Mitigation Techniques to Secure Enterprise
Creating a robust shield against cyber threats is essential in today’s interconnected digital landscape. CompTIA Security+ Domain 2.5 delves into the arsenal of mitigation techniques designed to fortify enterprises against potential security breaches and cyberattacks.

Before delving into Domain 2.5, it is essential to understand the significance of the preceding sections within Domain 2. Each of these critical sections provides indispensable insights aimed at bolstering enterprise security.
2.5 Purpose of Mitigation Techniques Used to Secure the Enterprise
This section guides cybersecurity enthusiasts through the intricate defenses in today’s dynamic threat landscape. It explores the purpose and significance of mitigation techniques, providing insights into fortifying organizations against cyber threats. This section helps develop a comprehensive understanding of the strategic measures required to protect enterprises from malicious attacks and unforeseen vulnerabilities. Let us uncover the essential mitigation techniques outlined in this crucial section and use examples to illustrate these concepts.
Segmentation: Dividing the network into distinct segments or zones to isolate critical systems from potential threats.
Example: A company might create separate segments for different departments like HR, finance, and IT. If one segment gets compromised, segmentation helps prevent the breach from spreading to other areas.
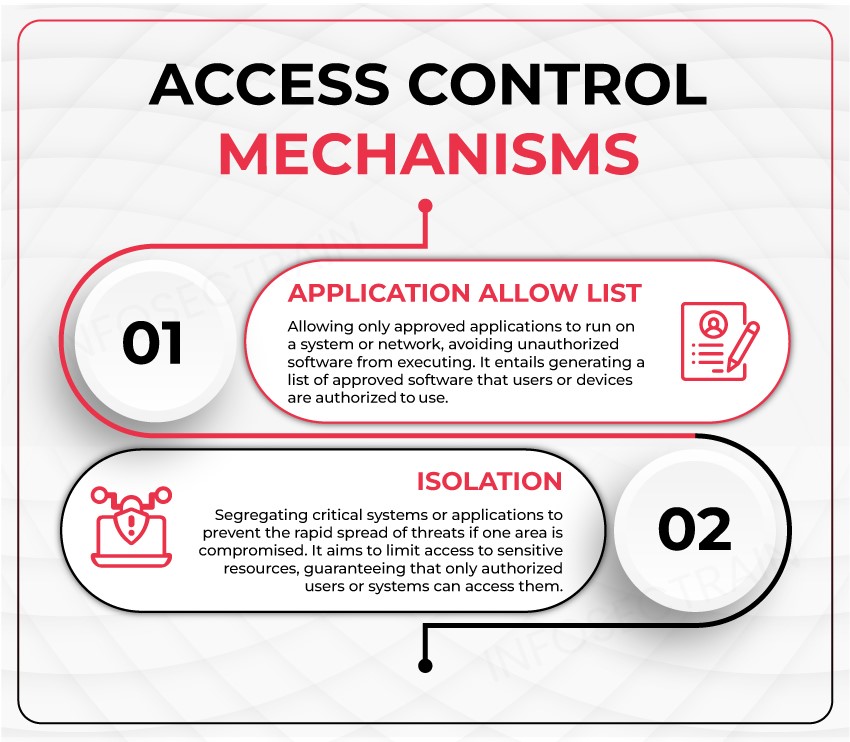
Access Control: Access control regulates who is authorized to access specific resources or perform certain actions within a network. Application Allow List (also known as Application Whitelisting) and permissions mechanisms are commonly used for this purpose.
Patching: Regularly updating systems, software, and applications to address known vulnerabilities and strengthen security.
Example: A company might regularly update its operating systems and software to patch known security vulnerabilities and protect against potential exploits.
Encryption: Securing sensitive data by converting it into an unreadable format using cryptographic algorithms.
Example: Secure Socket Layer (SSL) encryption secures online transactions, safeguarding credit card details during online purchases.
Monitoring: Continuous surveillance and analysis of network and systems activities to detect and respond to anomalies or security breaches.
Example: Using SIEM (Security Information and Event Management) and IDS (Intrusion Detection Systems) tools that monitor networks for suspicious behavior, triggering alerts for potential threats.
Least Privilege: Providing users with minimal access rights necessary for their roles, reducing the risk of unauthorized access.
Example: An employee in the accounting department might have read-only access to certain financial records but cannot modify them.
Configuration Enforcement: Ensuring that systems adhere to security configurations and standards.
Example: Enforcing password complexity rules on all company devices to prevent easy access by unauthorized users.
Decommissioning: Removing outdated systems or software that are no longer supported and might pose security risks.
Example: Discontinuing the use of older servers running on unsupported operating systems to prevent vulnerabilities.
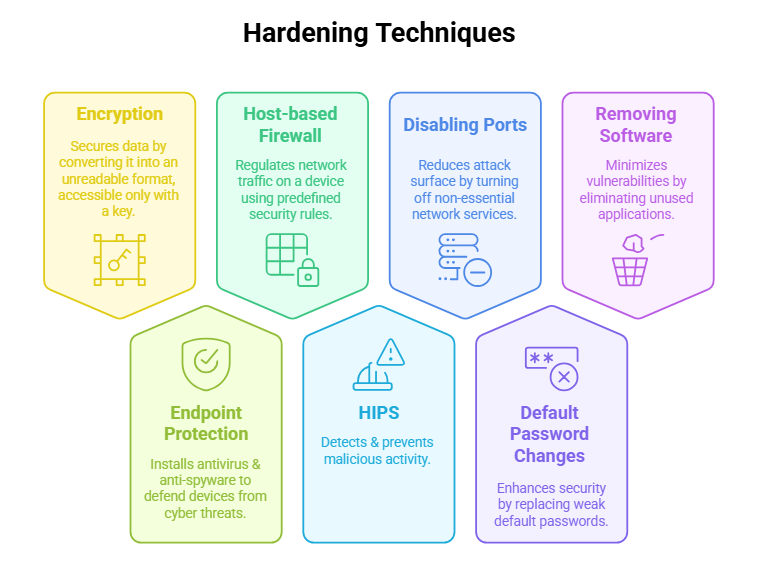
Hardening Techniques: Hardening techniques are practices and strategies utilized to enhance the security of a system, network, or device to make it more resistant to cyber threats and unauthorized access.
Exploring the purpose behind these mitigation techniques fortifies the security posture and equips individuals with the know-how to combat vulnerabilities effectively.
Master CompTIA Security+ with InfosecTrain
Enroll in InfosecTrain‘s CompTIA Security+ certification training course, as we offer an unparalleled opportunity to understand the nuances of mitigation techniques. Our training equips individuals with the expertise to fortify enterprise security against diverse cyber threats. Joining this course unlocks the strategic insights behind mitigation and empowers individuals and professionals to implement robust defense mechanisms within organizational frameworks.
TRAINING CALENDAR of Upcoming Batches For Security+ SY0-701
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 03-May-2025 | 08-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 25-May-2025 | 05-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 28-Jun-2025 | 03-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 26-Jul-2025 | 31-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)