(ISC)² ® CSSLP Domain 6: Secure Software Lifecycle Management (11%)

Domains of (ISC)² ®CSSLP
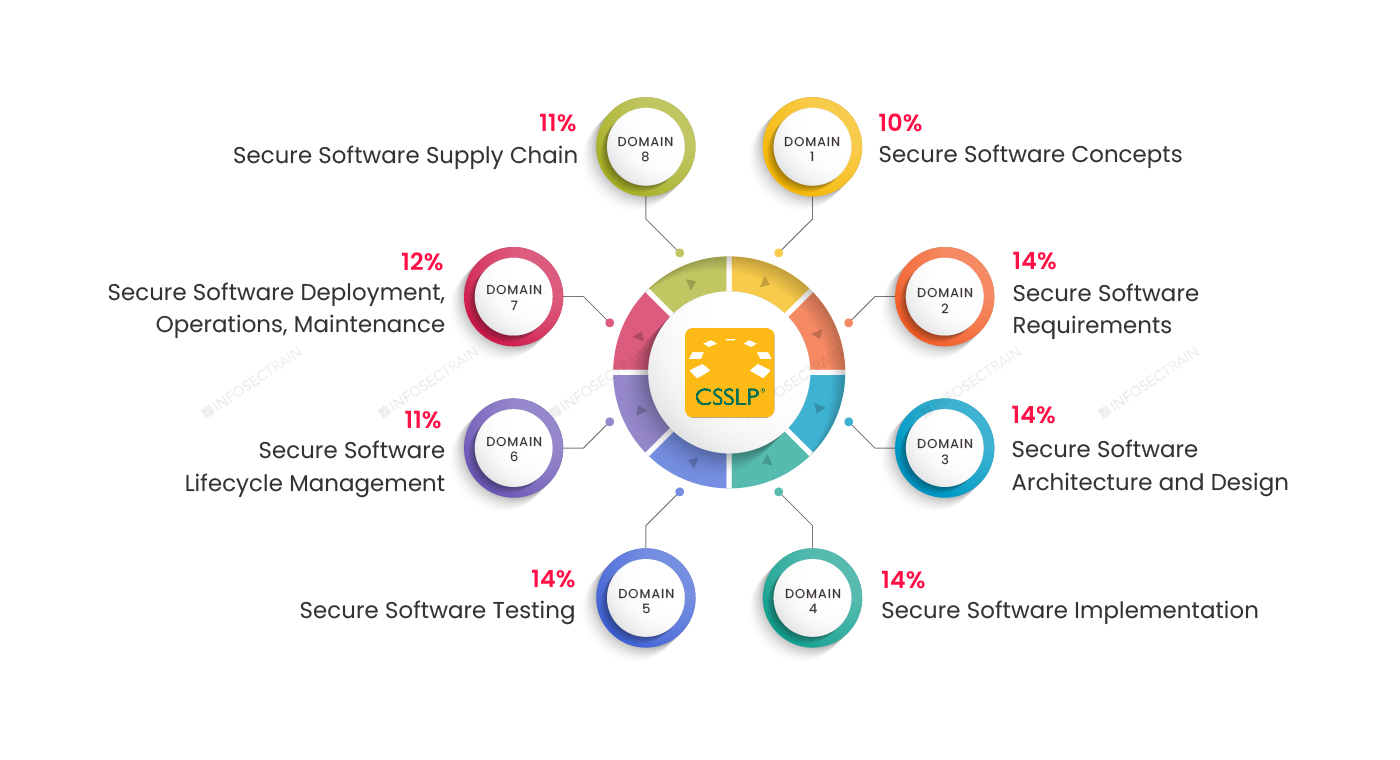
Domain 1: Secure Software Concepts (10%)
Domain 2: Secure Software Requirements (14%)
Domain 3: Secure Software Architecture and Design (14%)
Domain 4: Secure Software Implementation (14%)
Domain 5: Secure Software Testing (14%)
Domain 6: Secure Software Lifecycle Management (11%)
Domain 7: Secure Software Deployment, Operations, Maintenance (12%)
Domain 8: Secure Software Supply Chain (11%)
This article provides an overview of (ISC)² ® CSSLP Domain 6: Secure Software Lifecycle Management (14%).
Domain 6: Secure Software Lifecycle Management (11%)
The sixth domain of CSSLP is secure software lifecycle management which comprises 11% of exam weightage. This is one of CSSLP’s most essential domains, and it relates to the management of the various processes and procedures needed to implement security protocols through each stage of the software development lifecycle (SDLC).
This domain encompasses the whole lifecycle, from planning and road mapping to determining appropriate security requirements and procedures for future implementation. It demonstrates how to manage security as part of a software development approach and documentation. It also explains how to create security metrics (e.g., defects per line of code, criticality level, average remediation time, and complexity).
This domain is divided into the following subsections:
- Secure configuration and version control (e.g., software, hardware, implementation, interface, patching)
- Define strategy and roadmap
- Manage security within a software development methodology
- Identify security standards and frameworks
- Define and develop a security documentation
- Define security status (e.g., defects per line of code, criticality level, average remediation time, complexity)
- Decomposition software
- Report security status (e.g., dashboards, reports, feedback loops)
- Incorporated Integrated Risk Management (IRM)
- Promote security culture in software development
- Implement continuous improvement (e.g., retrospective, lessons learned)
1. Secure configuration and version control (e.g., hardware, software, implementation, interface, patching)
When we develop an application, so many parameters need to be considered. Security configuration and version control are essential in secure software lifecycle management (like hardware, software, implementation, interface, and patching). This section explains that software configuration management can be done practically and securely with version control. That allows developers and enterprises to work more quickly on increasing the quality of their products while documenting and reviewing a complete history of their developments, resulting in a successful end product.
2. Define strategy and roadmap
This section will learn why a comprehensive plan and calculated roadmap are required during the application development process, which outlines what you’ll do and the method you’ll choose so that security can be integrated into each phase of the software development lifecycle.
3. Manage security within a software development methodology
This section explains how the application was developed. There are different methodologies used in the development process. Like we have adaptive, which is known as Agile, and predictive, known as waterfall methodology. Here you will understand where to use Agile, where to use waterfall, and what scrum is.
4. Identify security standards and frameworks
When it comes to security standards and frameworks, we all know that there are several standards for various objectives. Professionals create these standards to protect organizations from any kind of risk. So this section will explain how to identify those security standards and frameworks.
5. Define and develop a security documentation
Documentation is an essential part of any software development lifecycle process. So this section defines and develops security documentation.
6. Define security status (e.g., criticality level, defects per line of code, average remediation time, complexity)
The security metrics in the software development process encompass criticality level, average remediation time, complexity, and defects per line of code.
7. Decomposition software
In this section, you will understand the following points:
- End-of-life policies (e.g., configuration removal, credential removal, license cancellation, and archiving)
- Data deposition (e.g., retention, destruction, dependencies)
8. Report security status (e.g., dashboards, reports, feedback loops)
During the application development process, you’ll learn how to manage a security report and the status of security (e.g., reports, dashboards, feedback loops).
9. Incorporated Integrated Risk Management (IRM)
This section will teach you how to include risk management in the software development process to mitigate and manage risk. In this section, you will explore regulation and compliance, standards and guidelines (e.g., National Institute of Standards and Technology (NIST), International Organization for Standardization (ISO), Payment Card Industry (PCI), Software Assurance Forum for Excellence in Code (SAFECode), OWASP, Building Security In Maturity Model (BSIMM), and Software Assurance Maturity Model (SAMM)), risk management (e.g., avoid, accept, mitigate, transfer), terminology (e.g., vulnerability, threats, residual risk, controls, probability, impact), and technical risk vs. business risk.
10. Promote security culture in software development
You’ll learn about the security champions in this section, who are ultimately responsible for eliminating fear, boosting independence, and promoting a tranquil workplace.
11. Implement continuous improvement (e.g., retrospective, lessons learned)
As we already know, a retrospective is designed to uncover facts or ideas that have tangible implications for the field’s performance and provide improvement ideas based on such findings. So in this section, these processes are implemented, which corrects and improves the development process.
CSSLP with InfosecTrain
When it comes to software development, it’s no longer just about coding; it’s about building secure code to minimize software development weaknesses. The CSSLP certification validates your advanced expertise in designing, developing, and implementing security processes throughout the SDLC. InfoSecTrain’s CSSLP course is spread out and covers all eight domains of the CSSLP certification. So, take a look at InfosecTrain.







 1800-843-7890 (India)
1800-843-7890 (India)