Top Cybersecurity Interview Questions
Cybersecurity is the only area of IT that has not experienced a recession yet. Demand brings competition. It is essential for handling data breaches, effectively safeguarding sensitive data, and reducing risk. While possessing the required Cybersecurity abilities is the first step, passing the interview is an entirely different story. Cybersecurity interview questions and answers to assist you in acing interview successfully.

1: What exactly is Cybersecurity?
Cybersecurity is concerned with preventing hackers from accessing electronic data on websites, networks, or devices. Cybersecurity experts assist in maintaining data security and accessibility through cutting-edge technology and complex procedures.
2: Which skills are necessary for a Cybersecurity professional?
Understanding network and endpoint threat mitigation are two essential skills for Cybersecurity professionals. A Cybersecurity professional must understand computer networks and cloud server security.
3: Define hacker?
An individual who violates a computer system is known as a hacker. Hacking can be done for various objectives, such as installing malware, stealing or destroying data, disrupting services, etc.
4: What is Cryptography?
“Cryptography” comes from the Greek word kryptos, which means hidden. The study of secure communication methods, such as encryption, which restrict access to message contents to the sender and intended receiver, is known as cryptography.
5: What’s the most common type of Cyberattack?
A phishing attack is the most common Cyberattack because it is simple to execute and surprisingly powerful.
6: What is a three-way handshake?
A three-way handshake (also known as TCP-3way handshake) is a mechanism to establish a connection between the client and server over a transmission control protocol/ internet protocol (TCP/IP) network. In this mechanism, the client and server send each other the synchronization and acknowledgment packets before an actual data transmission occurs.
7: Define a firewall.
A firewall is a program that filters both incoming and outgoing traffic networks according to a set of user-defined rules. A firewall’s general goal is to lessen or completely stop undesirable network communications while enabling all lawful communication to proceed without interruption.
8: How do you configure a firewall?
- Username/password: Change a firewall device’s default password
- Remote management: Disable the remote administration feature.
- Configure correct port forwarding for some applications, such as a web server or FTP server, to function effectively.
- Server for DHCP: In the absence of disabling the firewall’s DHCP, installing a firewall on a network with a DHCP server will cause a conflict.
- Logging: Ensure logging is enabled and learn how to view logs to fix firewall problems or potential assaults.
- Policies: Ensure the firewall is set up to enforce sound security regulations. You should also have strong security policies.
9: What function do antivirus sensor systems serve?
Antivirus software detects, stops and removes viruses from a computer. After installation, most antivirus programs run in the background to provide real-time protection against Cyberattacks.
10: What is security auditing?
Security auditing is considered one of the most effective ways to keep a system’s integrity. Establishing the proper level of auditing for your environment should be a component of the overall security plan.
11: How do encryption and hashing differ?
The purpose of hashing and encryption are distinct. While hashing is a one-way procedure that converts data into the message digest, which is irreversible, encryption comprises both the encryption and decryption process.
12: Define a VPN?
A virtual private network, or VPN, is a service that aids in maintaining your online privacy. A VPN connects your computer to the Internet in a secure, encrypted manner, by creating a secure, encrypted tunnel for your data and conversations while you use public networks.
13: What are the possible response codes from a web application?
1xx – Informational responses
2xx – Success
3xx – Redirection
4xx – Client-side error
5xx – Server-side error
14: What is data leakage?
Data leakage is the unauthorized transfer of information from an organization to an outside source via Hard Discs, USB storage devices, mobile phones, and other devices. This data may be physically or electronically leaked; it refers to the exposure or transmission of an organization’s sensitive data to the external recipient.
15: What is SSL, and why is it important?
SSL is a data encryption protocol that enables secure communication between a web server and a web browser. Businesses and organizations must add SSL certificates to their websites to secure online transactions and protect client information.
16: Explain Two-factor Authentication with an example?
The second layer of security is added to your online accounts by two-factor authentication (2FA). For account access, you need more than just your username and password; you also need access to something yours to obtain the additional log in credential.
Example-Using two different factors like a password and a one-time password (OTP) sent to a mobile phone via SMS is two-factor authentication.
17: What is a Cross-Site Scripting XSS attack?
Cross-site scripting (XSS) attack is something in which an attacker inserts harmful executable scripts into the source code of a reliable website or application. Attackers frequently start an XSS attack by giving users a malicious link and convincing them to click it.
18: How can identity theft be prevented?
- Use cryptic language.
- You might also give free online tools an attempt to generate passwords almost impossible to crack.
- Make sure all your passwords contain a combination of capital and lowercase letters, numbers, and other symbols like hyphens or punctuation marks.
- Never use the same password twice.
19: How to Identify a DDoS Attack?
A website or program abruptly slowing down or failing to function is the most noticeable sign of a DDoS attack. However, other variables, such as increases in genuine traffic, problems with the hardware infrastructure, and a host of others, can also lead to the same issues.
20: Describe a botnet?
A computer network that has malware infections and is managed by a bot herder is referred to as a botnet. The individual who works the botnet infrastructure is known as the “bot herder.” A bot is any solitary device part of a botnet network.
21: What is ethical hacking?
Ethical hacking is a lawful effort to gain unauthorized access to a computer system, application, or data. To carry out ethical hacks, copies of malicious attackers’ tactics and actions are used.
22: What is the difference between Symmetric and Asymmetric encryption?
Symmetric Key Encryption: Encryption changes a message’s format so no one can read it. The message is encrypted using a key in symmetric-key encryption, and the same key is also used to decrypt the message, making it simple to use but less secure. A secure way must be used to pass the key from one party to another.
Asymmetric Key Encryption: Public and private essential encryption techniques are the foundation of asymmetric key encryption. The communication is encrypted and decrypted using two distinct keys. Although slower, it is more secure than symmetric key encryption.
23: What is a CIA triad?
The CIA (confidentiality, integrity, and availability) triangle is a methodology for handling information security rules inside an organization.
Confidentiality: A set of regulations restricting access to information is known as confidentiality.
Integrity: This guarantees the accuracy and dependability of the information.
Accessibility: It gives authorized users reliable access to data.
24: How does Traceroute work?
A Traceroute operates by transmitting Internet Control Message Protocol (ICMP) packets, which are received by every router involved in the data flow. The ICMP packets reveal if the routers utilized for the transmission can successfully transfer the data.
25: What is Port Scanning?
A port scan attack can be used by cybercriminals to identify open ports and determine whether they accept or reject data. It can also reveal whether a company employs firewalls or other active security measures.
The response that hackers get from a port when they send a message to it tells them whether the port is in use and whether it has any vulnerabilities that might be exploited.
Using the port scanning technique, businesses can also send packets to particular ports and examine the responses for potential vulnerabilities. To maintain the security of their network and systems, they can utilize tools like IP scanning, network mapper (Nmap), and Netcat.
Port scanning can provide information such as:
- Services that are running
- Users who own services
- Whether anonymous logins are allowed
- Which network services require authentication
26: Differentiate between Hashing & Salting?
Hashing- Hashing is a one-way technique; data is confined to a fixed-length value and is mainly used for authentication.
Salting- Hashing requires an additional step called salting, which gives passwords that modify the generated hash value more excellent value.
27: SSL vs. HTTPS: which one is more secure?
Hypertext Transfer Protocol Secure is what HTTPS stands for, and it is the fundamental Internet protocol used by websites on browsers. The secure variant of the HTTP protocol is HTTPS, and all data transferred using the protocol is entirely safe because it is encrypted.
Secure socket layers are referred to as SSL. The encryption of the Internet security protocol is done by SSL, which is essentially a component of the HTTPS protocol. Data integrity, confidentiality, and availability to only authorized users are its responsibilities.
28: What is a Brute Force Attack?
It is a hacking method that makes use of trial and error to break encryption keys, passwords, and login credentials. It is a straightforward but effective strategy for unauthorized access to user accounts, company systems, and networks. Until they discover the correct login information, the hacker tries a variety of usernames and passwords, frequently utilizing a computer to test a wide range of combinations.
“Brute Force” refers to attacks that utilize excessive force to obtain user accounts. Despite being a tried-and-true type of hacking, brute force attacks continue to be a favorite among hackers.
29: What do you mean by risk, vulnerability, and threat in a network?
Risk- An organization’s risk profile changes as a result of internal and external environmental factors. It takes into account the possibility or potential of a harmful occurrence and the possible effects that event might have on your infrastructure.
Vulnerabilities- Your surroundings and your assets have weak points, or vulnerabilities, making you more vulnerable to threats and higher risk. And unfortunately, a company may have thousands, sometimes even millions, of openness, and it is impossible to fix them all.
Threats- The Cybersecurity landscape is disrupted by an endless stream of potential threats, ranging from Ransomware that locks up your systems and malware that inserts deadly executables into your software. All of these dangers search for a way in and a weakness in your environment that they may take advantage of.
30: What do “white hat,” “black hat,” and “grey hat” hackers mean?
White hat hackers assist authorities, businesses, security agencies, and individual users. They are typically employed by a company that requires them to monitor potential exposure locations.
Black hat hackers are dishonest people who employ hacking techniques to get consumer data, business trade secrets, government secrets, and any other information they may use for harm.
Grey hat hackers are unaware that security and hacking are rarely black-and-white issues. Grey hat hackers embrace a more complex world by combining “good” and “evil.” For just this reason, some people use them.
31: What is Cognitive Cybersecurity?
The concept of cognitive Cybersecurity is to use artificial intelligence to enhance digital security systems. AI in security is anticipated to significantly improve comprehensive security in systems currently exposed to various risks from hackers and other malicious attackers.
32: What is a phishing attack and how can it be prevented?
The fraudulent use of electronic communications to trick and exploit users is known as phishing. Phishing attacks aim to obtain private information such as usernames, passwords, credit card numbers, login credentials for networks, and more. Cyber attackers employ social engineering to trick victims into taking specified actions, including clicking on a harmful link or attachment or willingly disclosing sensitive information by assuming the identity of a trustworthy person or organization over the phone or via email.
Prevention tips:
- Know what a phishing scam looks like.
- Don’t click on that link.
- Get free anti-phishing add-ons.
- Don’t provide your information to an untrusted website.
- Change passwords regularly
33: How will you stay current on the latest Cybersecurity news?
Follow security professionals’ blogs and news sites.
- Search social media for subjects relating to security.
- Examine advisory websites, and vulnerability alert feeds.
- Observe live Cybersecurity events
34: How do you define compliance in terms of Cybersecurity?
Cybersecurity compliance is an organizational risk management strategy that complies with pre-established security controls and safeguards about the administrational procedures used to maintain data confidentiality. Determining and accomplishing IT goals as well as reducing threats through methods like vulnerability management, are all made easier with its assistance.
35: What does a Cybersecurity risk assessment require?
Assessing the risks associated with assets that Cyberattacks might impact is known as Cybersecurity risk assessment. You have to recognize internal and external threats, determine how they might affect issues like data availability, confidentiality, and integrity, and calculate the costs associated with experiencing a Cybersecurity catastrophe. Using the information supplied, you can adjust your Cybersecurity and data protection controls to fit the actual level of risk tolerance for your organization.
36: What is BIOS?
BIOS is a ROM chip found on all motherboards that allows you to access and configure your computer system at the most basic level. Phoenix is an excellent example of a BIOS manufacturer.
37: What are the seven layers of the OSI model?
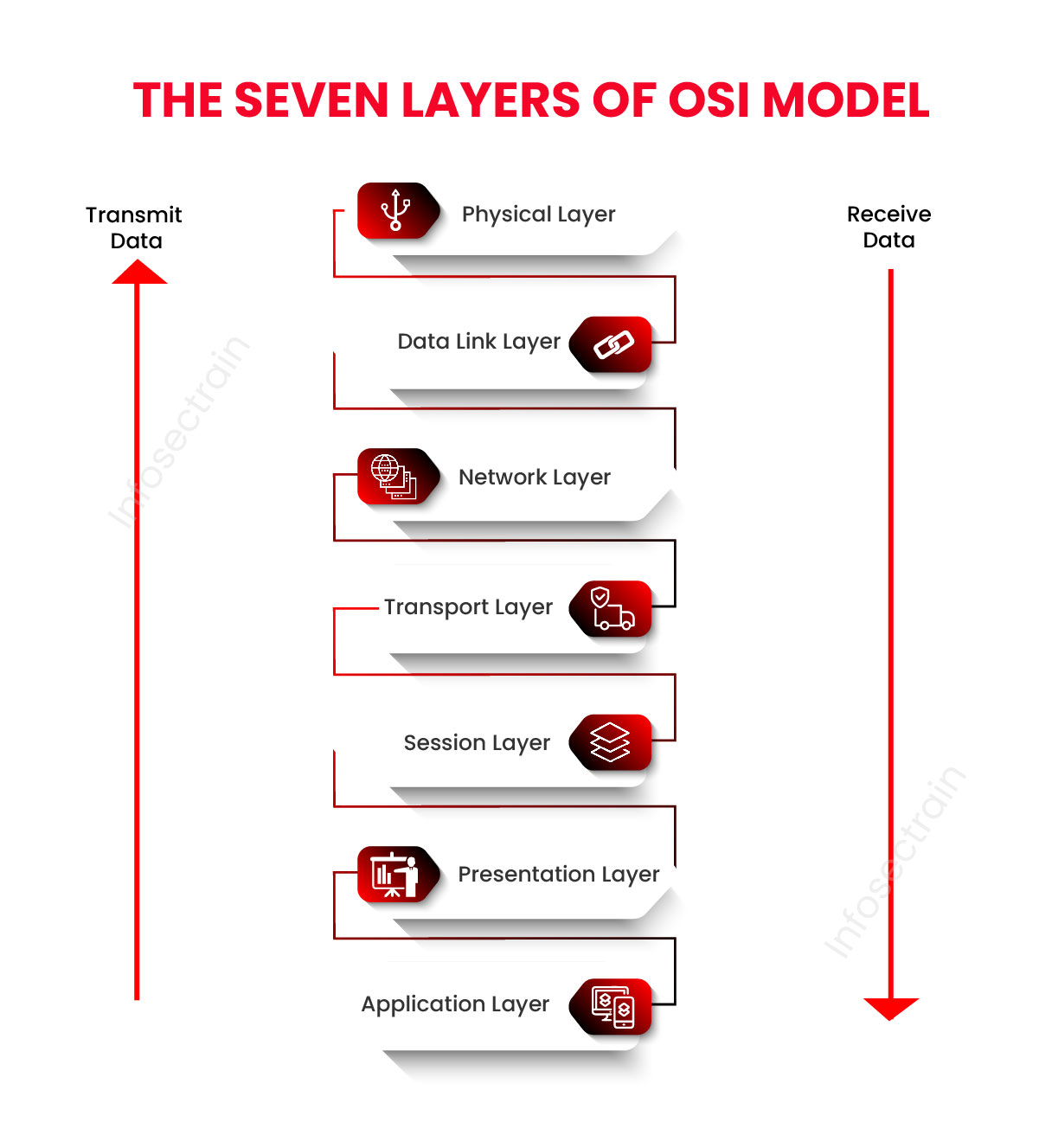
38: What are the many indicators of compromise (IOC) that organizations need to keep an eye on?
- Unusual Outbound Network Traffic
- HTML Response Sizes
- Geographical Irregularities
- Increases in Database Read Volume
- Log-In Red Flags
- Unexpected Patching of Systems
- Web Traffic with Unhuman Behavior
39: What is RDP or Remote Desktop Protocol?
The Microsoft RDP (Remote Desktop Protocol) protocol was created to secure and encrypt application data transfers between client devices, users, and a virtual network server.
It enables administrators to assess and address problems faced by specific subscribers from a distance.
40: Differentiate between the Red team and the Blue team?
An attacker who takes advantage of security gaps in a company is known as a” red team.”
A defense that spots vulnerabilities and fixes them to prevent successful intrusions is known as the “blue team.”
Red teams are offensive security specialists specializing in defending defenses and attacking systems. Defensive security experts on blue teams keep internal network defenses up to date against all Cyberattacks and threats. To evaluate the efficacy of the network’s security, red teams simulate attacks against blue teams. These red and blue team exercises offer a comprehensive security approach that ensures substantial barriers while keeping an eye on changing threats.
41: Describe MITM attacks and how to avoid them?
Man-in-the-Middle” (MITM) attack occurs when a hacker inserts himself into the middle of a conversation between two people to acquire their data.
The following procedures can help you avoid MITM attacks:
- Use VPN
- Utilize powerful WEP/WPA encryption.
- Detect intrusions using IDS
- Require HTTPS
- Based on Public Key Pair Authentication
42: What is an ARP?
The Address Resolution Protocol (ARP) is a communication protocol used to identify the link-layer address, like a MAC address, connected to a particular internet layer address, which is commonly an IPv4 address. An essential part of the Internet protocol suite is this mapping. RFC 826, which defines Internet Standard STD 37, defined ARP in 1982.
Numerous network and data link layer technologies, including IPv4, Chaosnet, DECnet, and Xerox PARC Universal Packet, have been used to implement ARP.
43: Describe System hardening?
System hardening generally refers to a collection of tools and approaches for managing vulnerabilities in an organization’s systems, applications, firmware, and other areas. System hardening reduces security risks by limiting potential attacks and shrinking the system’s attack surface.
The following are the various types of system hardening:
- Database hardening
- Operating system hardening
- Application hardening
- Server hardening
- Network hardening
44: Why is accessing free WiFi dangerous?
Hackers are drawn to free WiFi hotspots for the same reasons that customers are; primarily, the lack of authentication needed to establish a network connection. As a result, the hacker has a fantastic opportunity to gain unrestricted access to unprotected devices connected to the same network.
The capacity of the hacker to place himself between you and the connection point poses the biggest threat to the security of free WiFi. You communicate with the hacker, who would then pass the information to the hotspot rather than the hotspot directly.
In this configuration, the hacker has access to all the data you send over the Internet, including sensitive emails, credit card numbers, and even security codes for your company network.
45: What damage might spyware cause to a company’s data?
Spyware is generally understood as harmful software designed to penetrate your computer system, collect information about you, and send it to a third party against your will. Legitimate software that tracks your data for business purposes like advertising is also called spyware. Malicious spyware is, however, specifically meant to make money off of stolen data.
You are vulnerable to data breaches and the misuse of your personal information due to spyware’s surveillance activities, whether genuine or driven by fraud. The performance of networks and devices is also impacted by spyware, which slows down regular user activity.
46: What is HIDS?
Host-based intrusion detection system (HIDS) is a device that keeps track of activities on a computer system on which it has been placed to spot intrusions and misuse. Then it logs the actions and alerts the appropriate authorities. A HIDS can be compared to an agent that checks to see if anything or anyone, internal or external, has violated the system’s security policy.
47: What is NIDS?
An organization can monitor its cloud, on-premise, and hybrid systems for suspicious occurrences that can point to a compromise with the aid of a network-based intrusion detection system. This includes communications with unknown sources and destinations, port scanning, and policy infractions.
” As a result, they are frequently installed alongside intrusion prevention systems (IPS) that are “active” since they are only intended to alert on unusual activity.
48: What is the difference between information protection and information assurance?
Information assurance, or IA, ensures and controls the risks associated with sensitive data while it is being sent, processed, and stored. Data protection in the system’s integrity, availability, authenticity, non-repudiation, and confidentiality is the primary goal of information assurance. It includes physical approaches in addition to digital measures for data protection.
On the other hand, information security is a practice that involves reducing information risks to secure information. Typically, it reduces the risk of data theft or other unlawful uses, as well as the destruction, discovery, modification, inspection, or recording of sensitive data. It entails taking steps to avoid such occurrences. Information security’s primary goal is to secure data while retaining its confidentiality, integrity, and availability against Cyberattacks and hackers.
49: How frequently should patch management be done?
When a patch is released, it should be managed. When a patch for Windows is released, it should be installed on all devices no later than one month later. The same would be valid for network devices; patch them as soon as they are available. Patch management procedures should be followed.
50: What is SQL Injection, and how to prevent it?
An injection attack known as SQL Injection (SQLi) enables the execution of malicious SQL commands. These commands manage a database server in front of a web application. SQL Injection vulnerabilities allow attackers to get around application security safeguards. The entire content of a SQL database can be retrieved by getting past authentication and authorization of a web page or online application. They can also add, alter, and delete records in the database using SQL Injection.
You can prevent SQL Injection attacks by using the following practices:
- Use prepared statements
- Use Stored Procedures
- Validate user input
Cybersecurity with InfosecTrain
InfosecTrain is a top training and consulting organization specializing in information security and Cybersecurity training and services. All training is delivered by certified instructors who have years of industry experience. You can research and enroll in the best-suited certification course effortlessly to pass the certification exam.







 1800-843-7890 (India)
1800-843-7890 (India)