SOC Analyst Interview Questions
Securing a position as a Security Operations Center (SOC) Analyst can be a pivotal step in your cybersecurity career. As the demand for skilled SOC Analysts soars, the interview process intensifies for individuals aspiring to join this specialized domain. Whether you are an experienced individual looking to advance into a SOC role or an aspiring security enthusiast aiming to excel in the field, succeeding in the interview is vital. Our article unveils top interview questions for SOC Analysts, aiming to aid you in your preparation journey.
SOC Analyst Interview Questions
General Questions
1. Explain SOC.
A Security Operations Center (SOC) is a centralized unit that continuously monitors and analyzes an organization’s security posture. It detects, investigates, and responds to cybersecurity incidents using technology solutions, processes, and a skilled security team to protect against data breaches and strengthen cybersecurity defenses.
2. What are some of the organizational challenges that a SOC Analyst faces while managing SOC?
As a SOC Analyst managing a Security Operations Center, several organizational challenges can arise:
- Sifting through massive amounts of non-critical data to find real threats
- Time-consuming false positive alerts
- Limited visibility into encrypted or complex assets
- Insufficient tools for effective monitoring and management
- Subpar analytics and filtering capabilities
- Inadequate automation in SOC processes
- Integration of difficulties among security tools and platforms
Network Security
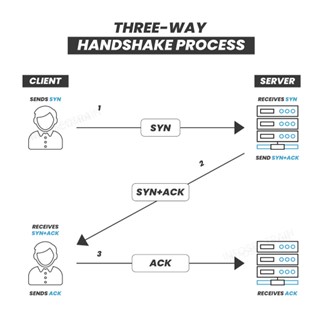
3. What is a TCP three-way handshake?
The TCP three-way handshake is a foundational networking process that establishes a reliable connection between a server and a client within a TCP/IP network. This procedure involves the mutual exchange of synchronization (SYN) and acknowledgment (ACK) signals to ensure both parties are ready for data transfer and to confirm that the communication ports are open and available.
4. Explain Virtual Private Network (VPN).
A VPN is a technology that encrypts data and establishes a secure tunnel for its transmission over the Internet. This safeguards sensitive information against cyber threats like eavesdropping and unauthorized access. It is crucial for protecting data confidentiality and integrity during transmission across public or less secure networks.
5. Could you explain the differences between Dictionary attacks and Brute Force attacks?
Here is the difference between dictionary and brute force attacks:
| Dictionary Attack | Brute Force Attack |
| Attacker utilizes a precompiled list of common words or phrases to guess passwords | Attacker tries all possible character combinations to identify a password |
| Less complex as it relies on a finite list of potential passwords that are more likely to be used by individuals | Time-consuming and resource-intensive due to a huge number of combinations |
| More effective when people use common words or predictable patterns in their passwords | More effective against passwords with high complexity and length |
| Prevented by enforcing complex password policies that avoid common words and phrases | Mitigated by using long, complex passwords and limiting login attempts |
6. Describe the difference between IDS and IPS.
IDS (Intrusion Detection System) is a security technology that scans for and identifies potential intrusions by monitoring network traffic and system activities. It aims to uncover any unauthorized or malicious activities that could compromise the network’s or system’s integrity.
IPS (Intrusion Prevention System) is also a security mechanism that not only monitors networks and systems for malicious activities but actively works to intercept and block those threats as they occur, providing real-time protection.
Security Testing
7. Describe the difference between Vulnerability Assessment and Penetration Testing.
Here is the difference between Vulnerability Assessment and Penetration Testing:
A vulnerability assessment is a methodical evaluation of security weaknesses within an information system. This process involves verifying the system’s exposure to any well-known vulnerabilities and determining the criticality of these issues.
Penetration testing is an active security practice in which a security professional, known as a penetration tester, actively tries to exploit vulnerabilities within a computer system to determine its defense capabilities.
8. What tools do you prefer for security testing, and why?
Here is the list of security testing tools:
| Wireshark | Packet analyzer, indispensable for network troubleshooting and traffic analysis. |
| Snort | Network intrusion detection system, great for real-time traffic analysis. |
| Splunk | Data analysis tool, exceptional for security monitoring and incident response. |
| Suricata | Similar to Snort, but with more multithreading capabilities for high-speed network traffic. |
| CrowdStrike Falcon | Offers excellent endpoint detection and response with real-time threat intelligence. |
| Elastic Stack (ELK Stack) | A robust SIEM platform for log aggregation and real-time monitoring. |
Log Analysis Questions
9. What is the Importance of log analysis in the SOC environment?
Importance of log analysis in a SOC environment:
- Detects Anomalies: Identifies unusual activities indicating potential security incidents.
- Improves Incident Response: Facilitates rapid response through detailed event context.
- Ensures Compliance: Helps meet regulatory requirements by maintaining logs.
- Enhances Forensics: Provides crucial data for post-incident investigations.
- Optimizes Threat Hunting: Enables proactive searches for hidden threats.
10. How would you monitor hundreds of systems?
Steps to monitor hundreds of systems include:
- Configure SIEM to collect and analyze logs from all systems
- Set up real-time alerts for suspicious activities
- Regularly review and tune SIEM rules for accuracy
- Integrate external intelligence for proactive threat detection
- Continuously monitor and investigate security alerts
Incident Response and Management
11. Describe the difference between an incident and an event.
An event is an observable occurrence within a system or network that can be detected, verified for accuracy, and documented for reference or analysis, ranging from normal to potentially suspicious activities. In contrast, an incident is a particular type of event or a chain of events that can have detrimental impacts on the security aspects of an asset, such as its confidentiality, integrity, or availability.
12. Explain the difference between incident management and problem management.
Incident Management focuses on mitigating the immediate effects and restoring service operations as quickly as possible. On the other hand, Problem Management is concerned with identifying the underlying causes of incidents to prevent their recurrence in the future.
13. Explain the differences between true positive, false positive, true negative, and false negative.
| Term | Explanation |
| True Positive | A security threat is identified, and it is a legitimate threat. It indicates the effectiveness of the security measures in detecting real attacks. |
| False Positive | A security threat is identified, but it is not an actual threat. This can lead to wasting resources and potential distraction from real threats. |
| True Negative | No security threat is identified, and there is no actual threat present. It indicates the system’s effectiveness in not raising unnecessary alarms. |
| False Negative | No security threat is identified, but an actual threat is present. This is a critical failure, as an actual attack is not detected, potentially leading to undetected breaches. |
14. How do you prioritize and manage alerts in a high-volume environment?
Prioritize and manage alerts in a high-volume environment by:
- Implement Alert Triage: Prioritize alerts by severity, potential impact, and urgency, ensuring high-risk threats are addressed first.
- Use Automation and Orchestration: Automate response mechanisms for low-level alerts and streamline workflows.
- Enhance Threat Intelligence: Integrate real-time intelligence to identify threats faster.
- Layered Alert Thresholds: Establish multi-tiered alert thresholds to differentiate between immediate action required and informational alerts.
- Continuous Training: Continuously train staff on emerging threats and responses.
Tools and Technologies
15. What is SIEM?
An SIEM (Security Information Event Management) system is a centralized platform for gathering, processing, and organizing data from various sources within a network. It combines the capabilities of Security Event Management (SEM), which offers real-time monitoring, analysis, and reporting of security events, with Security Information Management (SIM), which archives data for the long term and provides analytical tools for pattern detection and compliance reporting.
16. What is XDR?
XDR (Extended Detection and Response) is a suite of tools designed to bolster security teams in detecting, investigating, and responding to cyber threats. It integrates data from every layer of an organization’s IT infrastructure, enhanced with threat intelligence, to uncover and address complex and stealthy security threats. The primary goal of XDR is to provide an automated, all-in-one solution for Threat Detection, Investigation, and Response (TDIR) activities to tackle a wide array of threats.
17. What are the main differences between SIEM and XDR?
| Feature | SIEM | XDR |
| Scope | Centralizes log data | Extends beyond traditional data sources |
| Integration | Primarily logs and events | Integrates network, endpoint, cloud, and more |
| Automation | Limited automation capabilities | Advanced automation for threat response |
| Intelligence | Depends on predefined rules | Uses analytics and machine learning |
| Deployment | Complex setup and tuning | Typically, more user-friendly and integrated |
Frameworks and Methodologies
18. Explain the MITRE ATT&CK framework.
The MITRE ATT&CK framework is a vast matrix of Tactics, Techniques, and Procedures (TTPs) used by threat actors in cyberattacks. It provides detailed insights into attacker methods and behaviors, facilitating threat modeling, and helping in developing effective detection, defense, analysis, and response strategies for cybersecurity professionals.
Digital Forensics
19. What is digital forensics?
Digital forensics involves collecting, preserving, analyzing, and presenting digital evidence from electronic devices to support investigations of cybercrime, policy violations, and other incidents requiring technical scrutiny.
20. In digital forensics, what does the term “chain of custody” mean?
Chain of custody in digital forensics refers to the documentation process that records the handling, storage, transfer, and analysis of digital evidence, ensuring its integrity and admissibility in legal proceedings from collection to presentation in court.
For more insights on these topics and to explore scenario-based questions, consider checking out our SOC Analyst series, where experienced experts share their knowledge.
If you want to understand more about this domain, you can explore our related articles:
- Top 25 SOC Analyst interview questions that You Should Know
- How Do I Get My First Job In SOC?
- Role And Responsibilities of a SOC Analyst
- SOC Analyst Vs. Penetration Tester
- Infosec Train’s SOC Analyst Training Program
- SOC Analyst Interview Questions & Answers
- SOC Analyst Job Profile, Skills, Certifications, and Salary
- The Top Five Takeaways From Our SOC Analyst Course: Why are we different?
Become a SOC Analyst with InfosecTrain
Take the first step towards mastering the cybersecurity intricacies by enrolling in InfosecTrain‘s SOC Analyst training course. This course is designed to provide you with a deep dive into the world of Security Operations Centers, equipping you with the expertise needed to excel in this demanding field. Through practical, hands-on sessions, you will learn to navigate real-world scenarios under the guidance of some of the most knowledgeable trainers in the industry.
Individuals can also enroll in our SOC Expert Combo training course to further enhance their expertise in complex security challenges, advanced threat detection techniques, and effective incident response strategies.
TRAINING CALENDAR of Upcoming Batches For SOC Analyst
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 06-Sep-2025 | 19-Oct-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 08-Nov-2025 | 21-Dec-2025 | 19:00 - 23:00 IST | Weekend | Onsite | [ Open ] |

 1800-843-7890 (India)
1800-843-7890 (India)