Shodan: Information Gathering Tool
If Google is the search engine for websites, then Shodan is the search engine for devices and the hidden corners of the Internet. Often referred to as “the search engine for hackers,” Shodan allows Cybersecurity Professionals, Ethical Hackers, Penetration Testers, and OSINT Researchers to find internet-connected devices, servers, databases, webcams, IoT devices, and even unsecured Industrial Control Systems (ICS).

Unlike traditional search engines that index web pages, Shodan scans the Internet for open ports, services, and vulnerabilities, making it an indispensable tool for information gathering and reconnaissance.
Why is Shodan a Game-Changer for Cybersecurity?
Shodan is not just a search engine—it’s a cybersecurity intelligence tool that provides deep insights into the exposed infrastructure on the Internet. From detecting misconfigured devices to finding exposed databases, this tool plays a critical role in both offensive and defensive security.
Cybersecurity professionals use Shodan for:
- OSINT (Open Source Intelligence) research
- Vulnerability assessments
- Identifying unpatched and misconfigured devices
- Threat intelligence and attack surface mapping
- Penetration testing and ethical hacking
How Shodan Works: The Basics of Its Search Functionality?
Shodan is like a relentless digital detective, continuously scanning the Internet and cataloging devices that most people never even think about. Unlike traditional search engines that focus on web pages, Shodan focuses on uncovering the digital fingerprints of internet-connected devices, giving cybersecurity professionals deep insights into the global attack surface. So, what exactly does Shodan scan and index?
- Open ports: Detects which doors (ports) are left open, including HTTP/HTTPS, SSH, RDP, FTP, and Telnet.
- Running services: Identifies what software or applications are actively operating on a server.
- Banner information: Extracts metadata, including software versions, configurations, and potential vulnerabilities.
- Geolocation data: Pinpoints the physical location of servers, giving analysts insights into the geographic spread of exposed assets.
Getting Started with Shodan: Step-by-Step
- Sign up for a free account at Shodan.io.



- Use the search bar to look for specific devices, vulnerabilities, or exposed services (e.g., port:21 country:US to locate FTP servers in the US).
- Refine your search with filters (e.g., org:”Google” to uncover devices owned by Google).
- Analyze results carefully: Each search result provides valuable details like IP addresses, device types, and potential security risks.
Shodan Use Cases in Cybersecurity
1. OSINT (Open Source Intelligence) Research
Shodan is a goldmine for OSINT investigations, helping cybersecurity professionals track exposed assets, gather threat intelligence, and monitor adversary infrastructure.
To find publicly accessible databases leaking sensitive information for MongoDB
| product:”MongoDB” port:27017 |

For Elasticsearch
| product:”Elasticsearch” port:9200 |
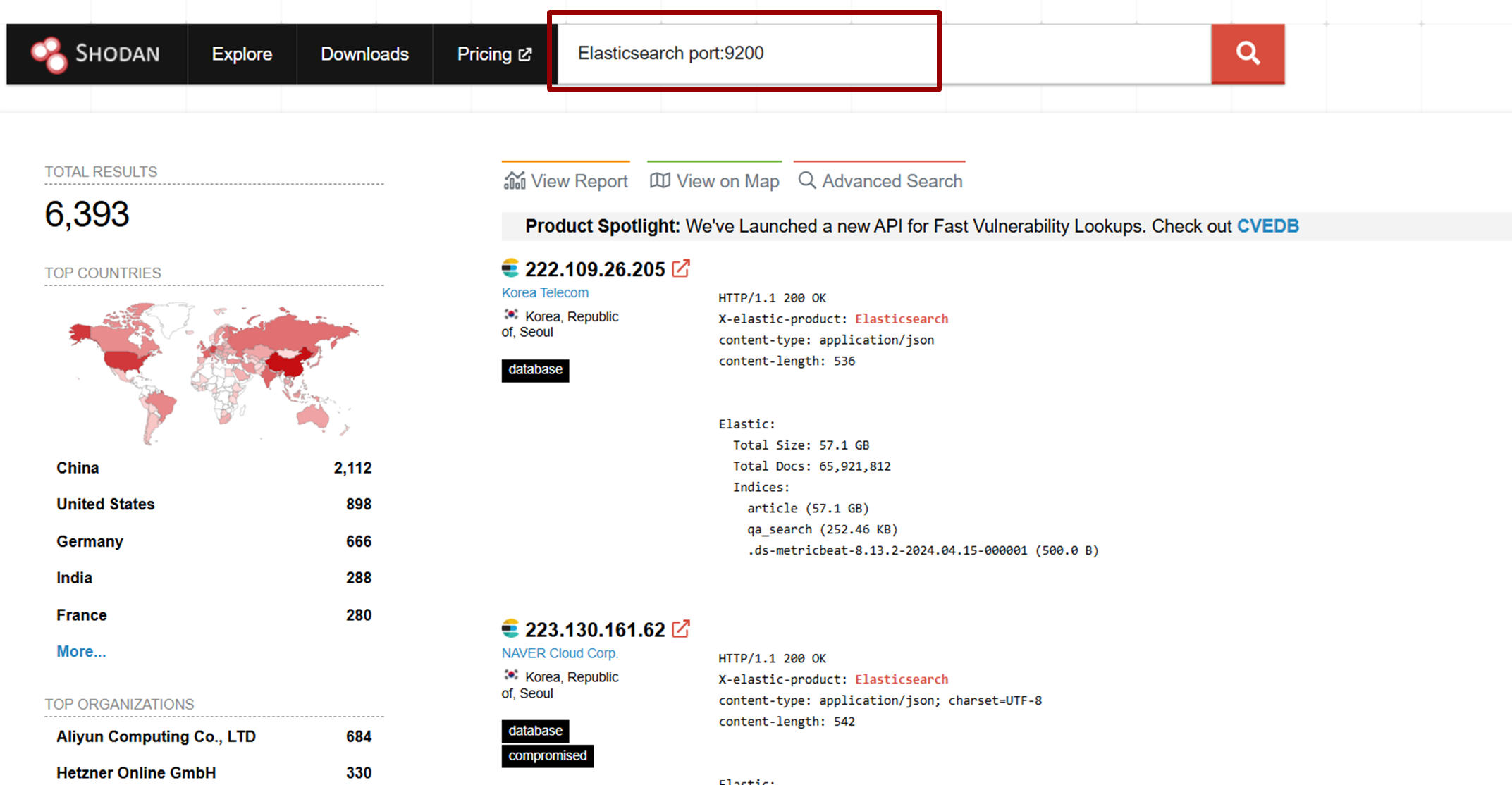
Identify servers associated with suspicious organizations:
(searches for assets owned by EvilCorp in xyz)
| org:”EvilCorp” country:xyz |

Track IoT devices with weak security: helps locate unsecured cameras.
| title:”webcam” |

2. Identifying Vulnerable Devices
Penetration Testers and Ethical Hackers leverage Shodan to locate outdated, misconfigured, and exposed devices.
- Find outdated web servers vulnerable to attacks:
product:”Apache httpd” version:2.4.49 (detects old Apache versions). - Identify open SSH servers that could be brute-forced:
port:22 country:US (finds SSH services in the US). - Locate routers using factory-default passwords (a common entry point for attackers):
“default password” in banner information.
3. Finding Misconfigured Databases and Cloud Storage
Unsecured databases and storage buckets can lead to massive data breaches.
- Detect exposed Redis instances:
port:6379 (searches for open Redis databases). - Find AWS S3 buckets mistakenly left open to the public:
bucket:open. - Identify unprotected SMB file shares:
port:445.
4. Threat Intelligence and Attack Surface Mapping
Shodan helps cybersecurity teams monitor an organization’s digital footprint and detect exposed assets before attackers do.
- Track enterprise assets:
org:”YourCompany” to reveal publicly exposed company-owned infrastructure. - Spot misconfigured firewalls:
port:23 to check for open Telnet services. - Set up Shodan alerts to monitor real-time changes in the attack surface.
5. Red Teaming and Penetration Testing
Red Teams use Shodan to identify weak points before conducting security assessments.
- Locate unsecured IoT devices:
“webcam” port:554 to find vulnerable surveillance cameras. - Identify Microsoft IIS servers for potential exploits:
product:”Microsoft-IIS”. - Find public RDP instances susceptible to brute-force attacks:
port:3389.
Advanced Shodan Techniques and Dorks
What Are Shodan Dorks?
Shodan dorks are specialized search queries that allow cybersecurity professionals to refine their searches and extract highly specific information from the vast pool of indexed internet-connected devices. These queries can help uncover exposed databases, outdated systems, and misconfigured services that may pose security risks. For example:
- port:3306 – This command filters results to show exposed MySQL databases. If these databases lack proper authentication, they can be easily accessed by attackers.
- country:IN org:”BSNL” – This query is geo-specific, allowing professionals to find devices in India owned by BSNL (Bharat Sanchar Nigam Limited), which can be useful for auditing a network’s security posture.
- before:2023 – This filter retrieves devices indexed before 2023, helping researchers find old, possibly unpatched systems still connected to the Internet.
- os:”Windows 7″ – This search helps locate machines running Windows 7, an outdated OS no longer receiving security updates, making them prime targets for exploits.
These dorks provide an efficient way to pinpoint vulnerabilities quickly, assisting Penetration Testers and Cybersecurity Analysts in reconnaissance, red teaming, and securing assets before attackers exploit them.
Learn Shodan with InfosecTrain
Shodan is more than a tool—it’s a cybersecurity intelligence powerhouse. Whether you’re a beginner, Penetration Tester, Ethical Hacker, or Cybersecurity Analyst, mastering Shodan can significantly enhance your OSINT and reconnaissance skills. But to truly harness its full potential, you need the right training and hands-on experience.
At InfosecTrain, we offer industry-leading courses such as Certified Ethical Hacker (CEH), Advanced Penetration Testing, and Red Team Training to help you build a solid foundation in ethical hacking, penetration testing, and adversary emulation. Our expert-led training provides real-world scenarios, practical exercises, and in-depth knowledge to ensure you can effectively use tools like Shodan to identify vulnerabilities and strengthen security defenses.
Ready to take your cybersecurity skills to the next level? Join our courses today and gain the hands-on expertise needed to master Shodan and other critical cybersecurity tools.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 04-Apr-2026 | 10-May-2026 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 02-May-2026 | 07-Jun-2026 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |

