Top Cybersecurity Trends to Keep Track of in 2021
Last year the corporate world witnessed some high-profile data breaches and sophisticated cyberattacks on companies, government agencies, and individuals. 2020 taught enterprises and organizations a harsh lesson. While some organizations became aware of the significance of cybersecurity, most of them struggled to implement necessary security measures. With a global pandemic and economic crisis, the year brought an unfamiliar set of challenges for the businesses with new and unexpected ways of working that have changed the prevalent norms. Here are the most expected cybersecurity trends in 2021:

Constantly rising IoT related threats
The use of IoT devices is expected to rise in 2021. IoT (Internet of things) provides a lot of advantages to organizations, including productivity and cost-effectiveness. But it is also prone to security threats and is an easy target for hackers. As per the report published by “Security Today”, the number of IoT devices will rise to 35 billion in 2021.
With the increment in the number of IoT users, IoT-related threats are also growing at a rapid pace. The attackers target consumer devices to break into the corporate networks.
According to a report published by “SonicWall”, There was a surge of 66% in IoT malware detection in 2020. That showcases how frequently cybercriminals targeted home networks and remote workers. This year will also be challenging for organizations to protect themselves from IoT-related attacks.
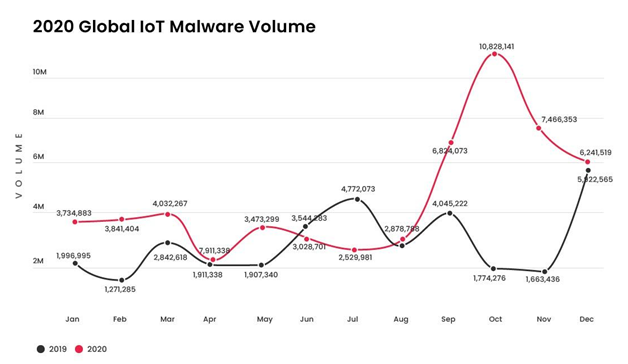
Source: SonicWall Cyberthreat Report 2021
Ransomware Threats :
Ransomware was one of the trending threats in 2020 that targeted organizations, healthcare systems, government agencies, and individuals. Ransomware campaigns such as ‘Sodinokibi’ and ‘Ryuk’ were at the top of the list. Attackers used double-extortion ransomware tactics. In double-extortion, cybercriminals encrypt the organizations’ sensitive data and threaten the organization to leak it if the ransom is not paid. If victim organizations become successful in decrypting and restoring their compromised data, they still have to give the ransom amount to stop it from being exposed publicly. In 2020, during the global pandemic, healthcare organizations were the primary victims of the ransomware attacks. Attackers stole the data of patients from various healthcare centers and asked for payments in bitcoins. Such tactics can become more prevalent in 2021 as well. Researchers have also suspected the correlation between ransomware attacks and the rising value of bitcoins. If it is true, then ransomware can be a growing market in the foreseeable future.
According to cybersecurity ventures, the global estimated cost of ransomware attacks will touch $20 billion in 2021.
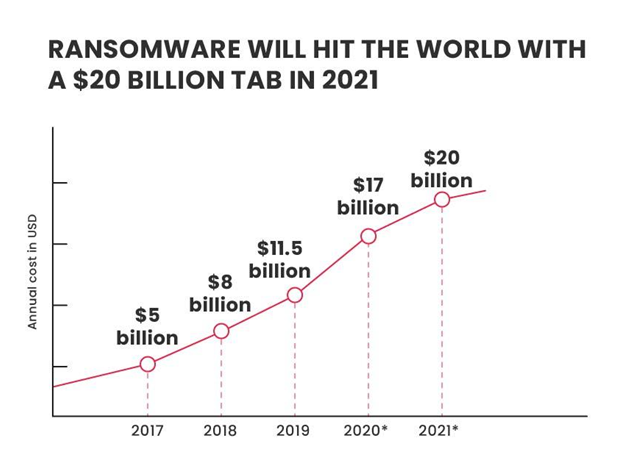
Source: Cybersecurity Ventures report, 2017
Cloud-related Security Threats:
Today organizations are adopting cloud services due to the flexibility and scalability it provides them irrespective of their sizes. The transition to the cloud has posed new security challenges. With the cloud, every information of business is available online. It has given a new set of targets and tools to carry out sophisticated attacks. For example, attackers use Kubernetes and other data science tools like AWS Glue, Sage Maker to perform attacks. Some of the major cloud security issues are misconfiguration, unauthorized access, data breaches, and insecure API (Application Programming Interface). Therefore, security measures to secure cloud platforms should be monitored continuously to prevent data leak incidents.
According to a survey conducted by Analysys Mason, small and medium businesses’ expenditure on cloud security will grow exponentially in upcoming years and will reach USD 20 million by 2024.
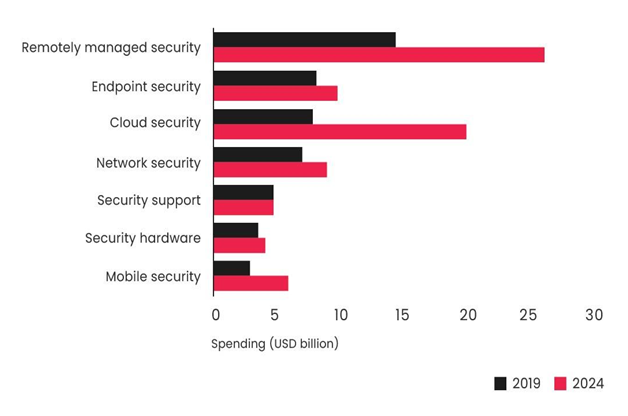
Source: Analysys Mason, 2020
Growing Supply Chain Attacks
Supply Chain Attacks are also referred to as third-party attacks. In this type of attack, attackers break into organizations’ security infrastructure through their third-party service providers or suppliers. The attackers are targeting supply chains to get access to systems and sensitive information of enterprises. The SolarWinds attack is one such example where criminals used supply chains to fulfill their malicious intent. This attack highlighted the risk associated with supply chains. One of the reasons for the rising supply chain attacks is that they can provide the attackers access to the information of large organizations. All they have to do is to compromise a third-party service provider associated with the organization. Once they have infiltrated into the target organization, they will gradually escalate the privileges or remain undetected for a more extended period. As we look forward to 2021, Supply Chain Attacks pose a significant threat to organizations.
According to a report published by Sonatype, the next-generation supply chain attacks increased by 420% in 2020.
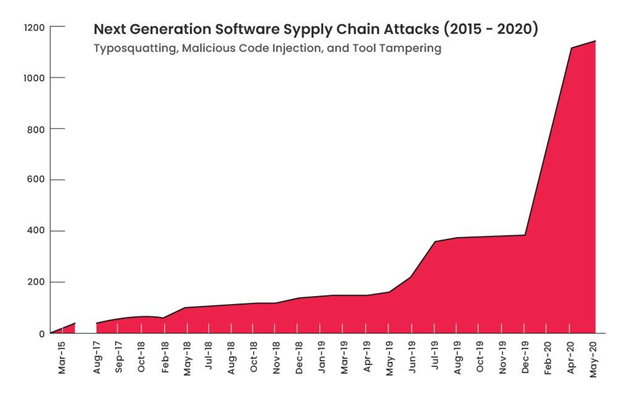
Source: 2020 State of the Software Supply Chain Attack report by Sonatype
The role of SOC will continue to expand
The Security Operation Center (SOC) is a security command center in an organization that proactively monitors networks and systems for suspicious activities. The SOC team responds to the cyberthreats and mitigates potential damage from cyberattacks and data breach incidents. A Security Operation Center offers immense benefits to the organizations, including 24/7 monitoring, reduced incident response time, reduced cost, and better collaboration across various departments. Nowadays, small and medium-size organizations also focus on building their own SOC team due to its cost-effectiveness. The SOC as a service market is estimated to expand from USD 471 million in 2020 to USD 1,656 million by 2025.
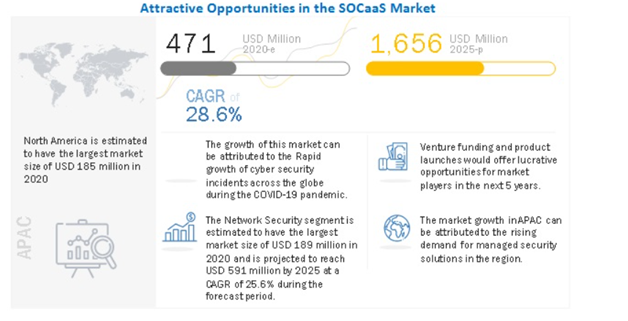
Source: https://www.marketsandmarkets.com
Increased Consumer Interest in Privacy
Consumers’ interest in data privacy changed enormously in the past few years. The recent large-scale data breach incidents such as ‘Equifax’ and ‘ClixSense’ exposed the personal information of millions of consumers worldwide. These incidents lead a large number of consumers concerning the protection of their privacy. Consumers now are worried less about their data being taken away. Rather than they are more interested in knowing how the captured data will be used by the organizations and government agencies in the foreseeable future. As more consumers are aware of the protection of their private data, it is expected that more data privacy regulations will be introduced around the globe in 2021. Apart from this, the organizations will develop new data privacy frameworks and invest in privacy technology.
Insider Threats
Every organization has business partners, third-party vendors, and employees who can access a certain amount of information. These are called insiders, and they are a significant security threat to the organizations. Some of them have a small amount of authorized access to the information, while others can access crucial information. Insider threats are the threats that come from within the organization. The insiders may pose a security threat intentionally or sometimes accidentally. Insider cybersecurity threats are more challenging than any outside attack. According to a Ponemon Institute report, the number of insider threat incidents increased by 47% from 2018 to 2020. In 2018, There were 3,200 insider threat incidents reported. These numbers increased in 2020, and there were a total of 4,716 insider threat incidents reported.
The statistics below showcases the causes for insider threats and their average cost estimation:
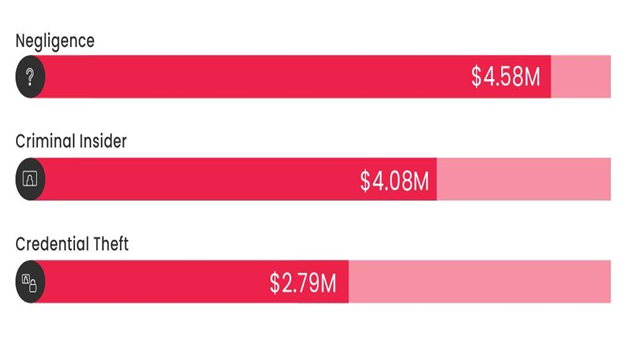
Source: IBM
Experts have predicted that insider threats will continue to haunt organizations in 2021 as well.
Securing Remote Workforce
Due to Covid-19, companies have normalized remote work culture. It has become a permanent aspect of their employment model. In a hurry to keep their business functioning, many organizations shifted to this model overlooking the security challenges and risks associated with it. To overcome the remote workforce challenges, organizations have to strengthen their IT security infrastructure. Implementing security controls, fixing vulnerabilities, and ensuring proactive monitoring are crucial steps for businesses to keep their remote security strategy intact. Zero Trust Network Access (ZTNA) or Security Access Service Edge (SASE) are solutions that organizations must consider to stay protected from cyberattacks.
Wrap up: The cybersecurity trends mentioned above will force organizations to beef up their overall security posture and create a protected cybersecurity landscape. 2021 will also be the year full of transitions. Businesses are expected to spend more on cybersecurity to protect their valuable information assets.
It is an excellent opportunity for professionals looking forward to making a career in the cybersecurity domain. Companies are expected to hire skilled cybersecurity professionals along with lucrative incentives and better salary packages.
Infosec Train is one of the most desirable IT security training providers worldwide, having a proven track record. We offer comprehensive training programs for cybersecurity professionals to provide them with the necessary skills to gear up their security game. Check out the latest schedule of our career-oriented training programs.






 1800-843-7890 (India)
1800-843-7890 (India)