Password Cracking: Techniques in CEH Module 6
Module 6 of the Certified Ethical Hacker (CEH) course delves into system hacking. This module is essential because it covers an attacker’s strategies to breach systems, primarily through password cracking. Password cracking is the method of guessing or deciphering a user’s password without their consent. Ethical hackers must master this technique not for malicious purposes but to discover and reinforce security vulnerabilities.

Furthermore, Module 6 addresses the comprehensive approach hackers take to compromise systems. They start by gathering information through techniques like system enumeration, footprinting, and vulnerability analysis. With this information, they exploit weaknesses through system hacking. Understanding an attacker’s objectives is crucial—it leads to questions about the specific methods and tools they use to breach systems. Password cracking is a key technique for gaining unauthorized access to targeted systems.
Phases of Ethical Hacking

As we can see in the above image, the third phase is gaining access. The goal of this phase is to gain access to the system. Techniques used include password cracking, taking advantage of known software flaws, and social engineering.
Password Cracking
Password cracking is a basic skill for attackers and those who work in computer security to investigate digital breaches. Most systems use a username and password to let the right person in, and even when there’s an extra layer of security, you often still use a password.
Microsoft Authentication
When users log into a Windows computer, it uses a few steps to check who they are based on Microsoft’s security measures.
- Security Accounts Manager (SAM) Database: A key part of this is the Security Accounts Manager (SAM) Database, where Windows keeps user account details and passwords stored securely (as hashed codes, which are scrambled versions of the passwords). The system locks this database to prevent unauthorized access, especially when the computer is running, adding an extra layer of protection for your password information.
SAM Database Authentication Process: Windows Operating Systems keep user passwords in a special database file called the Security Account Manager (SAM) located in the system directory (think of it as a secure cabinet in a well-guarded office). This file stores scrambled versions of passwords (hashes) using either LM (an older method) or NTLM (a newer method that’s tougher to crack).
For example, if a user’s name is KD and his password is “test,” the SAM file doesn’t store the word “test” but rather a complex code that represents it, like “OCB6948805E797BE2A82807973B89537.” This code is unique to KD’s password.

- NTLM Authentication: NTLM is a basic way that Windows checks if you’re allowed to log in. It uses a type of security check that doesn’t follow a strict set of rules, so it might not work the same in every situation. It has two parts: scramble your password into a secret code before saving it.
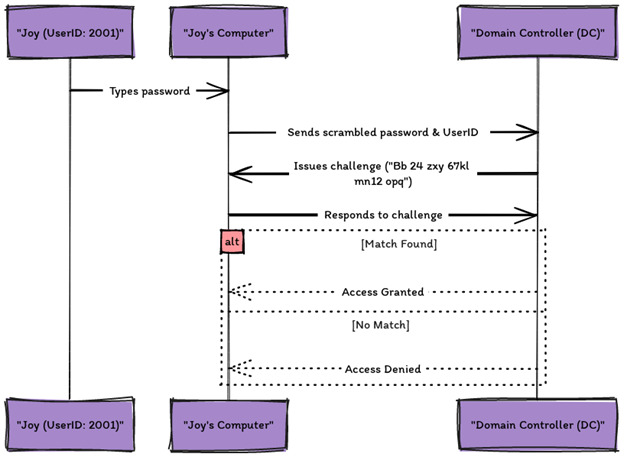
NTLM Authentication Process: NTLM is a way Windows checks your login, with three versions offering different security levels. When you log in, your password gets scrambled and checked against the network’s stored version.
Example: Consider a user, let’s call them “Joy,” with a user ID of “2001,” trying to log in. When Joy types their password, the computer scrambles it using NTLM’s secret codes. It might look something like “Joy:2001:NO PASSWORD**************:AD34FAD1234FED12345ABCDE:::”. Then, the computer sends this scrambled password to the network’s domain controller, which is like a bouncer checking IDs at a club. The domain controller challenges the computer with a secret code, say, “Bb 24 zxy 67kl mn12 opq.” The computer responds, and if the bouncer finds the response matches what it has on file, Joy is allowed in. If not, no entry!
- Kerberos Authentication: Kerberos is a more secure system for when your computer talks to other computers or servers. It uses secret codes that only the two sides of the conversation know, and it double-checks both sides to ensure they’re legit. It’s also good at preventing sneaky spying or someone trying to trick the system into thinking they’re you.
- Kerberos Authentication Process: Kerberos is an authentication protocol that secures client and server transactions using secret-key cryptography. It authenticates users and servers to each other and shields their communication from replay attacks and interception. The process involves a client requesting access from an authentication server, receiving a ticket-granting ticket (TGT) for services, and then using this ticket to get a service-specific ticket from the ticket-granting server (TGS). Finally, with this ticket, the client can access the desired service on the server, with both sides assured of the other’s identity.

To be Continued…..
CEH with InfosecTrain
InfosecTrain stands out as a premier training institute offering cost-effective solutions. We welcome you to embark on an enriching learning experience with our field specialists to deepen your knowledge of the Certified Ethical Hacker training program. You have the flexibility to choose between live sessions led by instructors or self-directed courses, enabling you to progress through your training at your own pace.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Jul-2025 | 16-Aug-2025 | 09:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)