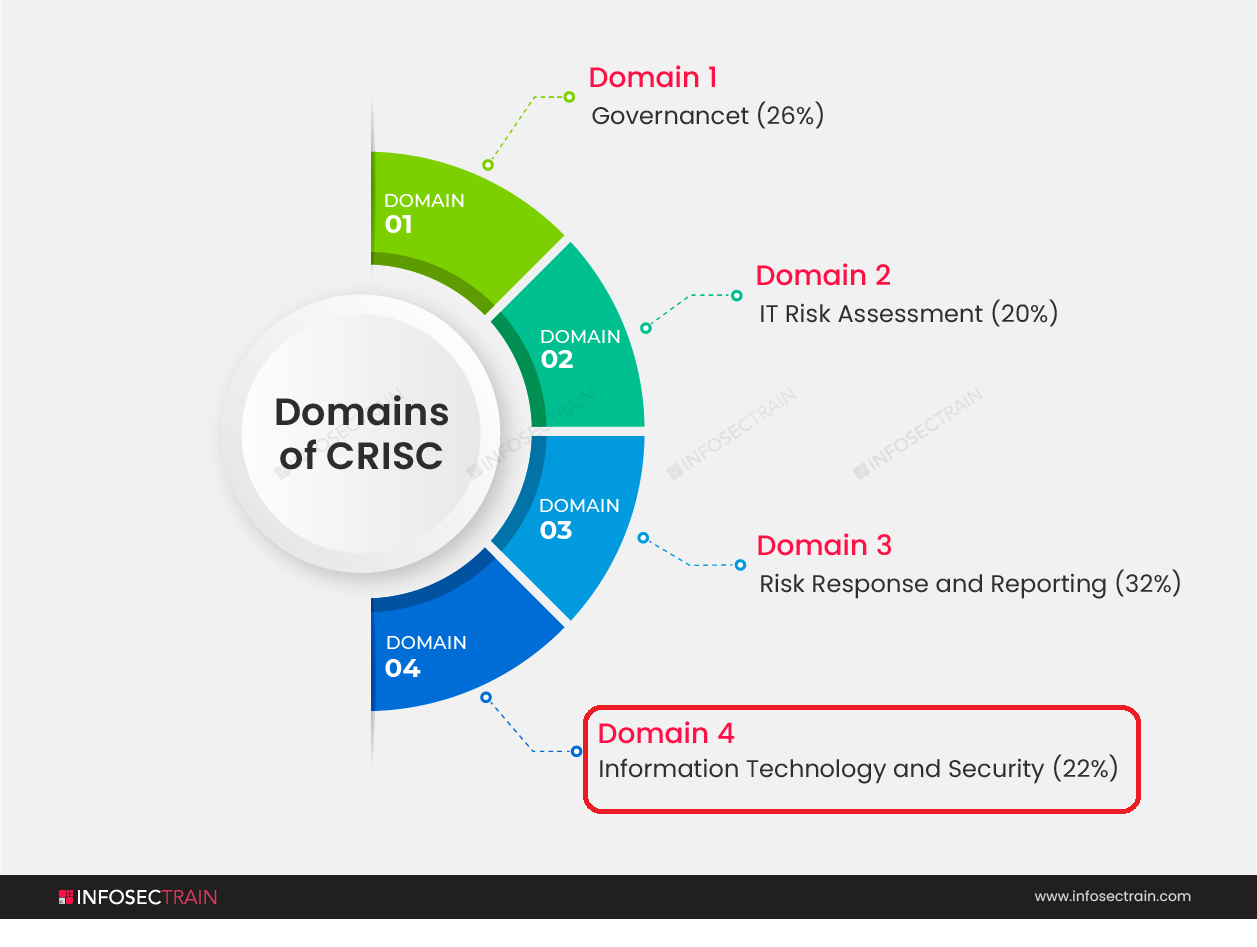
In this article, we are going to explain the fourth and last domain of CRISC, which is ‘Information Technology and Security.’
Domain 4: Information Technology and Security
The last domain of CRISC that is Information Technology and Security comprises 22% weightage which is a fair share. IT security is a collection of cybersecurity methods that protects corporate assets such as computers, networks, and data against unwanted access.
It protects the integrity and confidentiality of sensitive data by preventing skilled hackers from accessing it. The necessity to safeguard your digital assets and network devices is becoming more important as hackers become more sophisticated. While IT security might be costly, a large breach can cost a business far more. Large data breaches might put a small business’s health in jeopardy. IT security teams can use an incident response plan as a risk management strategy to gain control of the situation during or after an event.
This is bifurcated into:
1. Information Technology Principles
- Enterprise Architecture: Enterprise Architecture also referred to as EA is a discipline that identifies and analyses the execution of change toward desired business vision and objectives in order to drive enterprise responses to disruptive forces proactively and comprehensively. Six essential aspects must be included in a comprehensive EA strategy, all of which must be developed to function together:
- Architecture Governance
- Architecture Framework
- Implementation Methodology
- Documentation Artifacts
- Architecture Repository
- Associated Best Practices
- IT Operations Management (e.g., change management, IT assets, problems, incidents): IT Operations management is a critical aspect of any business since it aids in the efficient management, control, and supervision of products, services, and people. As far as operations management is concerned, it affects every area and business.
- Project Management: Project management is the process of guiding a team’s efforts to meet all project objectives while staying within budget limitations. Typically, this data is described in project documentation, which is generated at the start of the development process. Scope, time, and budget are the three main restrictions.
- Disaster Recovery Management (DRM): After a natural catastrophe, a cyber assault, or even economic interruptions caused by the COVID-19 pandemic, disaster recovery management is an organization’s technique of recovering access and functioning to its IT infrastructure. A disaster recovery strategy might include a range of disaster recovery (DR) approaches.
- Data Lifecycle Management: Data Lifecycle Management (DLM) refers to the many stages that data goes through during its life, from creation to disposal. The stages of the data lifecycle include creation, use, sharing, storage, and destruction. Both structured and unstructured data may be included.
- System Development Life Cycle (SDLC): The systems development life cycle, also known as the application development life cycle, is a method for designing, developing, testing, and deploying an information system in systems engineering, information systems, and software engineering.
- Emerging Technologies: Emerging technologies are those whose development, practical applications, or both are yet substantially unmet, to the point that they are symbolically emerging into prominence from obscurity. Emerging technologies are frequently portrayed as having the ability to alter the status quo.
2. Information Security Principles
- Information Security Concepts, Frameworks, and Standards:
- Information Security Awareness Training: IT and security professionals utilize security awareness training as a method to minimize and manage user risk. These initiatives are aimed to educate consumers and workers to understand their responsibility in preventing data breaches.
- Business Continuity Management: Business continuity management, also referred to as BCM, is a methodology for determining the risk of an organization’s vulnerability to internal and external threats. Disaster recovery, business recovery, crisis management, incident management, emergency management, and contingency planning are all incorporated in BCM.
- Data Privacy and Data Protection Principles: There are seven principles to be remembered for Data protection:
Confidentiality, Integrity, and Availability are three essential information security concepts that are crucial to information. Authentication, authorization, and non-repudiation are the terms used to describe how these principles relate to the persons who utilize the information.
The Information Security Framework is made up of a series of documents that clearly outline your company’s chosen policies, procedures, and processes. It efficiently communicates to all stakeholders how your organization’s information, systems, and services are handled.
ISO/IEC 27001 is a global standard for determining successful information security management. It is the only certification standard for information and cyber security that is widely accepted. This is the most recent version of the world’s most widely used standard for specifying information security procedures.
- Lawfulness, fairness, and transparency
- Purpose limitation
- Data minimization
- Accuracy
- Storage limitation
- Integrity and confidentiality (security)
- Accountability
What you’ll learn?
Domain 4 of CRISC comprises various sub-domains and topics.
- It will take you through various subjects like enterprise architecture, security architecture, and maturity models.
- It will provide an introduction to OSI layers, TCP/IP, network cabling, and network devices.
- It will provide you with knowledge of types of firewalls, Demilitarized Zone (DMZ), proxy server, and firewall implementation.
- We will also learn about the key aspects of Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), and Domain Name Systems.
- It provides an overview of Wireless Access Point (WAP) and Virtual Private Network (VPN).
- Cloud computing, project & program management, phases of SDLC, system migration & changeover techniques, enterprise resiliency (BCP & BIA), recovery objectives, business continuity plan and business impact analysis, and incident response plan and procedures are part of this domain.
- It also explains data classification, data life cycle management, system accreditation and certification, online auditing techniques, and emerging and new technologies.
- It will equip you with the knowledge of Deepfakes, Internet of Things, Information Security Principles, Segregation of duties, Cross-training and Job rotation, and Factor of Authentication.
- It will also provide an introduction to Password Management, Biometrics, Asymmetric Encryption, Digital Signature, and Public Key Infrastructure (PKI).
- You’ll also learn about Information Security Awareness Training, Data Privacy, and Different Attack Methods.
CRISC with InfosecTrain
CRISC Certification is a sign of risk assessment and information standard monitoring competence and skills. This certification equips the applicant with the necessary attitude to effectively advance up the professional ladder in today’s competitive environment. You must buckle down for the certification exam if you want to stand out from the throng and expand your job possibilities. InfosecTrain’s CRISC certification course will introduce you to the specific challenges of IT and business risk management. Because we are a significant training provider in the globe, we utilize highly qualified trainers who are experts in the field to create the entire action plan. Experienced professionals at InfoSecTrain will walk you through the process of building a solid CRISC foundation in order to upskill your risk management knowledge to a competent level. You can have a good chance of passing the exam on the first try if you have a solid approach, total devotion, and great resources. Join our training program and go on the fast track to success.







 1800-843-7890 (India)
1800-843-7890 (India)