Top 10 Cyber security attacks

In today’s digital world, cyber-attacks are an absolute certainty. While the basic types of attacks are still prevalent, new types of attacks have also metamorphosized, creating more monetary and physical destruction. Here are the Top 10 Cyber Security Attacks that are highly prevalent today.
- Brute force attacks
The use of “passwords” is still the most popular way to authenticate a user. When an attacker tries all possible alphabet and number combinations to crack a password, that is a “brute force attack”. The attack is normally carried out by bots or computers. There are different tools that are used to perform brute force attacks like John the Ripper, Aircrack-ng, L0phtCrack, and RainbowCrack.
Brute force attacks are more successful if the length of the password is less. For example, a 8 character password can be cracked in a few seconds or a few hours using the tools mentioned. On the other hand, if the password is long and has more characters, it will take more time to crack it.
According to https://howsecureismypassword.net/, a 8 character password can be cracked within a few minutes to hours.
Did you know that – 5% of attacks in 2017 were due to brute force attacks?
Ways to prevent brute force attacks:
Since brute force attacks rely on weak and vulnerable passwords, it is good to follow the following tips to prevent them:
- It is mandatory to set a definite set of password tries (maybe 3)
- It is also good to have a combination of characters, numbers, and symbols in a password
- The password should length of 10 characters to reduce the possibility of being subjected to brute force attacks
- Denial of Service attack (DoS attack)
DoS or Denial of Service attack is probably the most commonly encountered type of attack in the digital world. In this, as the name indicates, the host is attacked and denied from serving genuine client requests. How is this done? DoS attacks can be made in many ways. One way is to bombard the server with unlimited requests such that the server finds it difficult to respond if many such attackers attack a system in a similar way the server will be brought to a standstill in a very short time.
The other way is to send malformed packets to the server. The server does not know how to react and crashes, sending genuine requests to be rejected. The other types of denial of service attacks are distributed denial of service attacks (DDoS), Smurf attacks, teardrop attacks, fraggle attacks, and SYN flood attacks.
Ways to prevent DoS attacks:
Even though it is tough to predict DoS attacks, these measures if taken, can reduce the intensity of DoS attacks:
- Constantly scanning the network is probably the best way to sense DoS attacks
- In effect of this, Intrusion detection systems (IDS) and Intrusion Prevention Systems (IPS) tools should be installed in the network to note any anomalous traffic.
- Host hardening should be employed on all Internet-facing servers and devices
- Ingress and Egress filters should be employed to watch out for malicious traffic
- It is also necessary to work with the Internet service provider when the DoS attack is taking place to minimize its impact
- DDoS (Distributed Denial of service attacks)
A DDoS is similar to a DoS but is more large scale and more sinister in its workings. In a DDoS, instead of one attacker or a few attackers trying to overwhelm a system, there are multiple computers taking part to overwhelm the system and bring it down. A master computer gives directions to other slave computers, and they, in turn, will cripple systems or ruin major corporations.
There are different types of DDoS attacks, such as traffic attacks, bandwidth attacks, and application attacks.
Ways to prevent DDoS attacks:
While large scale, global DDoS attacks is difficult to predict there are again a few steps that can be taken to minimize its impact:
- As with DoS attacks, monitoring the network for anomalous traffic is the first step in recognizing DDoS attacks
- Keeping an eye on social media chatter also helps us to understand any impending DDoS attacks
- In addition, conducting a mock DDoS attack against the existing infrastructure will help the organization be better prepared for such attacks.
- SMURF attacks:
A ‘Smurf’ attack is a Distributed Denial of service attack that started to appear in the late 1990s. In a Smurf attack, the attacker makes use of the ICMP or the Internet Control Message Protocol to carry out their attack. These are the steps in a Smurf attack:
- The attacker sends a spoofed ICMP request to a device such as a router.
- The spoofed IP address is the victim’s server address
- No sooner than an ICMP request been made to the router, it broadcasts it to all the devices connected to it.
- These devices, in turn, send a response to the victim flooding it.
Ways to prevent Smurf attacks:
Since Smurf attacks are DDoS attacks, preventing them is similar to preventing DDoS attacks.
- It is essential to monitor network traffic and do packet analysis to sense Smurf attacks
- Anti-virus and anti-malware can be installed to prevent Smurf attacks
- IP broadcast addressing can also be disabled in the router
- Social engineering attack
‘Social engineering’ may be the most passive, yet the most effective cybersecurity attack. It does not need excessive knowledge of cybersecurity tools or any other specialized knowledge of Information security.
A social engineering attack only needs a smooth and cunning individual to convince an innocent user to part with their bank account details, password details, and any other financial and personal information.
Ways to prevent a social engineering attack:
- Just like ‘Zero trust architecture’ in Information security, citizens should cultivate ‘zero trusts’ when talking to anyone regarding their financial details
- All citizens should be made aware of good cybersecurity practices which are listed below
- Do not share OTP and other financial details to anyone claiming to be from the bank or other financial institutions
- Do not click on any new and foreign links in SMS, email or other means of communication
- Do not open emails from an unknown sender
- Using 2-factor authentication when signing onto sensitive sites is a good practice to prevent social engineering attacks
- Dumpster diving
‘Dumpster diving’ is a different type of attack wherein the attacker gathers information about the victim by looking at the information that has been discarded in the dumpster or trash can. They then use this information and attack the user.
Information that can give an attacker clues may be passwords written down and discarded, access codes and even a calendar and organizational charts that may reveal more about an organization. This is the information gathering phase, which in turn can be used to attack the organization.
Ways to prevent dumpster diving:
- Do not write down passwords, access codes and other important information anywhere and discard them
- Shred all the paperwork appropriately
- Paper disposal policy should be established for the organization
- All storage media should be completely erased using appropriate tools before being discarded
- All employees should be made aware of the different policies and the ways to implement them
- Cross-site scripting(XSS) attack
A cross-site scripting attack or XSS attack is a client-side injection attack. The attacker makes use of a vulnerability in a website and inserts a malicious code inside a client-side Javascript. Once the malicious Javascript starts executing on the client-side, the attacker takes control of the interactions with the user. The attacker can further control the functionality of the application and its data.
Ways to prevent XSS attack:
- It is good to filter the input to minimize XSS attacks
- The content security policy should be enabled
- Buffer Overflow attacks
The memory locations where data is stored are “buffers.” When we enter data for more than the data locations allocated, it spills over onto subsequent locations of memory. This is “buffer overflow” or “buffer overrun.” As an example, we can have
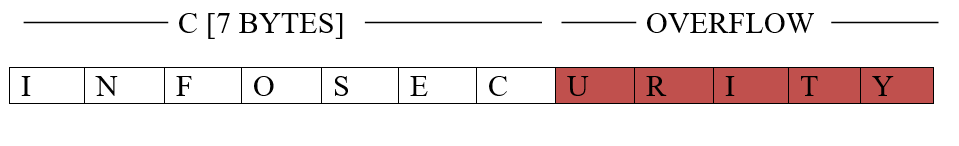
In this case, ‘C’ has been allocated only 7 bytes. But, since the word ‘INFOSECURITY‘ is more than 7 bytes, the buffer overruns into subsequent memory locations.
When this happens, the program starts corrupting other areas of memory and starts behaving strangely. It may also expose the personal information of the site and give hackers the key to exploit systems. Old programming languages such as ‘C’ and ‘C++’ are more prone to buffer overflow attacks.
Hackers study the code and make use of this vulnerability and cause the system to behave erratically or crash.
Ways to prevent buffer overflow attacks:
- Write well-designed code
- Validate user data to check to ensure that the data entered stays within the stated limits
- Apply all patches for older systems and use compilers that protect against buffer overflows
- Use of programming languages that do not use direct memory access is preferred
- Pharming
The act of hacking a website and redirecting users to a fake website is known as “Pharming”. In this case, users will not know that they have been redirected to a fake website. Banking sites and e-commerce organizations are popular targets of this type of attack.
Ways to stay away from “Pharmed” sites:
Alertness is the key to stay away from pharmed sites.
- At the very beginning, the user should check the URL of the address. Pharmed sites will have a different URL than the original URL(as an example, sbi.co.in might have changed to www.sbicoin.com)
- Users should always check for ‘secure’ sites when working with banks and other financial organizations. This can be done by checking the ‘padlock’ in the left-most corner of the URL
- All secure sites should begin with ‘https’ instead of ‘http’
- The certificate of the site should be verified
- Keystroke logging
‘Keystroke loggers’ or ‘Keyloggers’ are another way of passively attacking a system. This is done by recording the keystrokes of a user and sending it to the attacker, who then uses the information to perform other large scale attacks. This surreptitiously stolen information can also be sold to other party criminals for malicious purposes.
‘Keystroke loggers’ are not totally illegal since they can be used by employers to keep tabs on employees, parents to keep tabs on children, and so on. But when it is done mischievously, without the knowledge of an unknown user, it causes monetary and personal damage to the user.
There are two categories of keystroke loggers – hardware and software. While the hardware keystroke logger has to be physically installed on the system, the software loggers can just be downloaded by clicking on a malicious link through text messages, email, or any social media site. The unfortunate part of keyloggers is that they do not make any difference in the functioning of a system and cannot be detected easily.
Ways to prevent and detect Keyloggers:
- It is good to install anti-spyware, anti-virus, anti-malware programs that may detect keyloggers
- It is also necessary to scan the system regularly to detect keyloggers
- In addition, all patches and system updates must be regularly applied
- Employees and other users must be advised not to download unknown attachments as these may download the malicious keyloggers.
We have seen some of the most popular cybersecurity attacks. There will be more attacks as the days unfold, but it is our knowledge and determination that will keep them away!
For more of InfoSec Train’s courses, do visit us at this link.






 1800-843-7890 (India)
1800-843-7890 (India)