Top Vulnerability Analysis Tools
A successful cybersecurity approach is essential in an era where companies are moving their most critical services into the cyber world. Because there are many vulnerabilities in the cyber world today via which hackers might carry out attacks on companies. Therefore, companies should conduct a vulnerability analysis to identify and resolve the vulnerabilities before the hackers attack. It should be performed on a frequent basis because IT environments are rapidly evolving, and new threats are regularly emerging.

In this article, we will cover what vulnerability analysis is and the top vulnerability analysis tools.
Table of Contents
What is Vulnerability Analysis?
Types of Vulnerability Assessments or Vulnerability Analysis
Top Vulnerability Analysis Tools
What is Vulnerability Analysis?
Vulnerability analysis, often referred to as vulnerability assessment, is a systematic process for identifying, categorizing, and prioritizing potential and existing security vulnerabilities in an organization’s IT systems, network infrastructure, database, servers, and web applications. It also helps to remediate or mitigate the identified vulnerabilities or loopholes.
Types of Vulnerability Assessments or Vulnerability Analysis
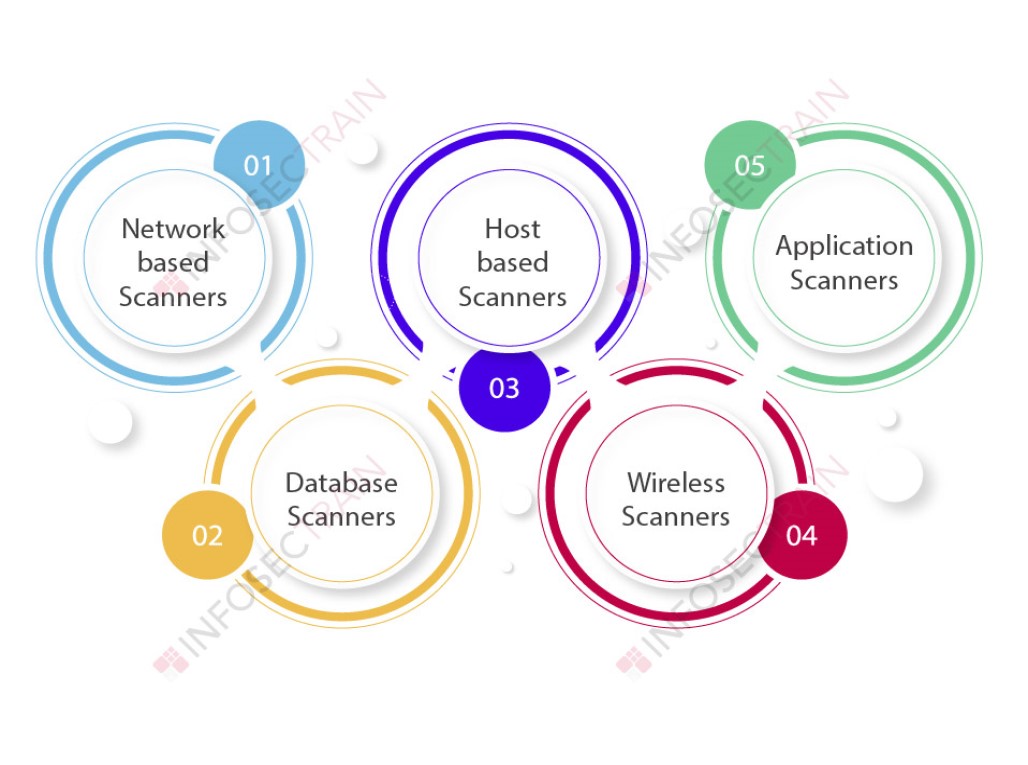
Top Vulnerability Analysis Tools
Various vulnerability analysis tools available can be free, charged, or open-source. Vulnerability assessment scanning tools include different types of scanners, including network scanners, web application scanners, and protocol scanners. These scanners can thoroughly scan every component of your IT infrastructure. Here, we will outline some top vulnerability analysis tools.
1. Nikto2 : Nikto is a free and open-source vulnerability scanner that scans web servers for potentially dangerous programs or files, misconfiguration services, vulnerable scripts, and other issues that can impair the server’s operation. You can receive an instant alert when server installation has security concerns.
2. Netsparker : Netsparker is a paid and open-source web application security scanner used to identify vulnerabilities in web applications and web APIs. It automatically scans vulnerabilities and identifies them, then provides you with detailed reports that include suggestions for solutions. You do not need to verify them manually and save time.
3. Wireshark: Wireshark is an open-source network protocol analyzer and one of the top packet analyzers on the market right now. It is used to assess security issues, troubleshoot network issues, dropped packet analysis, validate network applications, and troubleshoot malicious activities. It operates on various operating systems, including Windows, Linux, Unix, macOS, BDS, Solaris, etc., and it records problems online and conducts analysis offline.
4. OpenVAS: Open Vulnerability Assessment System (OpenVAS) is a free and open-source vulnerability scanner. It is a system of several services and tools that provides a thorough and robust vulnerability scanning and management solution. It can be used in web applications, application servers, databases, OS, networks, and virtual machines to identify and classify potential vulnerabilities and mitigate and remediate them.
5. SolarWinds: SolarWinds is a network management tool that assists businesses in managing systems, networks, applications, and other infrastructure. It provides a Network Configuration Manager to discover network vulnerabilities, monitors, addresses, and safeguards network configurations, and simplifies and enhances network compliance.
6. Nexpose: Nexpose is a free, open-source vulnerability scanner that scans for web applications, networks, and device vulnerabilities. It is used to monitor the real-time exposure of new vulnerabilities. When new applications and devices are exposed to the network, it automatically identifies them, scans them, and evaluates their vulnerabilities.
7. Intruder: An intruder is a paid vulnerability scanner that identifies and prioritizes cybersecurity vulnerabilities in cloud-based storage systems. It reduces or removes the risk posed by possible cybersecurity data breaches and regularly scans for vulnerabilities through an autonomous scanning method.
8. Acunetix: Acunetix is an automated web vulnerability scanner used in web application security testing, and it helps organizations identify and manage vulnerabilities in their web applications.
How can InfosecTrain help you?
InfosecTrain is one of the best security and technology training and consulting firms, focusing on various IT security services and information security training. You can enroll in InfosecTrain’s Certified Ethical Hacker (CEH v12) certification training course to learn more about vulnerability analysis. CEH v12 certification training will teach you how to perform vulnerability analysis using various vulnerability analysis tools to secure your organization. You will learn to find security vulnerabilities in a target organization’s network, communication infrastructure, and end devices.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 07-Mar-2026 | 12-Apr-2026 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |






