Types of Password Attacks
Password cracking is the process of figuring out passwords from data passing through or stored on a computer. It can be done to help someone regain a password they forgot, to ensure passwords are strong enough, or by hackers to get into systems they shouldn’t. Hacking often starts with guessing passwords. Since passwords are important for security, hackers use different methods like guessing, using a list of common passwords, or trying every possible combination until they find the right one. They often succeed because many people use passwords that are easy to guess

Types of Password Attacks
Cracking passwords is an important step for someone trying to break into a computer system. It’s like using an ethical way to do something unethical– getting into a system you’re not supposed to. When someone can’t remember their password, there are four main ways a hacker might try to figure it out:
1. Non-electric Attacks
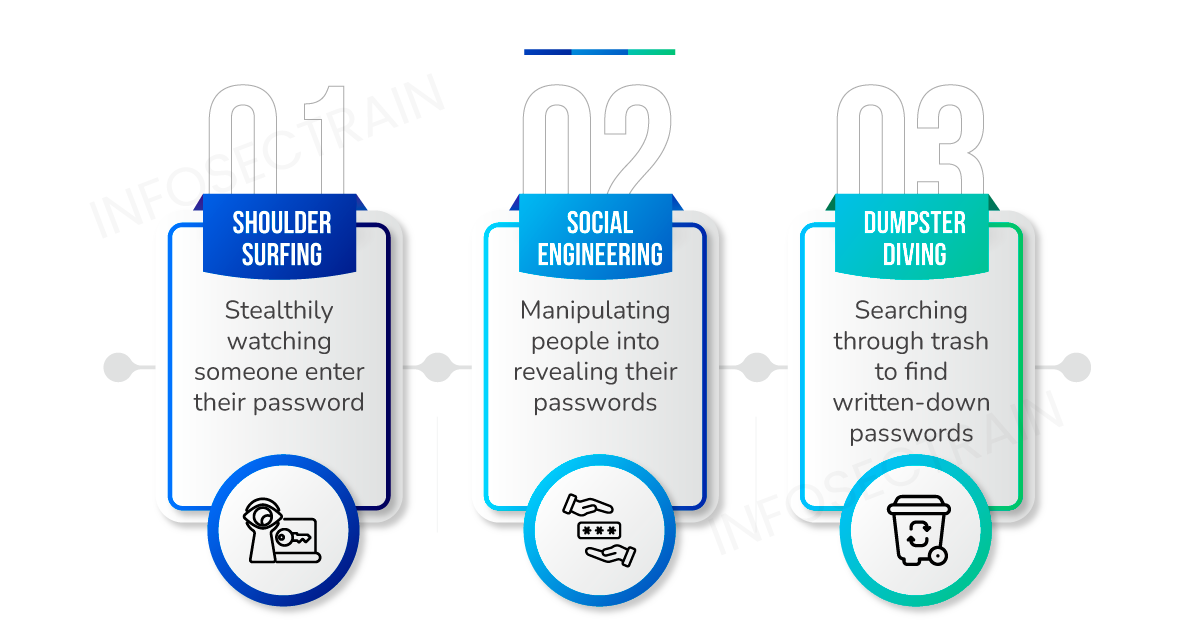
When hackers try to figure out someone’s password without using computers or high-tech gadgets, they often start with the basics. It’s like they’re using old-fashioned detective work to get the secret code to a computer. They might just watch quietly as someone types in their password (that’s called “shoulder surfing“), trick the person into telling them the password (that’s “social engineering“), or even rummage through the trash to find a piece of paper where the password is written down (yep, that’s “dumpster diving“). No fancy computer skills are needed, just some sneaky moves.
2. Active Online Attacks
An active online attack is like trying to pick the lock to the virtual front door. Hackers directly interact with the computer or network. They try every possible key combination until they get it right, which is known as a “Brute Force attack”. Sometimes, they use more sophisticated methods, like a “Dictionary attack,” like checking if your password is a common word or phrase. There are also ”Rule-based attacks” where they modify common passwords based on certain rules to guess the right one. Hackers can also use malware, such as “Trojans” or “Spyware,” to intercept your password as you type it. There’s also a sneaky tactic called “Password Guessing/Spraying,” where attackers spray common passwords across many accounts, hoping to get a hit. For those with greater technical skills, there are advanced strategies like “LLMNR/NBT-NS Poisoning,” which targets network communication to intercept passwords, or cracking specialized password systems like “Kerberos,” which is used in secure networks.

3. Passive Online Attacks
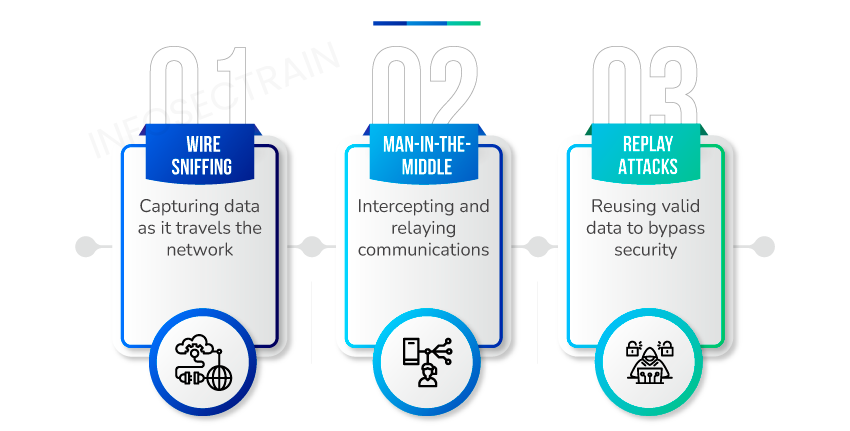
Passive online attacks are like eavesdropping. Hackers don’t break into your house but listen in on the conversation. They use “Wire Sniff” tactics to secretly catch passwords as they travel across the network. Or they perform a “Man-in-the-Middle Attack,” where they insert themselves into a conversation you’re having with a secure service to intercept the password. Then there’s the “Replay Attack,” which is similar to a hacker recording you unlocking your door and then using that recording to do the same when you’re not around.
See how Man-in-the-middle attack works:

4. Offline Attacks
Let’s take an example to understand offline attacks: assume a thief who has stolen a safe but doesn’t open it on-site. They take it somewhere safe to crack it open. This is what hackers do in “Offline Attacks.” They don’t interact with your system directly; instead, they take data like password files and try to crack them elsewhere. “Rainbow Table Attacks” involve using a pre-made cheat sheet that matches the hashed values with their possible plain-text versions. And with “Distributed Network Attacks,” they divide and conquer, using multiple systems to try cracking passwords, much like a group of thieves working together to break into a safe.

Master CEH with InfosecTrain
Ethical hacking is a detailed and challenging field that requires a deep understanding of cybersecurity. By taking courses like the Certified Ethical Hacker at InfosecTrain, learners can improve their skills in checking security and improving network systems. This training is designed to give learners the skills and knowledge to help organizations strengthen their security properly. Sign up for InfosecTrain’s CEH training to become a top expert in keeping information safe.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Jul-2025 | 16-Aug-2025 | 09:00 - 23:00 IST | Weekend | Online | [ Open ] |

 1800-843-7890 (India)
1800-843-7890 (India)