Top AWS Interview Questions and Answers to Ace in 2023
Amazon Web Services (AWS) has become an important factor in the rapidly changing world of cloud computing, completely altering how businesses build, operate, and grow their IT infrastructure. The demand for knowledgeable AWS individuals has risen to previously unheard-of levels as businesses increasingly use cloud technology to encourage innovation and efficiency. As a result, interviews for AWS-related jobs have grown more demanding and concentrated, calling for a thorough comprehension of AWS services, architecture, and best practices.

This article includes a chosen collection of the top AWS interview questions and answers for the year 2023. These questions have been carefully collected to represent AWS’s most recent developments and advancements, catering to the industry’s changing demands. Whether you are a seasoned AWS specialist or a candidate looking to get into the realm of cloud computing, this compilation will provide you with vital insights and expertise to confidently handle AWS-focused interviews.
1. What is the connection between Availability Zone and Region?
In Amazon Web Services (AWS), Regions represent distinct geographical areas, such as “US-West 1 (North California)” and “Asia South (Mumbai).” Each Region is independent and isolated from other Regions, providing redundancy and low-latency access for users in different locations. Each Availability Zone may contain a single or multiple data center.
Within each AWS Region, there are Availability Zones (AZs). Availability Zones are isolated areas within a Region designed to ensure fault tolerance and high availability. They operate in separate data centers and can replicate themselves as needed. By distributing resources across multiple Availability Zones within the same Region, AWS users can achieve enhanced resilience and continuity in case of disruptions.
2. What stages are involved in implementing a CloudFormation Solution?
In a CloudFormation solution, the implementation involves the following steps:
- Create or use a template in JSON or YAML format template.
- Store the template in an S3 bucket for easy access.
- Use CloudFormation to create a stack based on the template.
- CloudFormation provisions resources in the specified order, managing dependencies.
- Monitor stack creation and manage resources using the template.
- Maintain infrastructure as code for consistency and version control.
3. What services are available for implementing a centralized logging solution?
Essential services include:
- Amazon CloudWatch Logs: Collects and stores log data from various AWS resources and applications.
- Amazon S3: Acts as a storage repository for the log data collected by CloudWatch Logs.
- Amazon Elasticsearch: Utilized to visualize and analyze log data efficiently.
- Amazon Kinesis Firehose: Facilitates seamless data movement from Amazon S3 to Amazon Elasticsearch for analysis and visualization.
- Amazon CloudTrail: Captures and records API activity within the AWS environment, providing an audit trail of user actions, applications, and services. This essential service enhances visibility into account activity and assists in compliance, security analysis, and troubleshooting efforts.
4. What is AWS S3?
Amazon Simple Storage Service (Amazon S3) is a highly scalable and durable cloud storage service that Amazon Web Services (AWS) provides. It is designed to store and retrieve vast amounts of data, ranging from small individual files to massive datasets, over the internet. S3 offers a simple and cost-effective solution for businesses and developers to store and manage their data in a secure and reliable manner.
5. What is AMI?
AMI stands for Amazon Machine Image. It is a pre-configured virtual machine image used to create and launch instances (virtual servers) in Amazon Elastic Compute Cloud (Amazon EC2). An AMI contains the operating system, application software, configurations, and necessary data to run an instance.
6. What are the native logging capabilities of AWS Security?
AWS CloudTrail:
- Provides AWS API call history for the account.
- Enables security analysis, resource change tracking, and compliance auditing.
- Configurable to send notifications via AWS SNS for new log deliveries.
- CloudTrail logs can be forwarded to AWS S3 and CloudWatch for retention purposes, as CloudTrail retains logs for only 90 days.
AWS Config:
- Helps understand configuration changes in the environment.
- Offers AWS inventory with configuration history and change notification.
- Configurable to send information via AWS SNS for new log deliveries.
AWS CloudWatch:
- Provides a comprehensive monitoring and management service for AWS resources, including logs.
- CloudWatch Logs allows users to collect, monitor, and store log data from various AWS resources and applications.
- Its metrics provide insights into the performance of AWS resources, allowing you to set alarms and take automated actions based on defined thresholds.
7. What are AWS’s standout services?
- EC2: On-demand computing resource for hosting applications, ideal for uncertain workloads.
- Route 53: Web-based DNS service for managing domain names and routing internet traffic.
- S3: Widely used storage service for securely storing and retrieving data.
- EBS: Persistent storage for EC2 instances, enabling data persistence.
- CloudWatch: Monitoring service for critical AWS resources and setting up alarms.
- SES: Service for sending emails using regular SMTP or API calls.
8. What is the difference between stopping and terminating an instance?
An EC2 instance has three states: starting, stopping, and terminating.
| Starting and Stopping | Terminating |
|
|
9. What is the root device volume on Amazon EC2?
On the root device, volume, supported by either Amazon EBS or an instance store, is stored in the root device image used to boot an EC2 instance. The root device volume is created when an Amazon AMI launches a new EC2 instance. The EC2 instance’s lifetime does not impact the root device data stored on Amazon EBS.
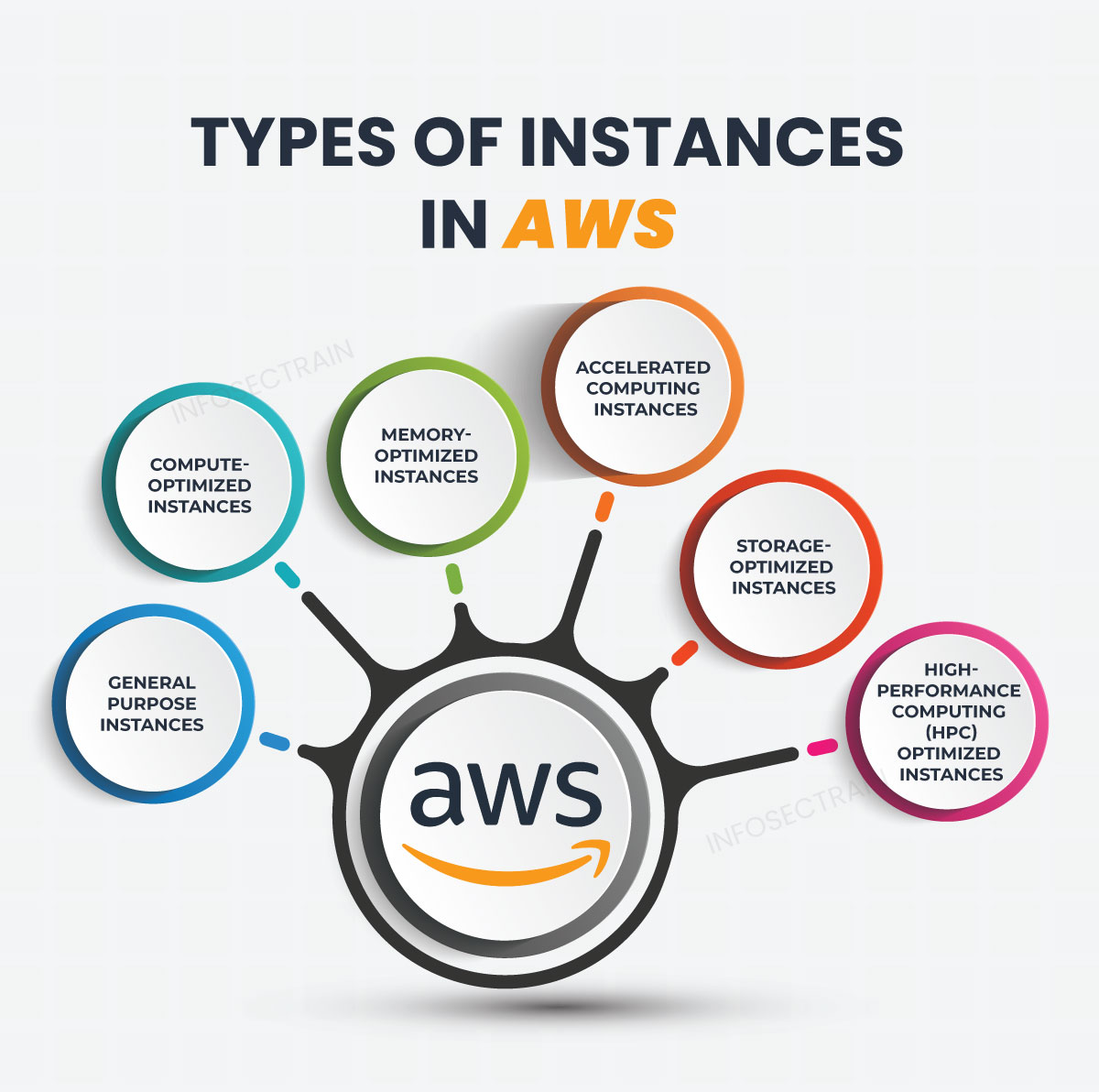
10. What are the different types of instances in AWS?
The following are the types of AWS instances.
11. How do you set up CloudWatch so that an EC2 server can be recovered?
To set up CloudWatch to enable automated recovery for an EC2 server, you can use Amazon CloudWatch Alarms and Amazon EC2 Auto Recovery. Here’s a step-by-step guide:
- Create a CloudWatch alarm to monitor instance health.
- Define recovery actions in the alarm settings.
- Enable EC2 Auto Recovery, for instance.
- Associate the CloudWatch alarm with Auto Recovery.
- Verify automated instance recovery during testing.
12. How do you configure an AWS system to track website metrics in real-time?
To configure an AWS system to track website metrics in real-time, follow these steps:
- Set up Amazon CloudFront: Use CloudFront to distribute content and gain access to real-time logs.
- Enable CloudFront Access Logs: Enable logging in CloudFront settings to capture real-time access logs.
- Send Logs to Amazon Kinesis Data Firehose: Configure CloudFront to send access logs to Kinesis Data Firehose.
- Process Logs with Kinesis Data Analytics: Use Kinesis Data Analytics to analyze and process real-time log data.
- Store Metrics in Amazon CloudWatch: Send processed metrics from Kinesis Data Analytics to CloudWatch for real-time monitoring.
- Visualize Metrics: Use CloudWatch dashboards or integrate with other monitoring and visualization tools to display website metrics in real time.
13. List some AWS services that are not region-specific.
Some AWS services are not region-specific and are available globally. These services are designed to be accessible from any AWS Region and include:
- AWS IAM (Identity and Access Management): Manages access and permissions to AWS resources.
- AWS Route 53: Provides domain name registration and DNS routing services.
- AWS CloudFront: Content Delivery Network (CDN) service for distributing content globally.
- AWS WAF (Web Application Firewall): Protects web applications from common web exploits and attacks.
- AWS S3 (Simple Storage Service): Object storage service for storing and retrieving data globally.
- AWS CloudWatch: Monitoring service for collecting and tracking metrics, logs, and events.
- AWS Lambda: Serverless computing service for running code without managing servers.
- AWS API Gateway: Service for creating, publishing, and managing APIs.
14. What is the difference between a Reserved Instance, a Spot Instance, and an On-Demand Instance?
| Reserved Instance | Spot Instance | On-Demand Instance |
|
|
|
15. What are Snapshots in Amazon Lightsail?
Snapshots are point-in-time backups of EC2 instances, block storage drives, and databases in AWS. They can be created manually or automatically at any time. Snapshots allow resources to be restored to a previous state even after their creation. Restored resources perform the same tasks as the original ones from which the Snapshots were taken. They serve as essential data recovery and disaster resilience tools in AWS.
16. What is a bastion host?
A bastion host is a security-hardened instance that is used to access other instances in a VPC. Bastion hosts can be used to reduce the attack surface of the VPC (Virtual Private Cloud).
17. What do you mean by Key-Pairs in AWS?
In AWS, a key pair is a cryptographic key used for secure authentication and access to Amazon EC2 instances. It consists of a public key, uploaded to AWS instances, and a private key held by the user. The public key encrypts data, while the private key decrypts it. Key pairs enable secure logins via SSH for Linux instances and decrypt Windows passwords for Windows instances. Keeping the private key safe is crucial to prevent unauthorized access.
18. What is the difference between RTO and RPO in AWS?
| RTO | RPO |
|
|
Additional AWS Interview Questions to Enhance Your Preparation:
- Top 25 AWS Interview Questions-Part 1
- Top 25 AWS Interview Questions- Part 2
- Top interview questions for AWS Solutions Architect
- Top AWS Architect Interview Questions In 2022
How can InfosecTrain Help You?
Boost your AWS interview readiness with our comprehensive interview questions and answers collection. At InfosecTrain, we stand ready to support you in your journey toward becoming an AWS expert. We offer diverse certifications training courses, including AWS Certified Solutions Architect-Associate, AWS Certified Solutions Architect-Professional, and AWS Certified SysOps Administrator Associate.
Under the guidance of our seasoned instructors, you can confidently pursue AWS certifications and open up new career avenues in cloud technology. Demonstrate your cloud computing and AWS knowledge to clients, showcasing your expertise in the field. Unlock the door to AWS excellence by joining InfosecTrain. Empower yourself with skills that transcend boundaries as you confidently and competently embrace the opportunities and challenges of cloud technology.







 1800-843-7890 (India)
1800-843-7890 (India)