Risk Management Lifecycle
In the unpredictable landscape of modern business, where risks can arise from disruptive technological innovations to evolving regulatory landscapes, a proactive approach is essential. These risks pose significant threats to operations and impact long-term sustainability and strategic objectives. Navigating such unpredictable situations in this ever-changing world requires a structured and proactive approach. This is precisely where the Risk Management Lifecycle (RML) emerges as a critical organizational framework. It provides a systematic method to identify, assess, mitigate, and monitor risks as they evolve and multiply. Mastering this lifecycle is beneficial and essential for businesses aiming to maintain resilience and drive growth amidst constant change.

What is Risk Management?
Risk management is a structured approach for detecting, assessing, prioritizing, and mitigating potential risks that could impact an organization’s goals, initiatives, operations, or assets. This approach includes the methodical assessment of recognizing threats, evaluating their likelihood and potential consequences, prioritizing them based on severity, and implementing strategies to reduce or manage those risks.
5 Steps: Risk Management Lifecycle
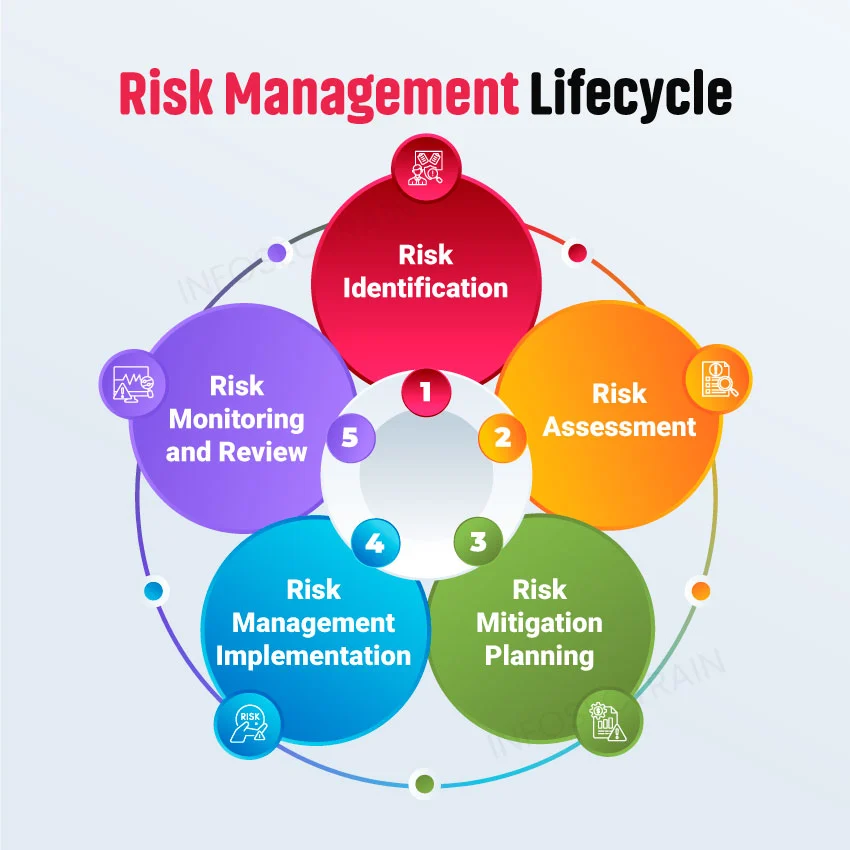
1. Risk Identification
Risk identification is the foundational stage in the risk management lifecycle where potential risks that could impact an organization or project are systematically identified. This process involves:
- Documentation Review: Analyzing project documents, contracts, and historical data to identify potential risks.
- Brainstorming Sessions: Teams gather to brainstorm potential risks based on their expertise and experience.
- Checklists: Using standardized checklists to ensure comprehensive coverage of potential risks.
- SWOT Analysis: Evaluating strengths, weaknesses, opportunities, and threats to detect potential risks.
- Expert Interviews: Consulting with subject matter experts to identify risks related to their areas of specialization.
2. Risk Assessment
Risk analysis involves evaluating identified risks to determine their likelihood, impact, and severity. Key factors considered in this stage include:
- Probability Assessment: Determining the likelihood of each risk occurring based on historical data, expert judgment, and statistical analysis.
- Impact Assessment: Assessing the potential consequences of each risk on project objectives, such as quality, cost, and reputation.
- Risk Prioritization: Prioritizing risks based on their probability and impact to focus resources on the most critical ones.
- Qualitative and Quantitative Analysis: Using qualitative techniques like risk matrices and quantitative methods like Monte Carlo simulation to analyze risks.
3. Risk Mitigation Planning
Risk mitigation planning involves developing strategies and tactics to reduce the impact of identified risks. These strategies may vary depending on the nature of the risk and the organization’s objectives. Key components of risk mitigation strategies include:
- Risk Tolerance: Determining the level of risk that the organization is willing to accept or tolerate.
- Risk Avoidance: Eliminating the risk by changing project scope, requirements, or approach to prevent the risk from occurring.
- Risk Transference: Shifting risk to third parties through insurance, contracts, or partnerships.
- Risk Mitigation: Deploying strategies to reduce the likelihood or impact of risks, including contingency planning, redundancy, process improvements, or other proactive actions.
- Risk Acceptance: Acknowledging the risk’s existence and its potential consequences without taking specific action, either due to the higher cost of mitigation compared to benefits or because the risk aligns with acceptable tolerance levels.

4. Risk Management Implementation
Risk management implementation involves putting risk management plans into action. This stage includes engaging stakeholders, communicating risk information, and establishing monitoring and control mechanisms.
- Stakeholder Engagement: Involving stakeholders throughout the implementation process to secure their buy-in and support.
- Communication Strategies: Establishing clear communication channels to disseminate information about risks and mitigation efforts.
- Monitoring and Control: Implementing mechanisms to monitor risks and their mitigation strategies, such as regular progress reviews and performance indicators.
- Adaptation and Adjustment: Adjust risk management plans as needed based on new information or changing circumstances.

5. Risk Monitoring and Review
Risk management review and monitoring involve ongoing assessment of risk management plans to ensure their effectiveness. This stage includes:
- Regular Reviews: Conducting periodic reviews of risk management plans to assess their alignment with project objectives and emerging risks.
- Performance Metrics: Establishing metrics to track the effectiveness of risk mitigation efforts and identify areas for improvement.
- Risk Reporting: Providing regular reports to stakeholders on risk trends, events, and the overall status of risk management activities.
- Lessons Learned: Capturing lessons learned from risk management experiences to inform future projects.
- Root Cause Analysis: Examining the root causes of risk events to identify systemic issues and prevent recurrence.
CISSP Training with InfosecTrain
Gain comprehensive insight into Risk Management through expert instruction from InfosecTrain’s CISSP training course. This course offers a thorough understanding of Risk Management core concepts, methodologies, and best practices, delivered by seasoned instructors with extensive expertise in the field. Understand the intricacies of identifying, assessing, and mitigating risks to safeguard organizational assets and achieve business objectives.
TRAINING CALENDAR of Upcoming Batches For CISSP
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 27-Apr-2025 | 02-May-2025 | 09:00 - 18:00 IST | Weekend-Weekday | Classroom Hyderabad | [ Close ] | |
| 03-May-2025 | 08-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 05-May-2025 | 22-May-2025 | 07:00 - 12:00 IST | Weekday | Online | [ Close ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 01-Jul-2025 | 01-Aug-2025 | 08:00 - 10:00 IST | Weekday | Online | [ Open ] | |
| 07-Jul-2025 | 12-Jul-2025 | 09:00 - 18:00 IST | Weekend-Weekday | Classroom Bengaluru | [ Open ] | |
| 30-Aug-2025 | 05-Oct-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)