CCSP Domain 2: Cloud Data Security
CCSP
The CCSP is a globally recognized certification that represents the pinnacle of cloud security knowledge. It was co-created by (ISC)2 and the Cloud Security Alliance (CSA), two of the most respected information security and cloud computing security organizations. This certification meets the increasing demand for trained and certified Cloud Security Professionals. A CCSP demonstrates competence in Cloud Security architecture, design, operations, and service orchestration by applying information security expertise to a Cloud computing environment. This professional competence is assessed against a body of knowledge that is globally recognized.

Domains of CCSP
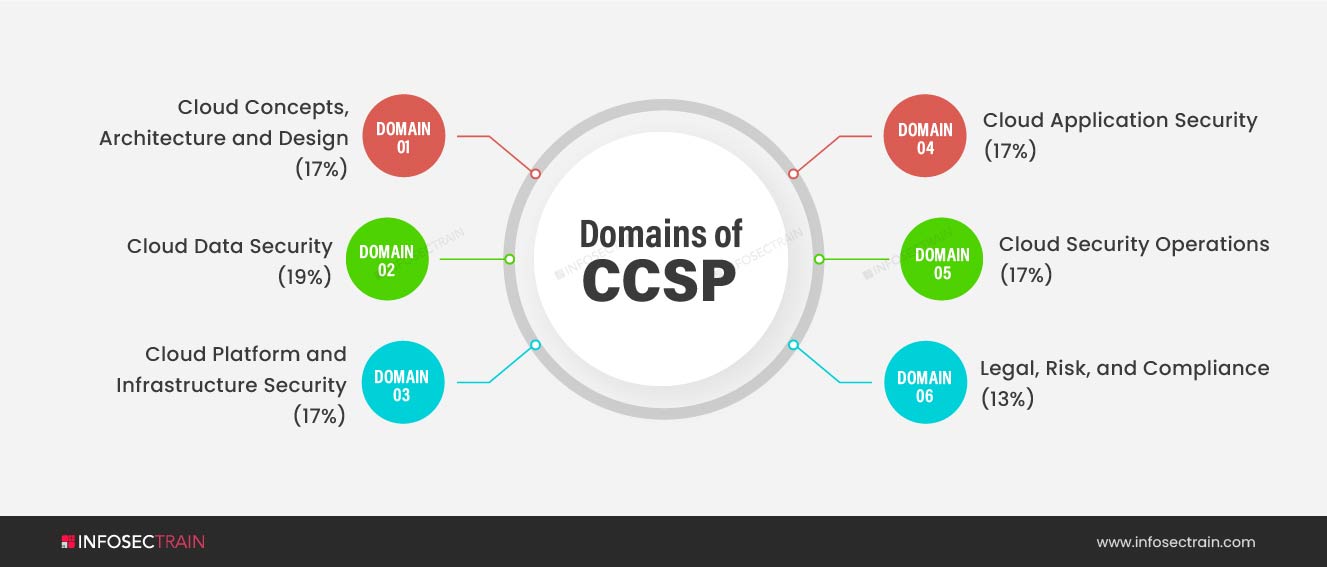
CCSP comprises a total of six domains:
- Domain 1: Cloud Concepts, Architecture and Design (17%)
- Domain 2: Cloud Data Security (19%)
- Domain 3: Cloud Platform & Infrastructure Security (17%)
- Domain 4: Cloud Application Security (17%)
- Domain 5: Cloud Security Operations (17%)
- Domain 6: Legal, Risk, and Compliance (13%)
In this blog, we will cover the second domain: Cloud Data Security.
Cloud Data Security
The second domain of CCSP, Cloud Data Security, is the most crucial domain as it covers the central part of the CCSP exam. It holds a weightage of 19%. It mainly focuses on:
- Describing Cloud Data Concepts
- Designing and Implementing Cloud Data Storage Architecture
- Designing and Applying Data Security Technologies and Strategies
- Implementing Data Discovery
- Implementing Data Classification
- Designing and Implementing Information Rights Management (IRM)
Understanding the Cloud Data Lifecycle
In this, we understand the different phases of data during its lifecycle. They are mainly referred to as CSUSAD, which stands for Create, Store, Use, Share, Archive, and Destroy. Data can be found in three states:
- Data in Transit (DIT)
- Data in Use (DIU)
- Data at Rest (DAR)
In order to ensure security in these phases, we must be aware of the organization mapping of the different stages of a Data Life Cycle. The Cloud Security Alliance (CSA) is one of the two developers of the CCSP that offers guidance regarding the Cloud Data Lifecycle. The candidates who want to pursue CCSP certification must be familiar with the Cloud Data Lifecycle phases and the data protection tools used to execute them. Along with Data Lifecycle, Data Dispersion also falls under this category, which is used for redundancy and robustness.
Designing and Implementing Cloud Data Storage Architectures
In this section, we learn about the different types of Cloud Storage Services available that vary across the service model. This portion of the CCSP is devoted to all facets of cloud storage. To be prepared, you must understand the various types of storage (long-term, ephemeral, and raw-disk), and the kinds of storage we use in SaaS, PaaS, and IaaS, respectively. We learn about the advantages and drawbacks of these storage services. Also, we understand the possible threats to each type of storage (unauthorized access, unauthorized usage, liability due to regulatory non-compliance, etc.) and how to address and mitigate these threats using encryption and other technologies.
Designing and Applying Data Security Strategies
This is the most crucial part from the exam point of view. In this section, we understand the various data-protection resources available and how to use them. We learn about:
- Encryption and Key management: Symmetric and Asymmetric Encryption, ECC, RSA, AES
- Hashing
- Masking: Static and Dynamic Masking
- Tokenization
- Data Loss Prevention (DLP)
- Data Obfuscation
- Data De-identification and modern and evolving cryptography-related technologies.
Understanding and Implementing Data Classification Techniques
In this section, we understand the different methods to find data within a cloud environment and how to classify data properly. It is about analyzing the data value based on the criticality and sensitivity of data. We learn about:
- Mapping: It involves mapping the sensitive data and the security controls deployed to guard.
- Labeling: It provides visibility to the data.
- Sensitive Data: It includes PHI, PII, Card Holder data, etc.
Understanding and Implementing Data Discovery
This section opens up a landscape of the possibility of enterprise collaborations that is enabled by sharing data and analytics. In this section, we understand the different types of data discovery approaches. We learn about:
- Structured Data
- Unstructured Data
Designing and Implementing Relevant Jurisdictional Data Protections for Personally Identifiable Information (PII)
Personal Identifiable Information (PII) is a category of data that is commonly-regulated. In this section, we understand the major data privacy laws, conduct data discovery, identify the data discovered, and chart, define, and apply security controls to protected data.
Designing and Implementing Information Rights Management (IRM)
In this section, we understand the technology for managing user access to various data. This includes being familiar with the controlling of data movement in the Cloud. You need to understand the difference between Enterprise DRM and Consumer DRM. We learn about:
- Objectives: Data Rights, Provisioning, Access Models, etc.
- Appropriate Tools: Issuing and Revocation of Certificates
Designing and Implementing Data Retention, Deletion, and Archiving Policies
Data is moved to long-term storage after completion of its lifecycle. Data preservation, deletion, and archiving policies are stringent in most corporate and legally protected data. Due to the lack of physical control over the hardware where the data is stored, cloud environments can make these policies more difficult to implement. In this section, we understand data retention, deletion, and archiving practices, processes, and mechanisms. We learn about:
- Data Retention Policies
- Data Deletion Procedures and Mechanisms
- Data Archiving Procedures and Mechanisms
- Legal Hold
Designing and Implementing Auditability, Traceability, and Accountability of Data Events
In this section, we cover all aspects of event management, including identifying event sources, recording events, storing events, and constantly improving the process. The section also concerns chain of custody and ensuring that collected data is non-repudiable. We learn about:
- Definition of Event Sources and Requirement of Identity Attribution
- Logging, Storage, and Analysis of Data Events
- Chain of Custody and Non-repudiation
CCSP with InfosecTrain
You can opt for the Certified Cloud Security Professional (CCSP) for professional knowledge and an in-depth understanding of Cloud security. We are one of the leading training providers with our well-read and experienced trainers. The courses will help you understand the basic concepts and provide a sound knowledge of the subject. This certification will indeed merit each penny and minute you will invest.