Mastering Network Discovery with Nmap: A Step-by-Step Guide
Network discovery is a cornerstone of ethical hacking and penetration testing, providing critical insights into the devices and services within a network. At the heart of this process lies Nmap (Network Mapper), a powerful open-source tool that has become a staple in the cybersecurity toolkit. Known for its versatility, Nmap allows Ethical Hackers and security professionals to identify active hosts, enumerate running services, and detect vulnerabilities, all while leveraging the robust capabilities of its Nmap Scripting Engine (NSE) for automation and advanced functionality.

This guide takes you step-by-step through the process of using Nmap for network discovery.
Why is Nmap Essential for Network Discovery?
Nmap plays a pivotal role in modern network discovery and security assessments by offering the following capabilities:
- Host Discovery: Identifying active devices on a network.
- Port Scanning: Determining open ports and associated services.
- Service and Version Detection: Identifying running services and their versions.
- Scripting Engine: Automating tasks and checking for vulnerabilities using the Nmap Scripting Engine (NSE).
- Operating System Detection: Determining the operating system and version of target hosts.
Role of Nmap in Network Discovery
Nmap enables Ethical Hackers to gain an overview of a network’s structure, devices, and potential vulnerabilities. Nmap simplifies this process through its robust feature set:
- Active Host Identification: Quickly find which devices are online and connected to a network.
- Service Enumeration: Determine which applications are running and their potential vulnerabilities.
- Network Layout Analysis: Offers insights into device interconnections, network configurations, and areas where security controls may be lacking.
- Vulnerability Detection: Using NSE scripts, Nmap can uncover known vulnerabilities in services and configurations.
Nmap Network Discovery Tutorial
Step 1: Setting Up Nmap
1. Installation
Ensure Nmap is installed on your system. Use the following commands based on your OS:
- Linux (Debian-based)
| sudo apt update //used for Kali sudo apt install nmap //used to install nmap in Kali |
- macOS (Homebrew):
| brew install nmap |
- Windows: Download the installer from the official Nmap website.
2. Verify Installation
Run nmap –version to confirm the installation.
Step 2: Host Discovery
Identifying active hosts is the first step in network reconnaissance.
1. Ping Scan: Quickly discover live hosts on the network without performing detailed port scans. They are commonly used for a preliminary sweep to understand which devices are reachable.

| nmap -sn 192.168.xxx.0/24 |
What It Does:
- This scan sends ICMP (ping) requests to each IP address in the specified range.
- If a device responds, it is marked as “alive.”
- This command scans the 192.168.109.0/24 subnet for active hosts.
- Note: The -sn option disables port scanning, focusing solely on host discovery.
2. ARP Ping Scan: Effective for local networks, sending ARP requests to identify active devices. This method is reliable for discovering hosts within the same subnet.
| nmap -sn -PR 192.168.xxx.0/24 |

What It Does:
- The -PR option forces Nmap to use ARP requests for host discovery.
- ARP requests are sent to all IP addresses in the specified range.
- If a device responds, it is confirmed as active.
3. UDP Ping Scan: Useful when ICMP is blocked; sends empty UDP packets to specified ports.
| nmap -sn -PU 192.168.xxx.0/24 |

What It Does:
- This scan can help identify hosts that do not respond to ICMP requests.
- The -PU option sends UDP packets to a specified or default port (e.g., port 40125).
- Hosts that respond are marked as live.
- Unlike TCP, UDP operates as a connectionless protocol, so responses may vary (e.g., ICMP unreachable or a direct UDP reply).
Step 3: Port Scanning and Service Enumeration
After identifying active hosts, the next step is to detect open ports and running services.
1. TCP SYN Scan: Conduct stealthy port scans to identify open, closed, or filtered ports while minimizing detection.
| nmap -sS 192.168.xxx.xxx |

What It Does:
- Sends SYN packets (used in TCP handshakes) to each port.
- If a SYN-ACK is received, the port is open.
- If an RST (reset) is received, the port is closed.
- This is faster and stealthier than a full TCP connect scan because it doesn’t complete the handshake, reducing the chance of detection by intrusion detection systems (IDS).
2. TCP Connect Scan: Perform a full TCP handshake to determine the status of ports.
| nmap -sT 192.168.xxx.xxx |

What It Does:
- This scan establishes a complete TCP connection with the target.
- While more detectable, it can be used when SYN scans are not permitted (e.g., by non-privileged users).
- Effective for networks with no restrictions on full handshakes.
3. Service Version Detection: Identifies services and their versions on open ports. Combining SYN scan with version detection provides detailed information about running services.
| nmap -sV 192.168.xxx.xxx |
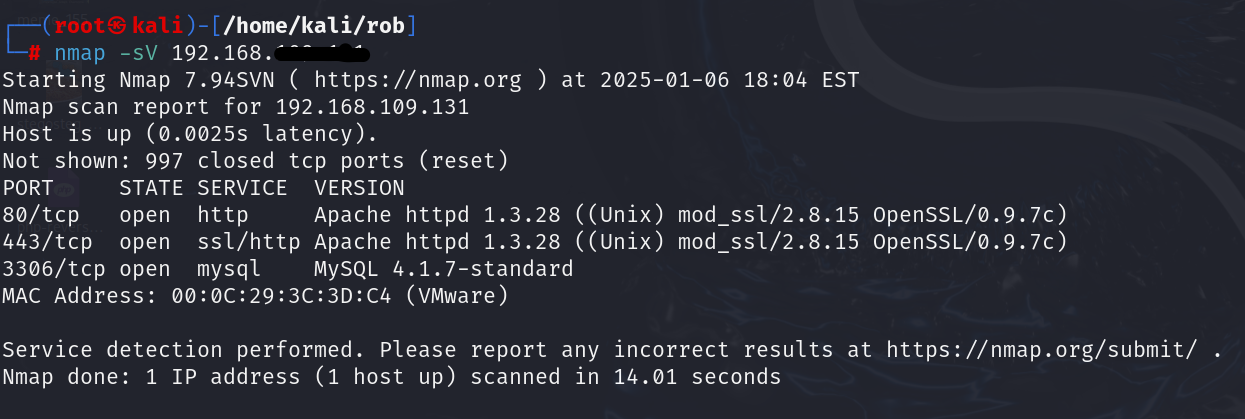
What It Does:
- Sends specially crafted packets to extract banners or responses from services.
- Useful for understanding the software running (e.g., Apache 2.4.41 on port 80).
- Helps assess whether the identified version has known vulnerabilities.
Step 4: Advanced Scanning with Nmap Scripting Engine (NSE)
NSE enhances Nmap’s capabilities by allowing the use of scripts for various tasks, including vulnerability detection and advanced service enumeration.
1. Enumerating Services
NSE scripts for service discovery provide detailed insights.
HTTP Enumeration: Used to gather detailed information about web servers, their configurations, and hosted applications. It helps identify potential vulnerabilities and areas for further testing.
| nmap -p 80,443 –script http-enum 192.168.xxx.xxx |
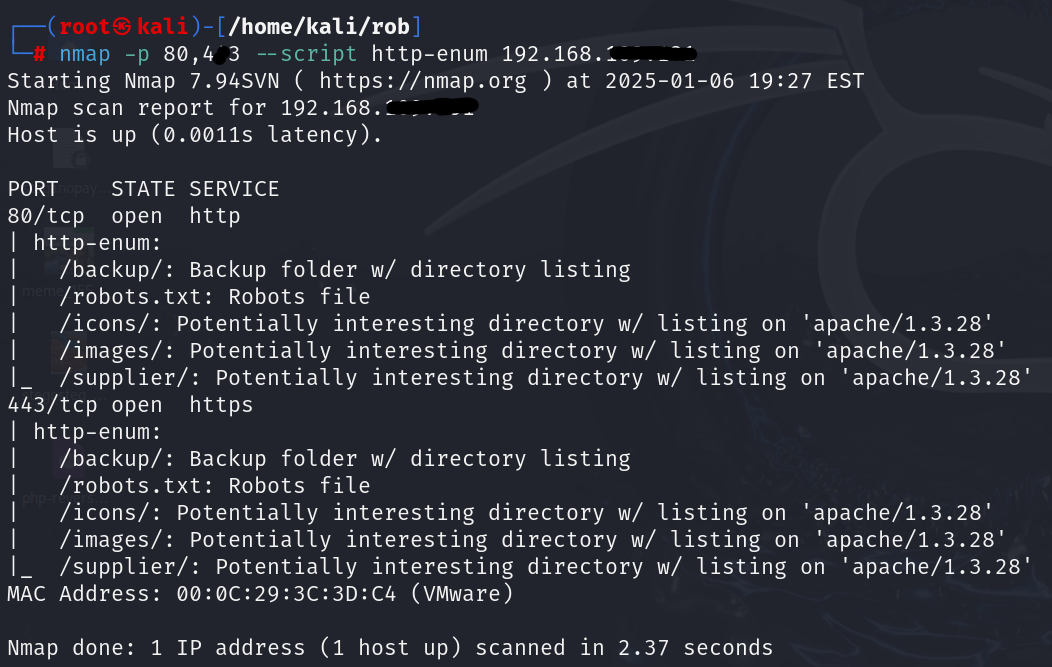
What It Does:
- Enumerates common files/directories on web servers.
- The -p 80,443 specifies HTTP and HTTPS ports.
- The http-enum script probes the server for directories, files, and services.
- Results include detailed information about server banners, configurations, and accessible resources.
FTP Enumeration: Used to gather information about an FTP server, such as supported features, anonymous access permissions, and exposed directories. It helps assess potential vulnerabilities in FTP configurations.
| nmap -p 21 –script ftp-anon,ftp-syst 192.168.xxx.xxx |

What It Does:
- The -p 21 specifies the FTP service port.
- The ftp-anon script checks for anonymous login access.
- The ftp-syst script retrieves system information about the FTP server.
2. Vulnerability Detection
Vuln: Used to detect vulnerabilities in services, operating systems, and applications running on target devices. It automates the process of vulnerability detection, saving time and ensuring consistency.
| nmap –script=vuln 192.168.xxx.xxx |
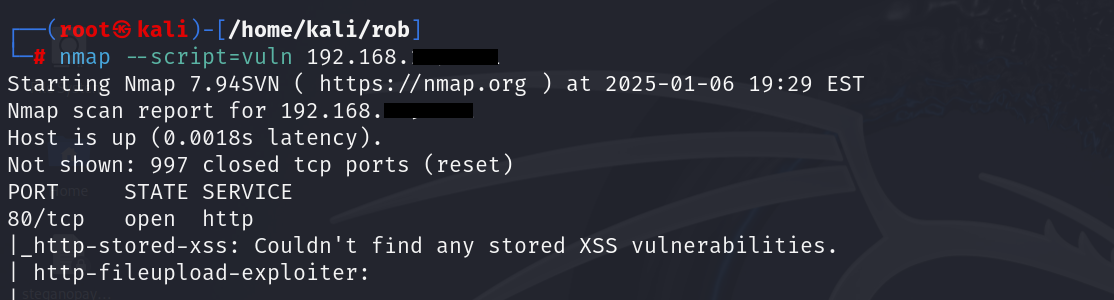
What It Does:
- The –script=vuln option runs a collection of scripts designed to identify known vulnerabilities.
- The output provides actionable details, such as the type of vulnerability detected, its severity, and any associated CVEs (Common Vulnerabilities and Exposures).
Run vulnerability-specific NSE scripts to identify weaknesses.
Scan for MS17-010 (EternalBlue)
| nmap –script=smb-vuln-ms17-010 -p 445 192.168.xxx.xxx |
Checks if the SMB service is vulnerable to EternalBlue.

Scan for SSL/TLS Vulnerabilities
| nmap –script=ssl-enum-ciphers -p 443 192.168.xxx.xxx |
Identifies weak SSL/TLS ciphers and misconfigurations.

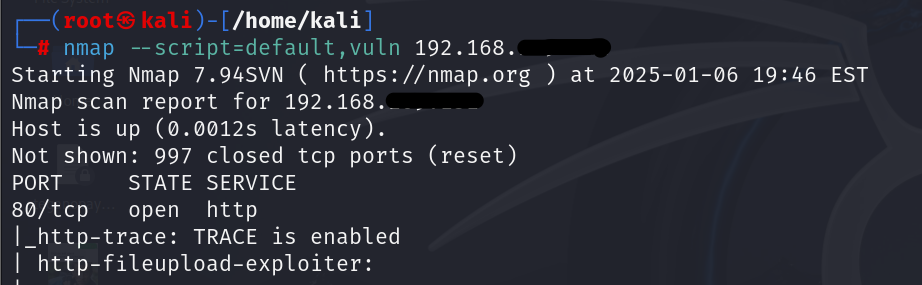
3. Running Multiple Scripts
You can run multiple scripts by specifying categories or using a comma-separated list:
| nmap –script=default,vuln 192.168.xxx.xxx |
This command runs all default and vulnerability detection scripts against the target.
Step 5: Advanced Techniques
1. Nmap Operating System (OS) Detection
Nmap can attempt to determine the host’s operating system running on the target devices.
| nmap -O 192.168.xxx.xxx |
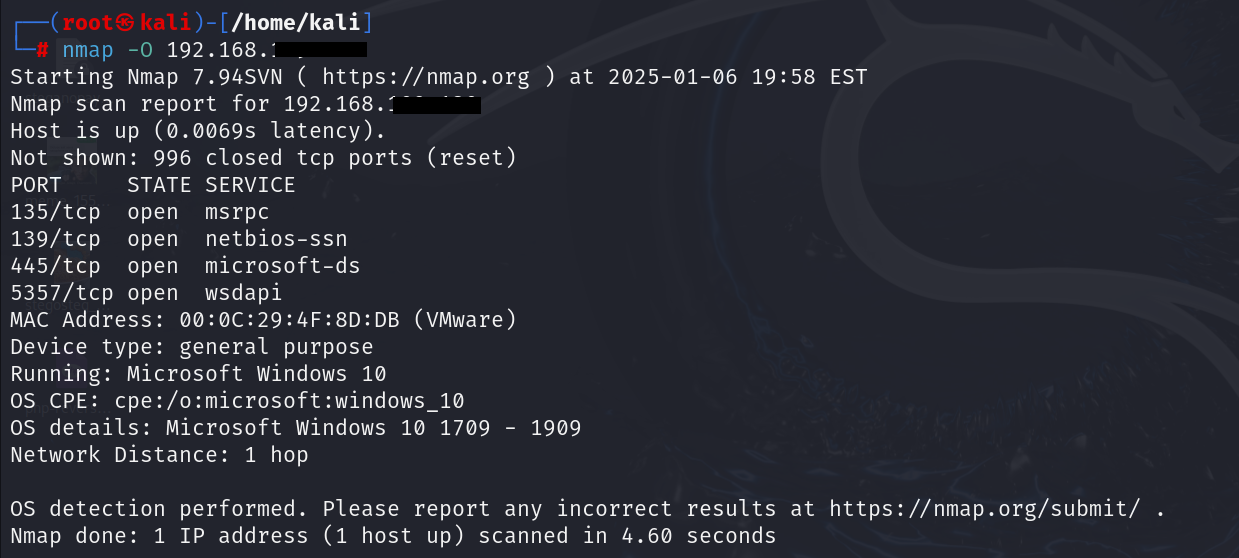
What It Does:
- Uses TCP/IP fingerprinting by analyzing subtle differences in packet responses.
- Helps determine if a device is running Linux, Windows, or another OS, along with its version.
- Useful for tailoring subsequent scans or exploits to the target’s specific OS.
2. Scan Multiple Hosts Simultaneously
Nmap can scan multiple hosts or an entire subnet in a single command.
| nmap -sS 192.168.1.1 192.168.1.2 nmap -sS 192.168.1.0/24 |
What It Does:
- Scans multiple specific IP addresses or all devices within a subnet.
- Efficiently identifies active hosts and open ports on a large scale.
- Useful for scanning entire networks or ranges of IPs in a single run.
3. Evading Firewalls and IDS
Nmap provides techniques to bypass firewalls and Intrusion Detection Systems (IDS).
| nmap -f 192.168.1.1 nmap –source-port 80 192.168.1.1 nmap -T4 192.168.1.1 |
What It Does:
- Fragment Packets (-f): Breaks packets into smaller fragments to evade simple firewall rules.
- Spoof Source Port (–source-port): Sets a specific source port (e.g., 80) to mimic legitimate traffic, as firewalls often allow HTTP traffic.
- Adjust Timing (-T4): Controls scan speed to balance stealth and speed (T0 to T5, where T4 is faster but still cautious).
4. Scanning IPv6
Nmap supports IPv6 scanning for networks and hosts.
| nmap -6 |
What It Does:
- Enables scanning of devices using IPv6 addresses, the next-generation internet protocol.
- Identifies open ports, services, and vulnerabilities on IPv6-enabled hosts.
Check out other related articles:
- Step-by-Step Guide for theHarvester Tool
- Steps for Effective DNS Footprinting
- The Ultimate Guide to SMTP and DNS Enumeration Practices
- Web Vulnerability Scanning with Nikto
CEH v13 AI with InfosecTrain
Enroll in InfosecTrain’s CEH v13 AI certification training to gain hands-on expertise with the Nmap tool and other essential cybersecurity techniques. This course combines practical insights and real-world applications, empowering you to identify vulnerabilities, conduct network scans, and understand modern AI-driven hacking methods. Master the skills to safeguard systems and elevate your ethical hacking expertise.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 16-Aug-2025 | 28-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Sep-2025 | 12-Oct-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 20-Sep-2025 | 26-Oct-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)