Securing Integrity: Key Concerns & Prevention
In today’s world, where our online presence can reach far and wide instantly, the concept of integrity has become more critical. From data breaches to ethical dilemmas, businesses and individuals face various data integrity concerns, which must be addressed and acted upon.

As we navigate through this intricate landscape, understanding what integrity truly means in the digital era is essential. Integrity is all about being honest, transparent, and adhering to ethical principles, especially when it comes to technology and information interactions. Integrity concerns are present in every aspect of our online existence, whether it is protecting user data from unauthorized access or ensuring fairness in algorithmic decision-making.
Integrity Concerns and Prevention Measures
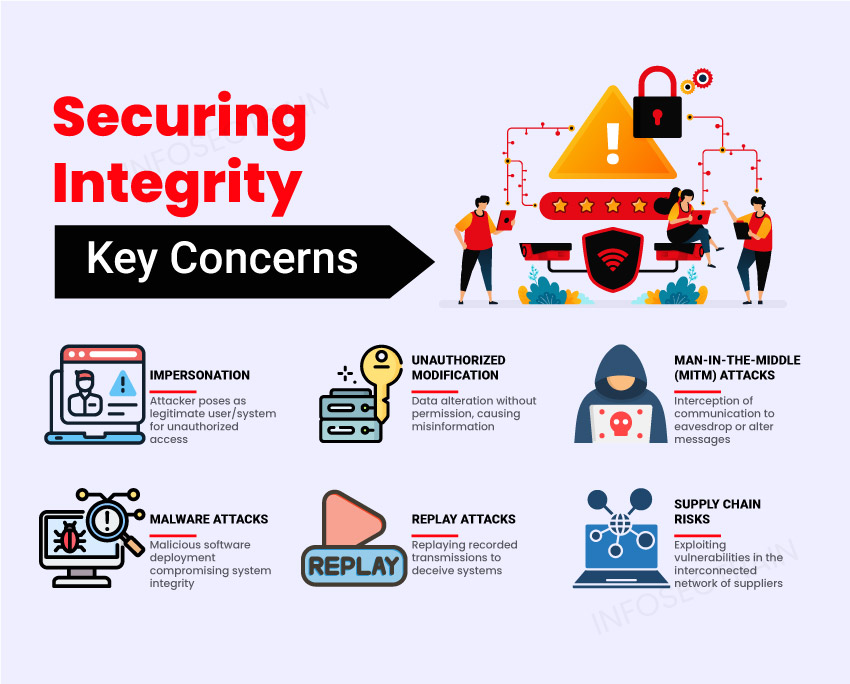
1. Impersonation: Impersonation occurs when an attacker pretends the identity of a legitimate user or entity to obtain unauthorized access to systems, sensitive information, or other valuable resources. This can happen through phishing emails, social engineering tactics, or exploiting weak authentication mechanisms.
Example: An attacker sends a phishing email pretending to be a trusted colleague, requesting sensitive information or credentials to access company systems.
Prevention Measures: User education plays a crucial role in preventing impersonation attacks. Training users to recognize phishing attempts, verify the authenticity of requests, and use of strong authentication measures such as Multi-factor Authentication (MFA) can significantly reduce the risk of unauthorized access through impersonation.
2. Unauthorized Modification: Attackers may gain access to systems or data and make unauthorized changes, such as altering configurations, modifying files, or tampering with critical settings. This can lead to data manipulation, service disruption, data corruption, or unauthorized access.
Example: An attacker with administrator privileges could access a company’s database server and modify customer records to change billing information or delete transaction logs.
Prevention Measures: Enforcing the “principle of least privilege” limits users’ access rights to only those required for their roles. By granting minimal permissions, organizations reduce the potential impact of unauthorized modifications.
3. Malware Attacks: Malware attacks involve the deployment of malicious software designed to compromise the integrity of systems or data. Some common types of malware include ransomware, viruses, worms, and Trojans, leading to data loss, system malfunction, or unauthorized access.
Example: Ransomware encrypts files on a user’s device and demands a ransom for their release, compromising the integrity of the data.
Prevention Measures: Utilize endpoint protection solutions, network firewalls, and intrusion detection systems, back up critical data regularly, enforce the principle of least privilege to limit malware from spreading, and educate users about secure browsing habits and the risks of downloading or executing suspicious files.
4. Man-in-the-Middle (MITM) Attacks: MITM attacks occur when attackers position themselves between two parties: sender and receiver. This intercepts communication and allows attackers to eavesdrop on sensitive data or modify data in transit without the party’s knowledge.
Example: An attacker intercepts communication between a user and a banking website, capturing login credentials or injecting malicious code into web pages.
Prevention Measures: Encryption is a vital defense against MITM attacks. Secure communication protocols like SSL/TLS for web traffic or VPNs for remote access encrypt data, preventing attackers from deciphering or tampering with it.
5. Replay Attacks: In replay attacks, attackers intercept and capture network traffic containing authentication credentials or session tokens and replay them to gain unauthorized access to systems or services. This can occur when sensitive data is transmitted without proper encryption or authentication mechanisms, leading to unauthorized access, financial fraud, or data manipulation.
Example: An attacker intercepts network traffic containing a user’s login session token and replays it to gain access to the user’s account without needing valid credentials.
Prevention Measures: Encryption plays a crucial role in preventing replay attacks by securing the transmission of sensitive data. Implementing encryption protocols such as TLS/SSL encrypts transit data, making it difficult for attackers to intercept and replay authentication tokens or session identifiers.
6. Supply Chain Risks: Supply chain risks involve vulnerabilities or compromises within the interconnected network of suppliers and vendors. Attackers might exploit vulnerabilities within the supply chain to introduce malicious components or compromise the integrity of products or services.
Example: An attacker compromises a software vendor’s update mechanism, distributing malware-infected software updates to unsuspecting customers.
Prevention Measures: To mitigate these risks, organizations should perform thorough vendor assessments, establish secure communication channels, implement code signing and verification mechanisms, conduct regular security audits, and implement supply chain security controls.
You can also explore our blog: Protecting Confidentiality: Key Concerns & Prevention.
How Can InfosecTrain Help?
At InfosecTrain, we offer extensive training courses such as CompTIA Security+ and Certified Ethical Hacker (CEH) to address integrity concerns by emphasizing the protection of sensitive information. Through our diverse courses and workshops, we delve into the fundamentals of information security, risk assessment, cryptography, network security, and ethical hacking methods. Our training equips participants with the expertise to recognize vulnerabilities, manage risks effectively, and defend against unauthorized access, tampering, or data loss.

TRAINING CALENDAR of Upcoming Batches For Security+ SY0-701
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 03-May-2025 | 08-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 25-May-2025 | 05-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 28-Jun-2025 | 03-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |






 1800-843-7890 (India)
1800-843-7890 (India)