The Role of Biometrics in Data Security and Privacy
Data security and privacy are paramount in an era dominated by digital interactions and data-driven business processes. Biometrics is crucial in protecting sensitive data from cyber threats because of its exceptional capacity to provide a robust authentication mechanism while upholding user privacy. As technology advances, adopting and implementing biometric solutions properly can instill confidence and trust in individuals and organizations navigating the digital landscape, ensuring the security of their data.

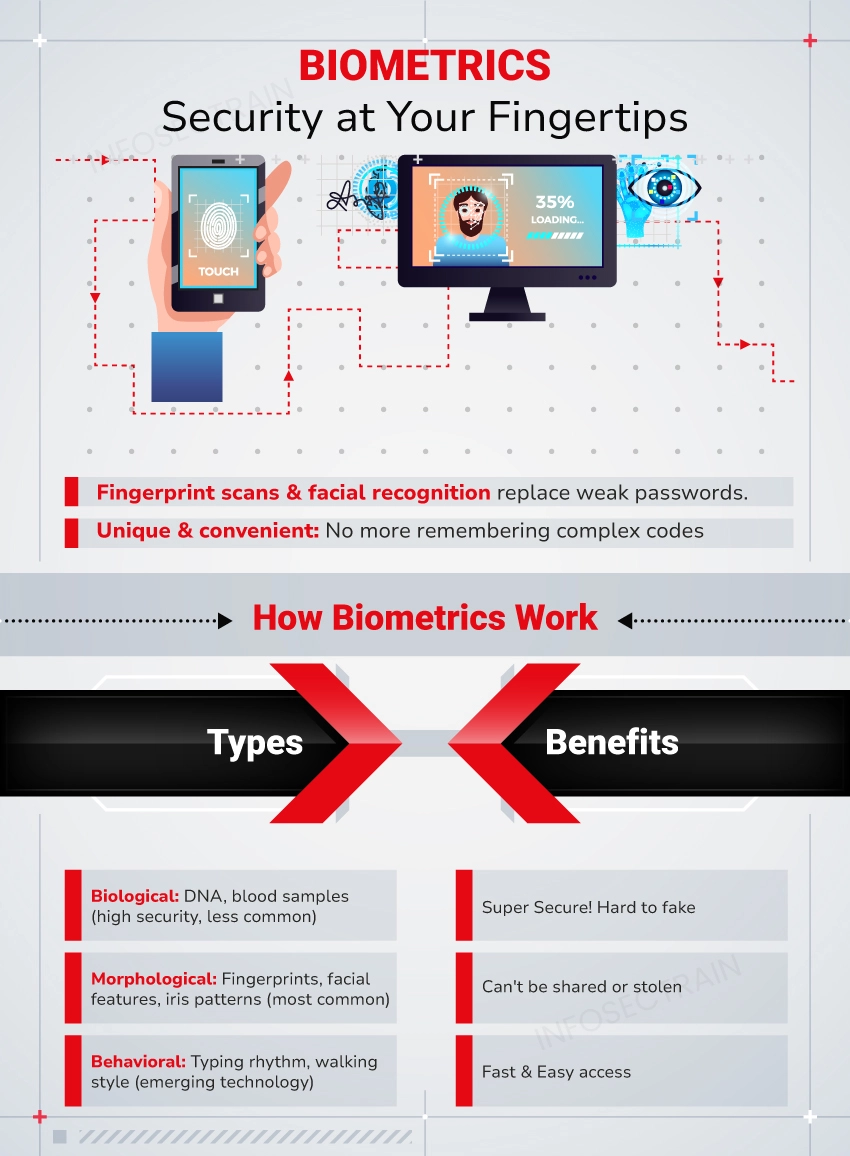
What is Biometrics?
Biometrics is the practice of analyzing unique physical or behavioral traits to identify and authenticate individuals. Biometric properties, such as fingerprints, facial features, iris patterns, voice, and even behavioral characteristics like keystroke dynamics, offer a highly secure and individualized authentication compared to passwords or PINs, which can be lost, shared, or stolen. A strong barrier against identity theft and cyberattacks, biometric data is stored in encrypted form and is difficult to duplicate.
Types of Biometrics Security
- Biological Biometrics: Biological biometrics focuses on traits at the genetic and molecular levels. These characteristics are unique to each individual and may include elements such as DNA or blood samples used for identification purposes.
- Morphological Biometrics: Morphological biometrics center around the physical structure of the body. These traits involve tangible features like fingerprints, eye patterns, or facial shapes, which security scanners can capture and analyze.
- Behavioral Biometrics: Behavioral biometrics rely on distinctive patterns exhibited by individuals. These patterns are specific to each person and can include traits like walking style, speech patterns, or even typing behavior on a keyboard. Tracking and analyzing these behavioral patterns aid in identifying and verifying an individual’s identity.
Advantages of Biometrics
- Enhanced Security: Biometric characteristics are exclusive to each individual, making it difficult to copy or fake them. They are unique compared to more traditional authentication techniques like passwords or PINs, which are more vulnerable to hacking, thus resulting in higher security.
- Non-Transferable: Unlike passwords or access cards, biometric traits cannot be shared, transferred, or stolen, ensuring that only the authorized person can access the protected resources.
- Remote Authentication: Technology improvements have made it possible to perform biometric authentication remotely, providing secure remote access to systems and services.
- Convenience and Speed: Biometric authentication is quick and user-friendly. Users must exhibit their biometric attributes, which are quickly captured and verified, rather than carrying physical tokens or remembering complicated passwords.
How Does Biometrics Help in Data Security and Privacy?
- Unique Identification:Biometrics relies on characteristics specific to each individual, like facial features, fingerprints or iris patterns, to provide unique identification. Because of its uniqueness, there is less chance of identity theft and unauthorized access because only authorized individuals can access important information.
- Strong Authentication: A robust and trustworthy technique for confirming an individual’s identification is provided through biometric authentication. Biometrics considerably lowers the likelihood of password-related weaknesses, such as password reuse or brute-force attacks, compared to conventional password-based authentication.
- Non-Repudiation: Biometric information is directly linked to the individual, making it difficult for users to dispute their activities or transactions. This non-repudiation feature is significant in transactions involving money and law, where accountability is essential.
- Reduced Reliance on PII: Unlike conventional PII authentication techniques, biometrics rely entirely on non-reproducible physical or behavioral features. As biometric templates are useless without the actual person, this lowers the possibility of PII data breaches.
Challenges of Biometrics
- Biometric Spoofing and Presentation Assaults: One of the biggest challenges is the possibility of biometric spoofing or presentation assaults. Attackers may trick the system and gain unauthorized access by presenting false fingerprints or facial photos as artificial biometric samples.
- Accuracy and False Positives/Negatives: Biometric systems occasionally generate false positives, which result in the improper acceptance of illegal individuals, or false negatives, which result in the incorrect rejection of permitted individuals. In order to prevent an overabundance of false rejections or acceptances, there should be a perfect balance between security and user convenience.
- Ethical and Legal Concerns:The gathering and use of biometric data involve consent, data ownership, and potential surveillance. Legal systems must handle these issues to safeguard individual liberties.
- The Permanence of Biometric Traits:Unlike passwords that can be changed, biometric traits are generally permanent. If a biometric trait is compromised or needs to be replaced due to an injury, it can lead to challenges in updating the system and user re-enrollment.
About InfosecTrain
InfosecTrain offers various information security certification training courses. Explore our range of cybersecurity, Data Security, and Data Privacy training courses led by qualified professionals. Enhance your skills, build a strong foundation for a career in security, and earn your certification. Register now and evolve into a proficient security specialist.







 1800-843-7890 (India)
1800-843-7890 (India)