OSI Model: A Comprehensive Guide for Exam and Interview
The Open Systems Interconnection (OSI) model is a fundamental framework for understanding networking systems, breaking down their functions into seven distinct layers. It is vital for ensuring interoperability and compatibility across different technologies. By familiarizing themselves with the OSI model, IT and networking professionals can enhance their ability to communicate complex network problems and solutions more effectively, thereby streamlining collaboration and innovation in the field. This model serves as the cornerstone of network theory, enabling professionals to adapt to new technologies and protocols while maintaining a solid foundation in networking principles.

OSI Model Layers
Created by the International Organization for Standardization (ISO) towards the end of the 1970s, the OSI model simplifies the intricate task of communication between computers by segmenting it into seven unique layers. Each layer is assigned a particular role and interacts with the layers immediately adjacent to it. The layers, arranged from the lowest to the highest, include Physical, Data Link, Network, Transport, Session, Presentation, and Application.
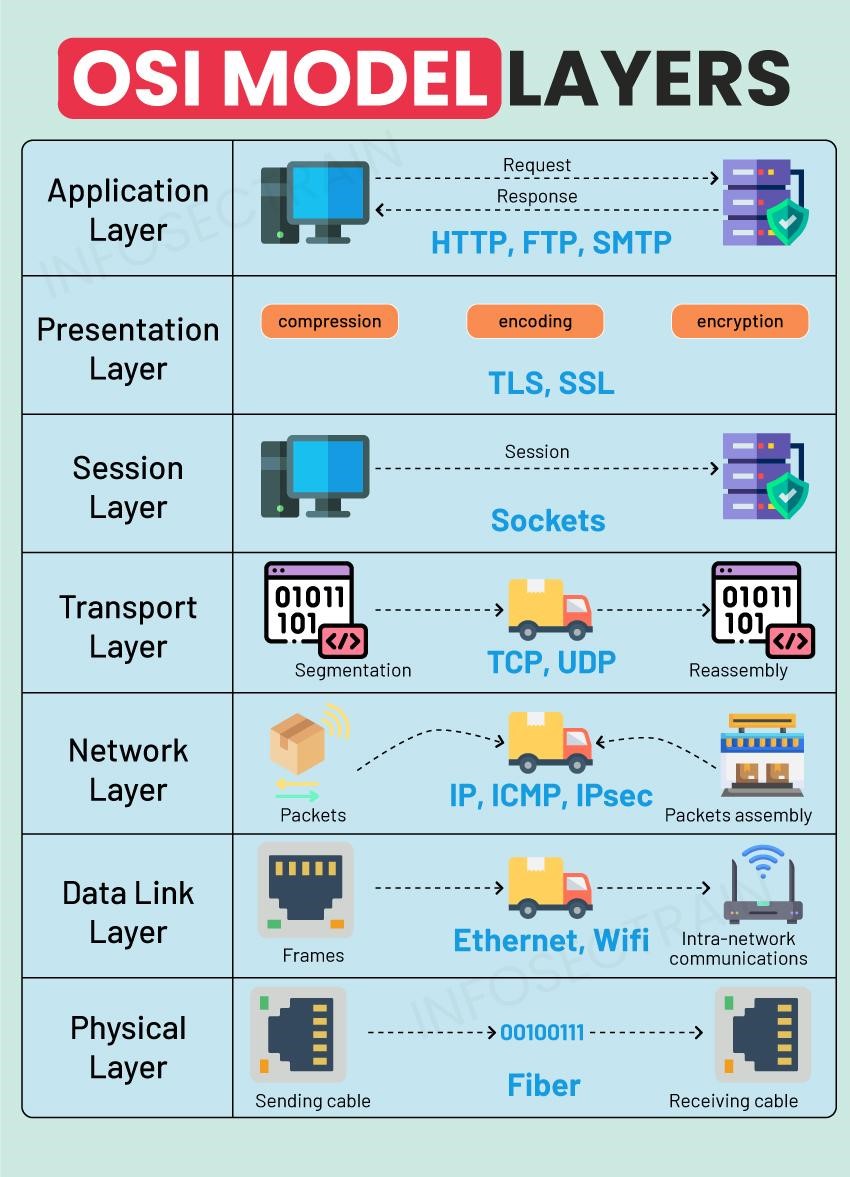
1. Physical Layer (Layer 1)
Function: The Physical Layer is responsible for the physical and electrical connections between devices. It transmits and receives raw binary data over a physical medium.
Example: When a computer connects to a network through an Ethernet cable (Cat5, Cat6), the Physical Layer handles the transmission of binary data through electrical signals along the cable.
Physical Layer Interview Questions
- How do different types of cables (e.g., coaxial, fiber optic) affect data transmission at the Physical Layer?
Different types of cables can significantly affect data transmission in terms of speed, distance, and susceptibility to interference:- Coaxial cables:
- Resistant to electromagnetic interference
- Suitable for cable TV and Ethernet
- Bulkier and less flexible
- Fiber optic cables:
- Transmit data via light
- High speeds, long distances
- No electromagnetic interference
- Ideal for backbone networks and long-distance communication
- Twisted pair cables (Ethernet cables):
- Common in LANs and telephone connections
- Available in shielded and unshielded versions
- Variable electromagnetic interference vulnerability
- Different speeds and distance capabilities
- Coaxial cables:
- Can you explain how Ethernet and Wi-Fi protocols operate at the Physical layer and their roles in data communication?
- Ethernet:
- Works at Physical and Data Link layers
- Uses electrical signals, timings, and connectors
- Supports coaxial, twisted pair, and fiber optic cables
- Speeds vary between 10 Mbps and 100 Gbps
- Wi-Fi:
- Operates at Physical and Data Link layers
- Transmits data using radio waves
- Protocols specify frequency bands (2.4 GHz, 5 GHz) and modulation techniques
- Speeds vary from 11 Mbps (802.11b) to several Gbps (802.11ax)
- Facilitates wireless communication and mobility
- Ethernet:
2. Data Link Layer (Layer 2)
Function: This layer ensures error-free data transfer between network nodes over the physical layer, handling error detection and correction. It’s split into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC).
Example: A network switch operates at the Data Link Layer, using MAC addresses to forward data to the correct destination on a local network.
Data Link Layer Interview Questions
- Explain the difference between MAC addresses and IP addresses.
- A MAC address is a unique hardware identity assigned to each device on a network to distinguish it from others. It operates at the Data Link layer and is used for local network communication.
- An IP Address is a digital identifier given to each device on a network that communicates using the Internet Protocol (IP). It operates at the Network layer and is used to identify devices across different networks and route data.
- How does the Data Link Layer handle error detection and correction?
The Data Link Layer uses mechanisms like checksums, Cyclic Redundancy Check (CRC), and parity bits to detect errors. For error correction, it uses techniques like retransmission of corrupted frames or sophisticated error correction codes that allow the receiver to correct errors without needing a retransmission.
- Can you explain the difference between flow control and error control?
- Flow control is a method for managing the pace of data transmission between two endpoints. This process prevents a fast sender from flooding a slow receiver by ensuring the data transmission rate does not surpass the receiver’s capacity to process the data.
- Error control involves detecting and correcting errors that occur in the data transmission process. It ensures that the data received is the same as the data sent despite any potential transmission errors.
- Explain the differences between the Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP) in the context of the Data Link Layer. How do they facilitate network communication?
- The Address Resolution Protocol (ARP) connects an IP address with a MAC address. This protocol is utilized when a device needs to identify the MAC address of another device on the same network for which it only has the IP address.
- The Reverse Address Resolution Protocol (RARP) protocol maps a MAC address to an IP address. It is typically used by devices not knowing their IP address when they join a network. RARP helps these devices obtain their IP addresses using their known MAC addresses.
3. Network Layer (Layer 3)
Function: The Network Layer is responsible for data packet routing, logical addressing, and the handling of routing protocols. It manages the delivery of packets from the source to the destination across multiple networks (routing).
Example: A router functions at the Network Layer, using IP addresses to direct packets between different networks towards their final destination.
Network Layer Interview Questions
- Describe how a router works at the Network Layer to route data.
A router examines the destination IP address in a packet’s header, uses routing tables to determine the best route for the packet, and forwards it toward its destination through the appropriate interface. It operates at the Network Layer, directing traffic based on IP addresses.
- What is the significance of routing protocols in the Network Layer?
Routing protocols (like OSPF, BGP) enable routers to build and maintain routing tables. They dynamically communicate network topology changes and determine the most efficient path for data packet delivery across different networks, ensuring efficient and reliable data routing.
- Can you define unicasting, multicasting, and broadcasting in a network?
- Unicasting: Sending data from one sender to one specific receiver.
- Multicasting: Sending data from one sender to multiple specified receivers.
- Broadcasting: Sending data from one sender to all possible receivers in the network segment.
- How do IP, ICMP, and IGMP work together at the Network layer to manage data delivery and network diagnostics?
- The Internet Protocol (IP) is a crucial protocol that guides data packets from their source to their designated destination through multiple networks, leveraging IP addresses to determine their path.
- Internet Control Message Protocol (ICMP) is used to send diagnostic messages and report error, helping manage and troubleshoot network issues.
- Internet Group Management Protocol (IGMP) manages multicast group memberships, allowing routers to efficiently send multicasting data to groups of interested receivers.
4. Transport Layer (Layer 4)
Function: This layer provides reliable, transparent data transfer between end systems. It’s responsible for error recovery, flow control, and end-to-end data transfer. It includes TCP (connection-oriented) and UDP (connectionless) protocols.
Example: TCP ensures that data sent over the internet reaches the destination in the correct order and without errors (e.g., an email). UDP is used for streaming video online, where speed is more critical than perfect accuracy.
Transport Layer Interview Questions
- Compare and contrast TCP and UDP in terms of reliability and speed.
Reliability:- TCP is highly reliable as it establishes a connection through a handshake process, ensures data is received in order, and resends lost packets.
- UDP is less reliable, does not guarantee order or delivery, and does not resend lost packets.
Speed:
- TCP is slower than UDP due to its mechanisms for ensuring data integrity, such as error checking, flow control, and congestion control.
- UDP is faster as it lacks the overhead of connection setup and error correction and is stateless, making it suitable for real-time applications where speed is critical.
- How does the Transport Layer handle flow control and congestion?
- Flow control: Protocols like TCP manage it at the Transport Layer to prevent a fast sender from overwhelming a slow receiver. Techniques include windowing, where the sender adjusts the data transmission rate based on the receiver’s ability to process the data.
- Congestion control: Congestion control is also a responsibility of protocols like TCP. It aims to prevent congestion by adjusting the data transmission rate based on the network’s current state. Methods include slow start, congestion avoidance, fast retransmit, and fast recovery, which help to optimize data transmission rates and prevent packet loss due to network congestion.
5. Session Layer (Layer 5)
Function: The Session Layer establishes, maintains, and terminates connections between applications. It manages sessions by initiating the opening and closing of connections between end-user applications.
Example: When you log into a web application, the Session Layer manages the connection between your browser and the server, ensuring that the session remains consistent.
Session Layer Interview Questions
- Can you explain the concept of session establishment, maintenance, and termination?
Session layer management in web applications:- Session establishment: Initiates a user session with a unique ID upon login.
- Session maintenance: Keeps the session alive through cookies or URL rewriting, tracking user actions.
- Session termination: Ends the session upon logout or inactivity, clearing session data.
- Explain the function of the Point-to-Point Tunneling Protocol (PPTP) and how it facilitates VPN connections at the Session layer.
- Function: Enables VPN connections by encapsulating PPP frames in IP datagrams, operating at the Session Layer.
- VPN connections: Establishes a secure tunnel between a VPN client and server, allowing encrypted communication and remote access to private networks.
6. Presentation Layer (Layer 6)
Function: This layer translates data between the application layer and the network. It’s responsible for data encryption/decryption, compression, and ensuring that data is in the correct format for the receiving application.
Example: When encrypting an email for sending, the Presentation Layer takes your message and encrypts it before it’s sent over the network.
Presentation Layer Interview Questions
- Explain the role of the Presentation Layer in data encryption and compression.
- Data encryption: Converts plain text into a scrambled format (cipher text) to protect the data’s confidentiality during transmission. This layer applies encryption algorithms to data before it’s sent over the network and decrypts received data back into its original form.
- Data compression: Reduce data size to save bandwidth and improve transmission speed. The Presentation Layer compresses data before sending and decompresses received data.
- How does the Presentation Layer facilitate data format translation between different systems?
The Presentation Layer translates data between the format the network requires and the format the application uses. It ensures different systems can communicate by converting data from one coding scheme (e.g., ASCII, EBCDIC) to another, making data readable across diverse systems.
- Discuss how Secure Sockets Layer (SSL) and Transport Layer Security (TSL) protocols work at the Presentation layer to ensure secure data transmission.
SSL and TLS are designed to secure network communications. While they are commonly linked to the Transport Layer, their functionalities are more in line with the Presentation Layer, involving encryption, maintaining data integrity, and verifying the authenticity of the communication parties. These protocols safeguard data transmitted online, protecting it against interception and alteration. They ensure the secure exchange of information by employing asymmetric and symmetric encryption methods to establish a secure connection, authenticate the entities involved, and preserve the accuracy and completeness of the transmitted data.
7. Application Layer (Layer 7)
Function: The Application Layer is where network services are provided to end-users. It provides a user interface and facilitates interaction with the network (e.g., web browsers and email clients).
Example: Using a web browser to access a website involves the Application Layer, where HTTP or HyperText Transfer Protocol is used to fetch pages from a web server and display them to the user.
Application Layer Interview Questions
- Describe how the Application Layer enables various network functionalities, such as email, file transfers, and web browsing.
- Email: It utilizes protocols like SMTP for sending emails and IMAP or POP3 for receiving emails, enabling users to exchange messages through email clients or web interfaces.
- File transfer: This method employs FTP to transfer files between systems, allowing users to upload or download files from servers.
- Web browsing: Uses HTTP or HTTPS to request and display web pages, facilitating access to the World Wide Web.
- How does the Application Layer interact with the Presentation Layer to deliver services to the user?
The Application Layer communicates with the Presentation Layer to ensure that data is in the correct format for the application. For example, the Presentation Layer might encrypt data for secure HTTP transmission (HTTPS) or format data as HTML for web browsing, which the Application Layer then sends or receives.
- How do HTTP, FTP, and SMTP provide different services at the Application layer?
- Hypertext Transfer Protocol (HTTP): Specifies how web browsers and servers interact to request and deliver web content.
- File Transfer Protocol (FTP): Provides a protocol for transferring files over a network, supporting operations like upload, download, delete, and directory listing.
- Simple Mail Transfer Protocol (SMTP): A protocol for transmitting email messages from one server to another, facilitating the movement of emails across the Internet.
Importance of the OSI Model
The OSI model is a blueprint for network communication that helps IT professionals understand how different network protocols interact and operate. It provides a universal language that describes the functions of a networking system. Understanding the OSI model can help diagnose network problems and improve the design and implementation of new networking solutions.
Preparing for Exams and Interviews
When preparing for exams or interviews, it’s essential to memorize the OSI layers and understand their functions and how they interact with each other. Consider the following tips:
- Use mnemonics to remember the order of the layers. For example, “Please Do Not Throw Sausage Pizza Away” (Physical, Data Link, Network, Transport, Session, Presentation, Application).
- Understand real-world applications and examples of each layer.
- Be prepared to explain how data flows through each layer from source to destination.
- Practice diagnosing network issues by identifying at which OSI layer a problem might occur.
CCNA Training with InfosecTrain
For individuals pursuing careers in networking, IT, or cybersecurity, mastering the OSI Model is crucial. It offers a structured method for comprehending the complexities of network communications, facilitating simpler network design, implementation, and troubleshooting. As you prepare for exams or interviews, it’s important to constantly revise the OSI model’s layers, their functions, and how they apply in real-world scenarios. A profound knowledge of the OSI model not only improves your troubleshooting skills but also boosts your capability to clearly convey your networking expertise to potential employers.
For further learning and preparation, consider exploring InfosecTrain’s CCNA certification training course to deepen your knowledge.







 1800-843-7890 (India)
1800-843-7890 (India)