CompTIA Cloud+ Domain 2: Security
Domains of CompTIA Cloud+
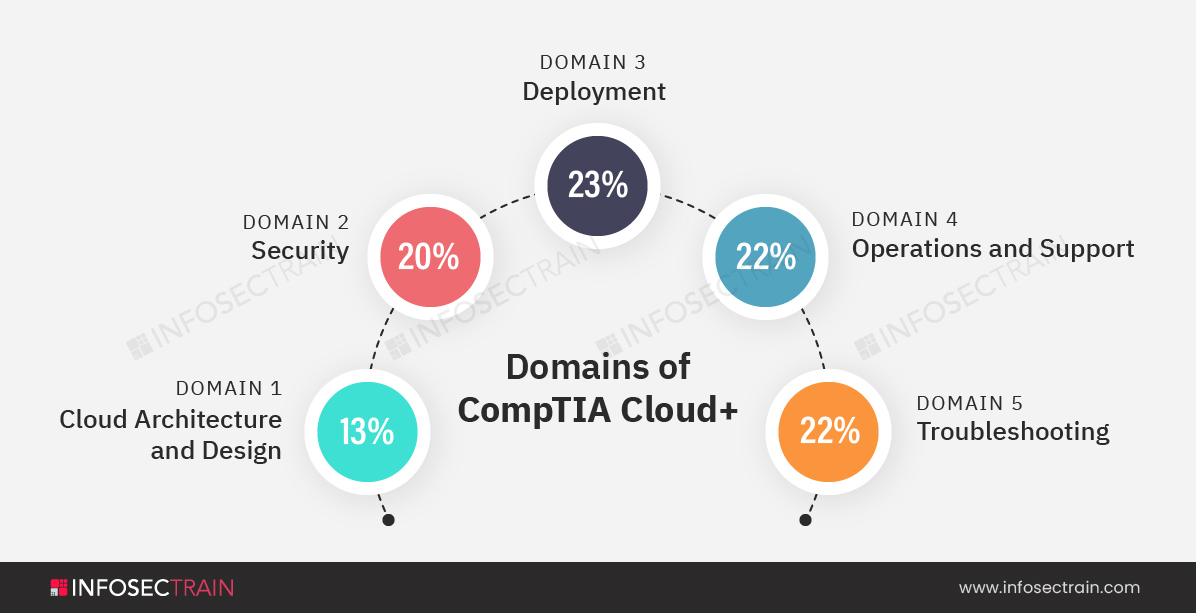
CompTIA Cloud+ certification comprises a total of five domains:
- Domain 1: Cloud Architecture and Design 13%
- Domain 2: Security 20%
- Domain 3: Deployment 23%
- Domain 4: Operations and Support 22%
- Domain 5: Troubleshooting 22%
We will discuss the second domain that is ‘Security.’
Security
Since security is a shared responsibility between the client and the cloud service provider, it is like joint custody where both parties play an equal role. Security breaches can be catastrophic for an organization, so they must pay extra attention to their security infrastructure. The second domain of CompTIA Cloud+ certification explains all the aspects of security. It comprises a fair amount of weightage that is 20% in the CompTIA Cloud+ exam.

1. Configure Identity and Access Management: In this sub-domain, we learn about configuring Identity and Access Management in a given scenario. It provides an in-depth knowledge of identification and authorization, directory services, federation, certificate management, Multi-Factor Authentication (MFA), Single Sign-On (SSO), Public Key Infrastructure (PKI), secret management, and key management. The identification and authorization explain all about privileged access management, logical access management, account life-cycle management, provision and de-provision accounts, role-based access controls, discretionary access controls, non-discretionary access controls, and mandatory access controls. Directory service explains Lightweight Directory Access Protocol (LDAP). The Single Sign-On (SSO) will define Security Assertion Markup Language (SAML).
2. Secure a network in a cloud environment: In this sub-domain, we learn about securing a network in the cloud environment in a given scenario. It incorporates network segmentation, protocols, network services, log, event monitoring, network flows, and hardening and configuration changes. The network segmentation will provide an in-depth understanding of Virtual LAN (VLAN)/Virtual Extensible LAN (VXLAN)/ Generic network virtualization encapsulation (GENEVE), micro-segmentation, and tiering. Protocols will explain all about Domain name service (DNS), DNS over HTTPS (DoH)/DNS over TLS (DoT), DNS Security (DNSSEC), Network Time Protocol (NTP), Network Time Security (NTS), encryption, IPSec, Transport Layer Security (TLS), Hypertext Transfer Protocol Secure (HTTPS), tunneling, Secure Shell (SSH), Layer 2 Tunneling Protocol (L2TP)/Point-to-Point Tunneling Protocol (PPTP), Generic Routing Encapsulation (GRE). Network Services will explain all about stateful firewalls, stateless firewalls, Web Application Firewall (WAF), Application Delivery Controller (ADC), Intrusion Protection System (IPS)/Intrusion Detection System (IDS), Data Loss Prevention (DLP), Network Access Control (NAC), and packet broker. Hardening and configuration changes explain about disabling unnecessary ports and services, disabling weak protocols and ciphers, firmware upgrades, control ingress, and egress traffic, allow list (previously known as whitelisting) or blocklist (previously known as blacklisting), proxy servers, and Distributed Denial of Service (DDoS) protection.
3. Apply the appropriate OS and application security controls: We learn about applying the appropriate OS and application security controls in a given scenario in this sub-domain. It explains about policies, user permissions, antivirus/anti-malware/Endpoint Detection and Response (EDR), Host-based IDS (HIDS)/Host-based IPS (HIPS), hardened baselines, file integrity, log and event monitoring, configuration management, builds, Operating System (OS) upgrades, encryption, mandatory access control, and software firewall. In policies, we learn about password complexity, account lockout, application-approved list (previously known as whitelisting), software feature, and user/group. Single functions fall under hardened baselines. We learn about stable builds, Long-Term Support (LTS) builds, beta builds, and canary builds in the build section. Encryption explains all about Application Programming Interface (API) endpoint, application, Operating System (OS), storage, and filesystem.
4. Apply data security and compliance controls in cloud environments: In this sub-domain, we learn about applying data security and compliance controls ina cloud environment in a given scenario. It includes topics like encryption, integrity, classification, segmentation, access control, the impact of laws and regulations, records management, Data Loss Prevention (DLP), and Cloud Access Security Broker (CASB). In integrity, we learn about hashing algorithms, digital signatures, and File Integrity Monitoring (FIM). The impact of laws and regulations explains all about legal hold. Records management explains versioning, retention, destruction, and writing once read many.
5. Implement measures to meet security requirements: In this sub-domain, we learn about implementing measures to meet security requirements in a given scenario. It provides an in-depth knowledge of tools, vulnerability assessment, security patches, risk register, prioritization of patch application, deactivates default accounts, impacts of security tools on systems and services, effects of cloud service models on security implementation. Tools explain vulnerability scanners and port scanners. Vulnerability assessment explains default and common credential scans, credentialed scans, network-based scans, agent-based scans, and service availability. Security patches present all about hotfixes, scheduled updates, virtual patches, signature updates, and rollups.
6. Explain the importance of incident response procedures: In this domain, we learn about preparation and incident response procedures. Preparation explains documentation, call trees, training, tabletops, documented incident types/categories, and roles and responsibilities. Incident response procedures describe identification, scope, investigation, containment, eradication, recovery, isolation, evidence acquisition, chain of custody, post-incident and lessons learned, and root cause analysis.
CompTIA Cloud+ with InfosecTrain
For expert knowledge and an in-depth grasp of Cloud security, consider taking the CompTIA Cloud+ Certification Training Course from InfosecTrain. Instructors that are highly trained and experienced are in charge of this training. With our well-versed and experienced teachers, we are among the leading training providers in the globe. The courses will assist you in grasping the fundamental principles and providing a thorough understanding of the subject. This certification is well worth every dollar and minute you put into it.







 1800-843-7890 (India)
1800-843-7890 (India)