Ransomware- A reality check (Part 3)
- Ransomware- A reality check (Part 1)
- Ransomware- A reality check (Part 2)
- Ransomware- A reality check (Part 3)
Interesting statistics about Ransomware
Let’s take a look at the latest interesting statistics of Ransomware attacks:
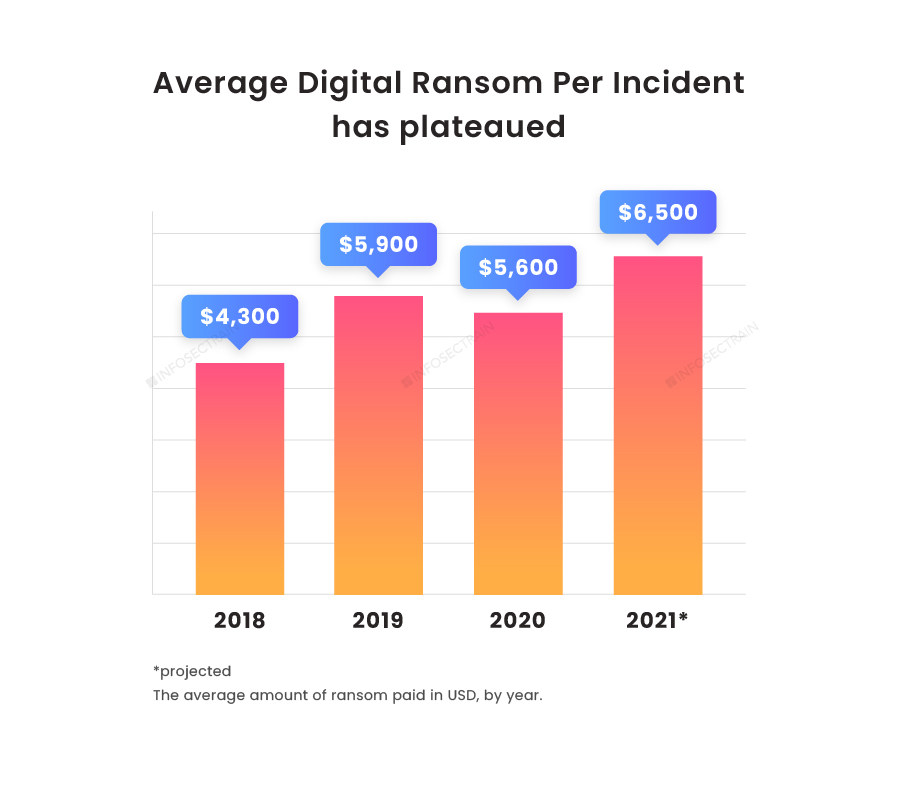
Graph One: The average ransom payment has increased gradually over the years, and interestingly, hackers tend to duplicate successful attacks and hit the victims repeatedly.
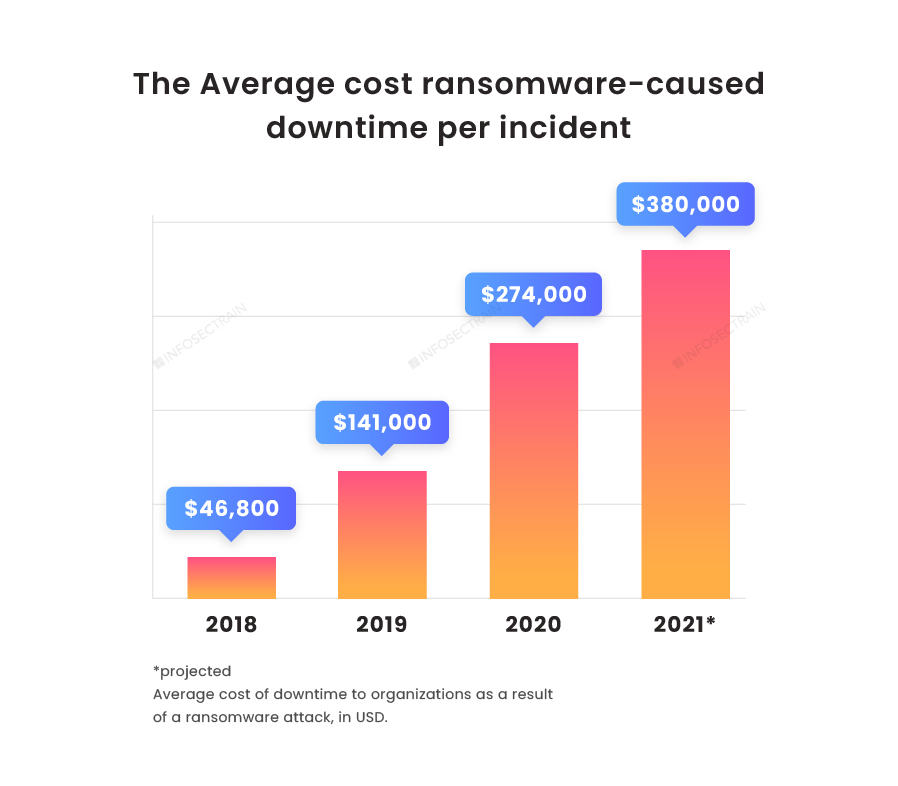
Graph Two: Most companies have experienced data loss and major downtime due to ransomware attacks. The overall cost of Ransomware has doubled in recent years.
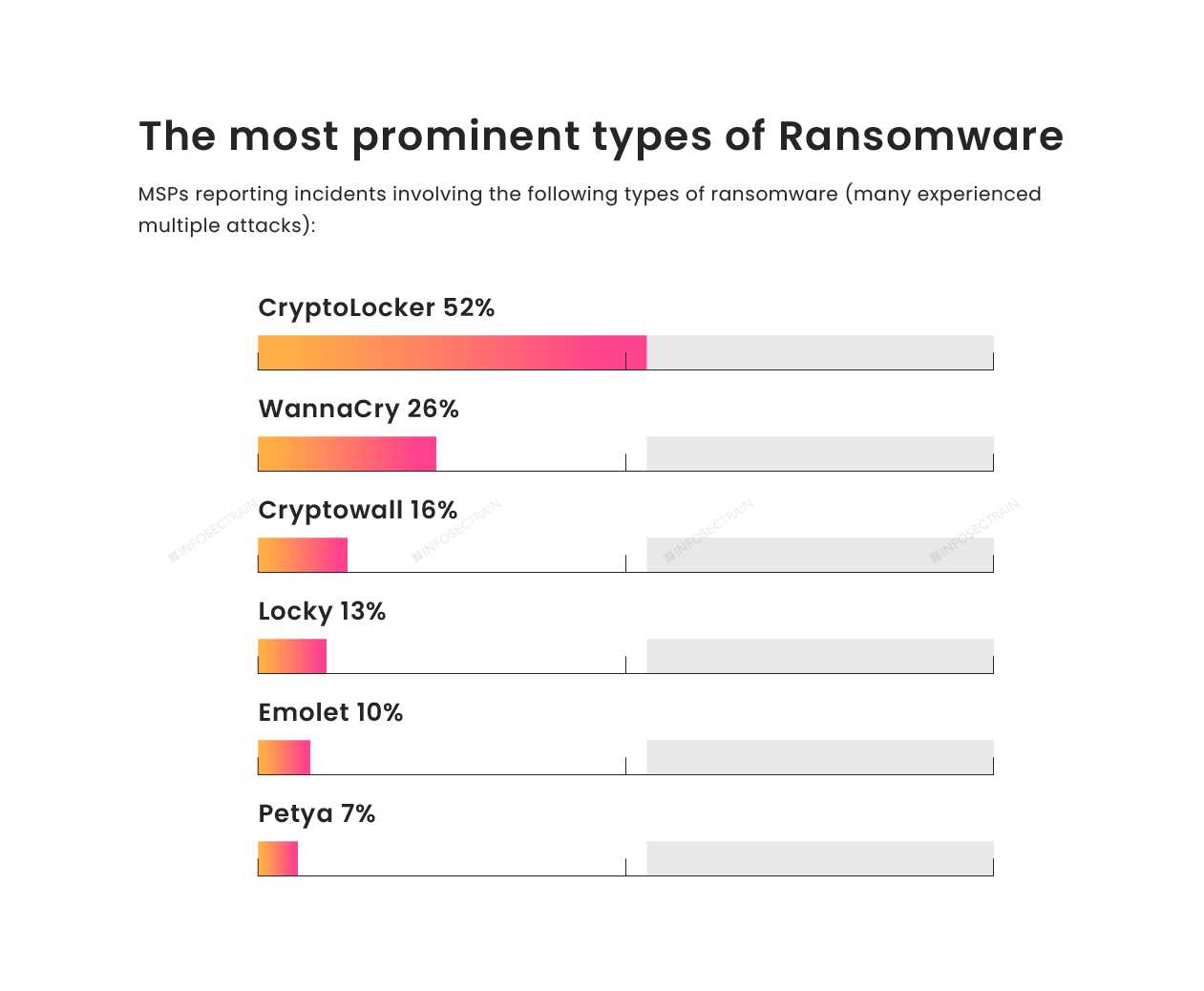
Graph Three: Most sophisticated strains are raised.
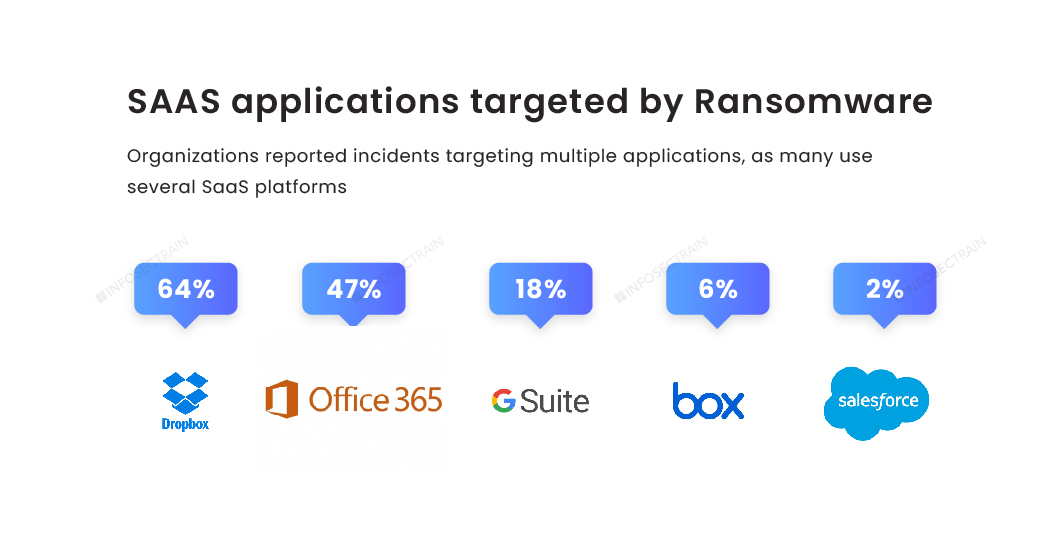
Graph Four: There is a rise in attacks on SAS-based applications.
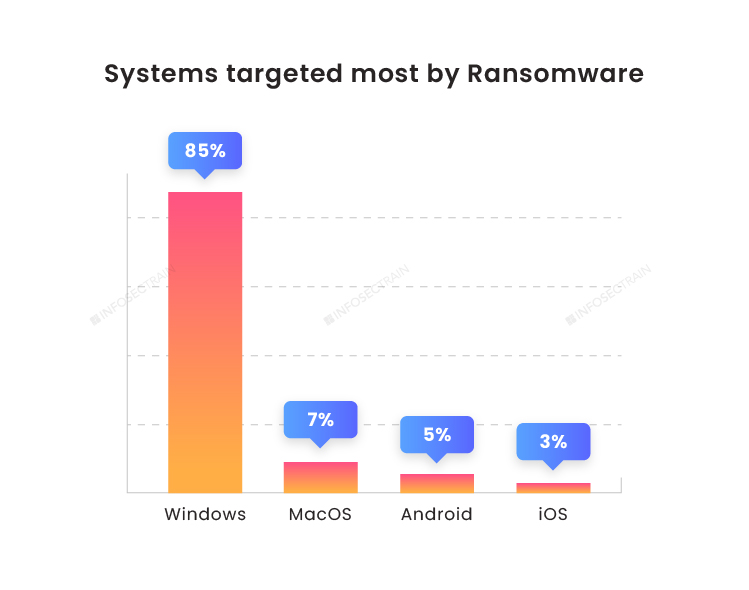
Graph Five: Windows OS are being targeted frequently. As windows are primarily used more and necessary updates are not done, that leads to vulnerable sections.
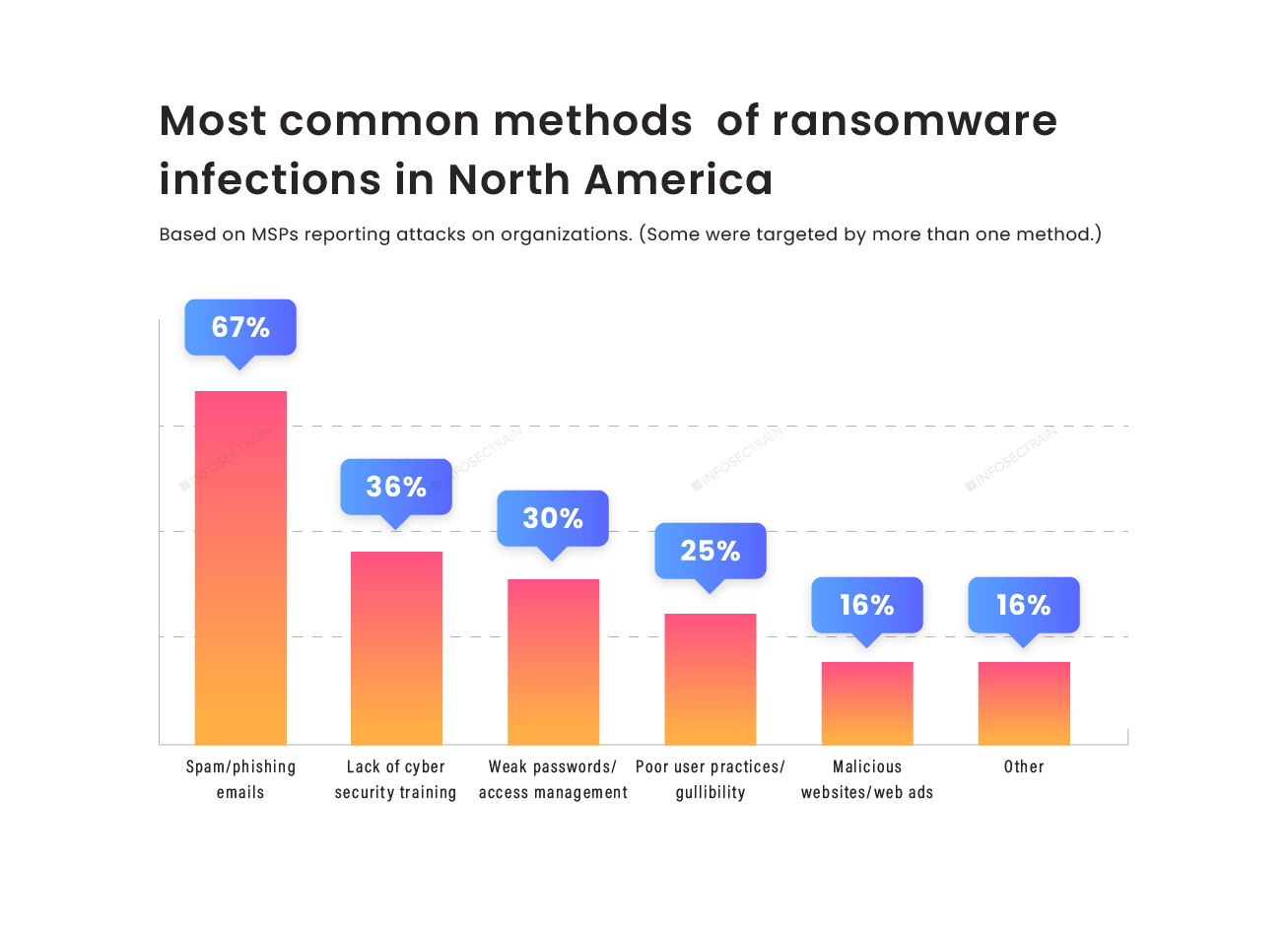
Graph Six: Emails are the primary method for all types of cyberattacks, and people are still falling victim to your malicious social engineering and lack of training in basic cybersecurity practices, use of weak passwords, lack of proper access management, and poor awareness.
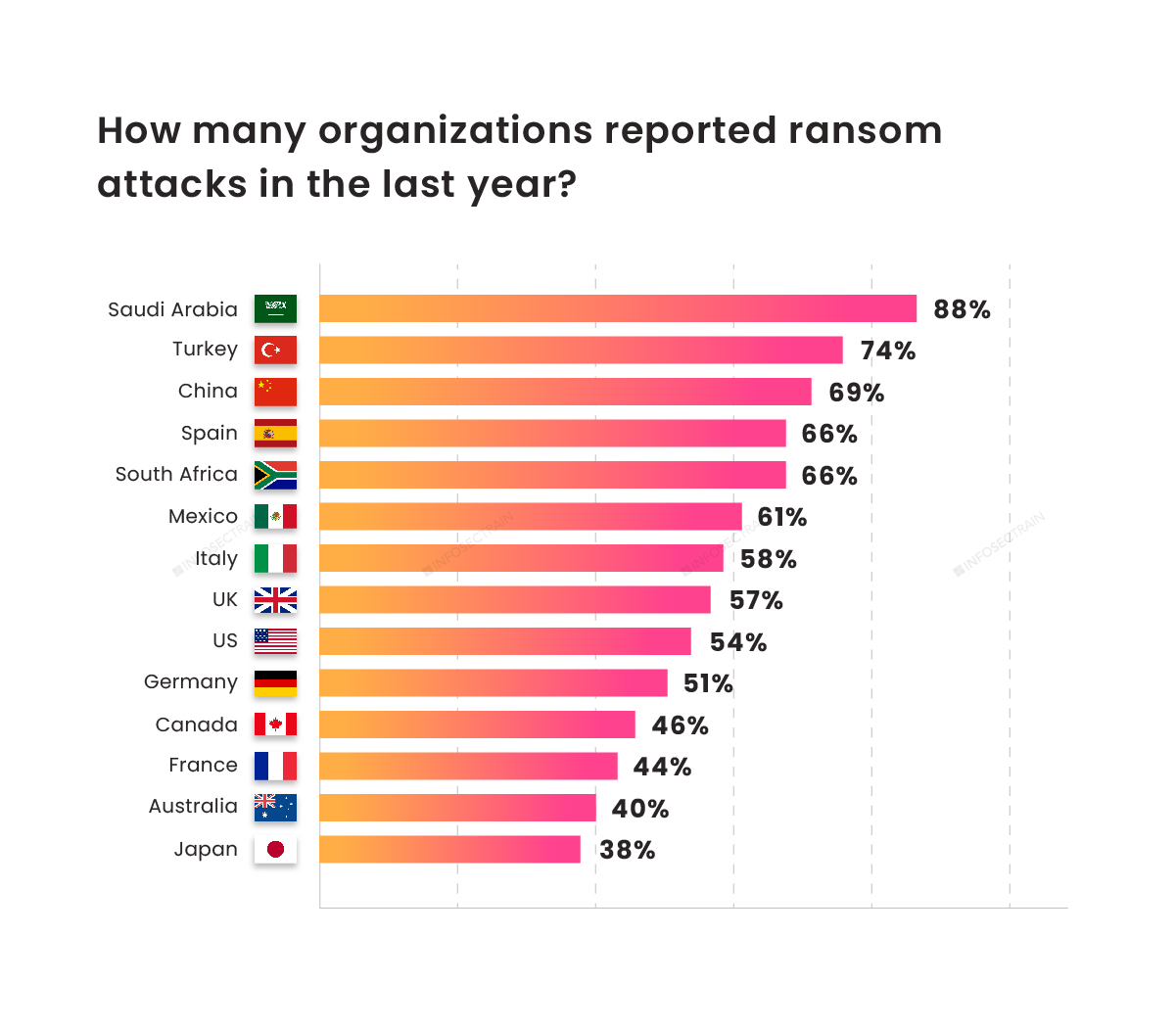
Graph Seven: Even the countries with access to the most advanced security technologies with considerable higher awareness are also falling victims to these kinds of digital extortion.
Graph Eight: Individual users and businesses will continue to be targeted, and URLs embedded in emails will remain the number one way for computers to become infected.
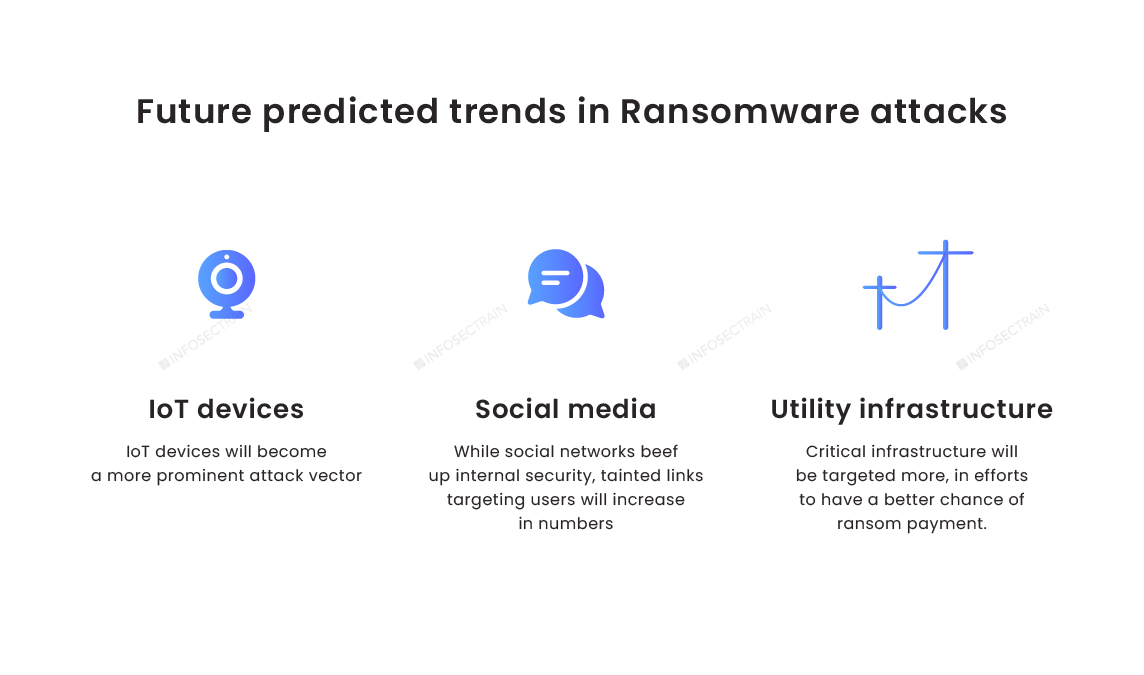
The annual share of ransomware attacks experienced by the organizations has been raised to 68% by 2021 over the world. The best defense over Ransomware is for users to understand what it is, how it infects, and what to do once it happens.
The What’s of Ransomware
Let’s have a look at some interesting questions on Ransomware attacks:
What is the most prominent ransomware payout made?
$40 million was the most prominent ransomware payout by an insurance company. The attackers demanded 100 million, but they received around $40 million.
What is the current average ransom fee requested?
Around $ 200,000
What is the average downtime a company faces after a ransomware attack?
It depends on the company and sophistication of the attack. A company’s downtime whenever they are attacked with ransomware is 21 days.
What is the largest healthcare data breach in history?
Ireland Anthem Breach in 2015: 80 million people were affected.
What is the most common ransomware attack tactic?
- Email phishing campaigns
Which ransomware variant has affected over 100 financial institutions?
LokiBot: More than $2 million
How much did FedEx pay for the NotPetya ransomware attack?
$300 million
Which Chief Executive paid hackers $4.4 million in bitcoin after receiving a ransom note?
CEO Blount- Colonial Pipeline, an oil sector of the southern part of the US, underwent an operational technology attack.
What is the common type of ransomware attack in India?
Crypto ransomware- they used to mine cryptocurrency.
What are the top three ransomware attacks in India?
Telangana and AP Power Utilities Hacked, UHBVN Ransomware Attack.
Response- NIST Incident Response Framework
National Institute of Standards and Technology (NIST) is an American government department that defines an Incident Response Framework. If you are affected by the Ransomware attack, follow the steps to ease your hard times.
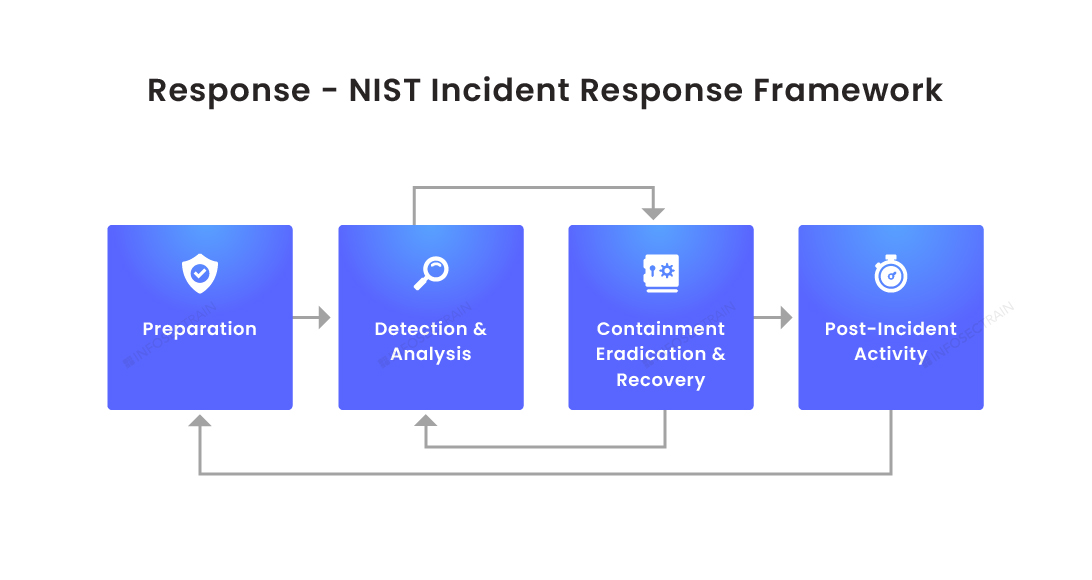
They define four steps:
Step1: Preparation
Planning is a part of countermeasures. Notify your higher officials if you have experienced any unusual activity on your system.
For instance: I would call the manager immediately if I’m not able to log in to my work system.
Step2: Detection & Analysis
The following are the detection and analysis techniques that should be implemented as a part of the action plan:
- Vulnerability Assessment
- Penetration Testing
- Frequent checks
- VAPT
AntiVirus actively monitors and scans your system in the background when you run monthly or weekly scans. For example, many files get renamed once, so it is not a usual activity. The end-user behavior analytics performs these detections to understand the user’s behavior and detect anything malicious. Few organizations go on and extend to monitor the traffic at the packet level. So, these are the detection mechanisms that have to be implemented.
Step3: Containment Eradication and Recovery stage.
If a user’s computer is infected, then isolate that particular system from the network to prevent it from spreading.
Isolate the computer, analyze and take a forensic image of the computer, understand what went wrong, and then eradicate the infected virus. Finally, recover by implementing a new firewall.
Step4: Post-incident activity
It is also known as lessons learned; it means analyzing what went wrong. Analyze the reason for the attack to eradicate the threat. You find out there is a vulnerability, you patch that vulnerability in that system and even in the entire network.
If they did not patch the vulnerability that the attacker exploited, that could allow the attacker to affect the same way with the same ransomware again.
SANS Incident Response Plan
SANS has also framed an Incident Response Plan, which is quite similar to NIST Incident Response Framework.

- Prepare
- Identify
- Containment
- Eradication
- Recovery
- Lessons learned
Final Words
We hope this blog has covered valuable information about Ransomware and its reality. Furthermore, if you want to explore, you can refer to the YouTube video:
InfosecTrain provides professional training, certification & consulting services related to all areas of Information Technology and Cyber Security. We offer a complete instructor-led training program for all cybersecurity and information security certification courses that would help you to upskill your abilities.









 1800-843-7890 (India)
1800-843-7890 (India)