The Strategic Processes Behind Executing an Effective PEN Test
With the increase in the number of data breaches and ransomware attacks making headlines, thorough security audits have become an unavoidable element of running a firm that manages client data.

This article will outline a systematic methodology that a security professional must follow to conduct a successful penetration test or PEN test.
What is a PEN test? – Complete Penetration Testing Guide
A PEN test or penetration test identifies attack vectors, vulnerabilities, and control flaws in IT infrastructure, networks, and business applications. PEN testing entails simulated attacks against an organization’s information security systems using several manual and automated procedures. In simple words, a PEN test is a process of identifying vulnerabilities and delving into them to determine the extent to which a target can be compromised in the event of a real Cyberattack.
The penetration testing process entails actively examining the target system for any potential vulnerabilities that may arise as a result of bad or improper system configuration, known and unknown hardware or software faults, and operational flaws in procedural or technical countermeasures. Penetration testing aims to exploit known vulnerabilities, but it should also employ the tester’s knowledge to find specific weaknesses that are unknown vulnerabilities in an organization’s security measures.
Why the PEN test?
A penetration test will ensure that architectural flaws are detected and fixed before a hacker can locate and exploit them, resulting in a business loss or service outage. These days, businesses must adhere to a variety of rules and procedures. A penetration test will guarantee that any gaps are identified and closed in time to meet regulatory requirements.
Penetration tests will also serve as an eye-opener or a check on the internal security team of the firm. It is possible to measure the impact of an actual attack, the damages that can be done, and the potential cost to the organization if an attack occurs.
With so many large-scale and dangerous cyber-attacks taking place these days, it’s become inevitable to conduct penetration testing regularly to protect information systems from security breaches.
What are the approaches or methodologies of the PEN test?
Below are the various methodologies of the PEN test.
- White box PEN test: The Pen Tester is given complete information about the IT infrastructure, source code, and environment in this technique for pen-testing. It is a more extensive and in-depth pen test in which every aspect of the application is examined, including the quality of the code and the basic design. Furthermore, pen-testing of this nature typically takes two to three weeks to complete. Internal pen-testing, clear box pen-testing, and even glass box pen-testing also recount a white box pen test.
- Grey box PEN test: The Pen Tester is given partial information about the IT infrastructure and code structure in this technique of pen-testing. It is a more targeted method because the Pen Tester only has a limited understanding of or access to the internal network or online application, allowing them to concentrate their efforts on exploiting the potential vulnerabilities, saving time and money. It can be regarded as an External Hacker gaining unauthorized access to an organization’s network infrastructure documentation.
- Black box PEN test: The Pen Tester in this approach does not know the organization’s IT architecture. This procedure appears to be more similar to a simulation of a real-world cyber-attack to identify system flaws. In this strategy, the Pen Testers play the role of cyber-attackers, attempting to exploit the system’s weaknesses. This procedure takes a long time to perform and can take up to six weeks. An external pen test is another name for the black-box pen test.
- External PEN test: External pen-testing is when the penetration test is carried out from outside the network.
- Internal PEN test: Internal pen-testing is used to simulate a scenario where the attacker is present within the network. The attacker, in this case, will have a lot of knowledge about the system and the target because he is an internal person.
- Blind PEN test: This approach mimics an actual cyber attack. Similar to an unethical attacker apart from the fact that the organization has authorized it. The Ethical Hacker is provided limited knowledge and must figure out the majority of the firm’s information independently.
- Double-blind PEN test: This type of testing is identical to blind testing, except that someone within the organization is aware of the action. The purpose of the test is to see how fast and effective the security team is at monitoring and responding to threats and preparing the company for an actual attack, and closing gaps.
- In-house and third-party PEN test: The test is referred to as an in-house pen test when an in-house security team carries it out. It’s a different type of internal penetration test. Whereas, when firms hire third-party entities to execute these tests, it is known as third-party pen-testing.

Steps in the PEN testing process
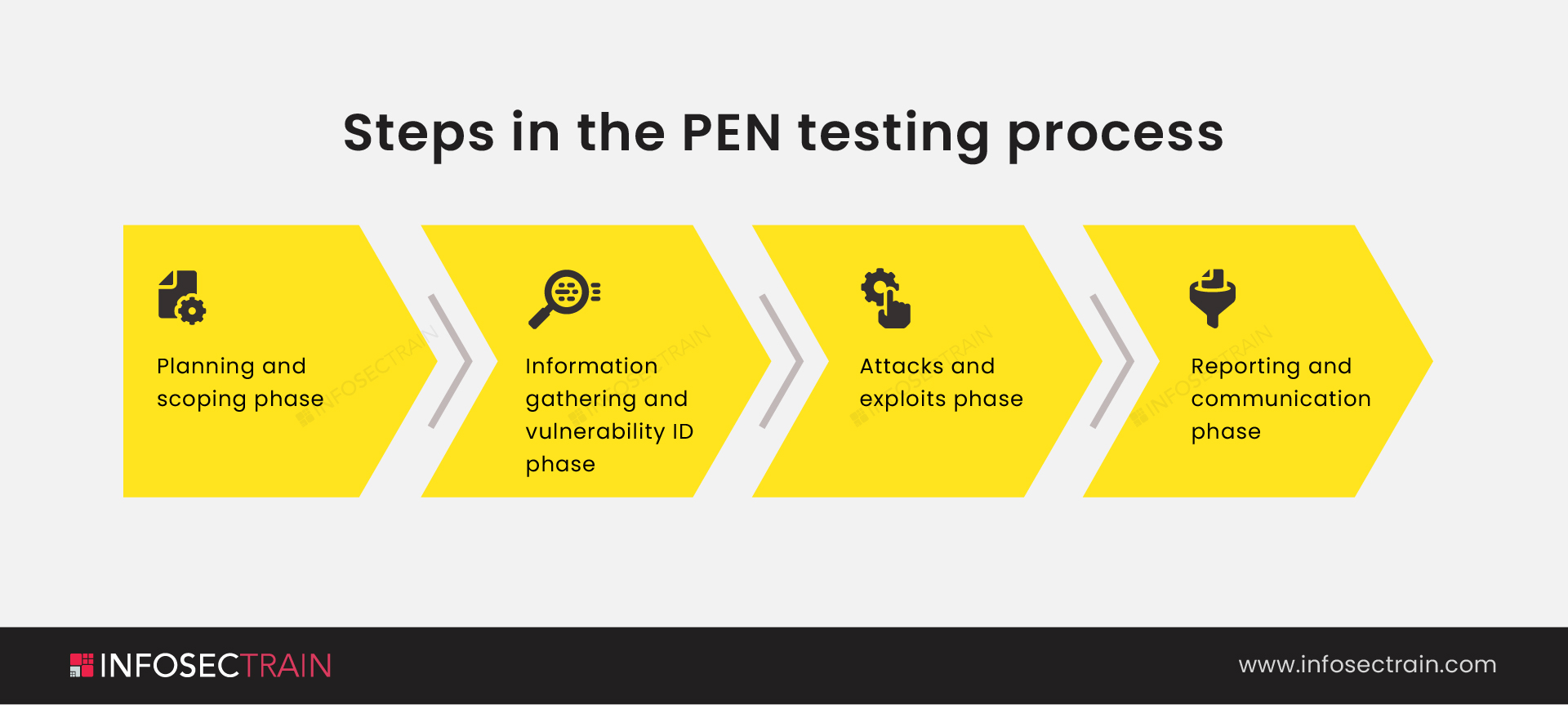
PEN tests can be divided into several stages, depending on the organization and the type of test being undertaken that is either internal or external.
Let us go over four primary phases of PEN test, each one by one:
- Planning and scoping phase: The scope of the task is specified at the planning phase. Management approvals, documentation, and agreements such as the Non-Disclosure Agreement (NDA), among others, are all signed. The pen-testing team develops a clear plan for the job. Existing security rules, industry standards, best practices, and other factors will all be considered when determining the scope of the test. This phase usually entails all of the actions that must be completed before the actual penetration test.
- Information gathering and vulnerability ID phase: The real pen test begins only after the information gathering phase, also known as the discovery phase. The pen testers and stakeholders make sure they are on the same page about what each test should achieve. Security professionals monitor the target, acquiring the data needed to scope and execute each test properly. The information gathering can be active, allowing the tester to make direct contact with the target, or passive, not allowing the tester to make direct contact with the target. The tester collects information while remaining undetected by the target.
- Attacks and exploits phase: The most intriguing and challenging step of any pen test is this one. A penetration tester will try to uncover exploits for the numerous vulnerabilities discovered in the previous phase during this phase. Countless online sources give proof-of-concept exploits for the majority of vulnerabilities. If not done correctly, this step can be harmful. Running an exploit has the potential to bring a production system down.
- Reporting and communication phase: The reporting and communication phase is the final stage of the entire operation. This stage might occur concurrently with the previous three or after the attack stage. Many penetration testers do not pay attention to this stage and rush through all of the submissions. The organization reimburses you for this final report; it is perhaps the most crucial of all the phases. The final report must consider both management and technical aspects, detailing all results with appropriate graphs, figures, and other visual aids to create a clear picture of the vulnerabilities and their impact on the target organization’s operations.
Who performs the PEN test?
PEN test is carried out by PEN Testers who build and organize simulations and security assessments to find potential vulnerabilities in the system, IT infrastructure, or web applications. In addition, PEN Testers must document any findings and provide them to customers, employees, or the organization.
What are various PEN test tools?
Now, as we have covered the principles of penetration testing, it’s time to move on. Let us take a look at the tools a Pen Tester can utilize to do this test.

PEN test with InfosecTrain
Every organization must identify security issues in the internal network and IT systems. Using this knowledge, the organization may plan a defense against any hacking attempt. We at InfosecTrain recognize the necessity for professionals to be trained in order to help combat these attacks and threats, as user privacy and data security are two of the most pressing problems today. PEN tests can aid in the detection of these dangers. So you can enroll in our CompTIA PenTest+, Network Penetration Testing, Web Application Penetration Testing, Advanced Penetration Testing, and Active Directory Pentest training courses. Our qualified instructor will present you with how to spot exploitable vulnerabilities in networks, systems, hosts, and other IT devices long before attackers do.







 1800-843-7890 (India)
1800-843-7890 (India)