Types of Security Controls
Security Controls or cyber security controls are the most important factor used to develop the actions taken to prevent the organization’s security risks. IT security controls are parameters implemented to protect the organization’s data and assets.

In layman’s terms, any measure used to identify, mitigate, counteract, or reduce security risks is known as a security control. Types of IT security controls can be broadly divided into three categories:
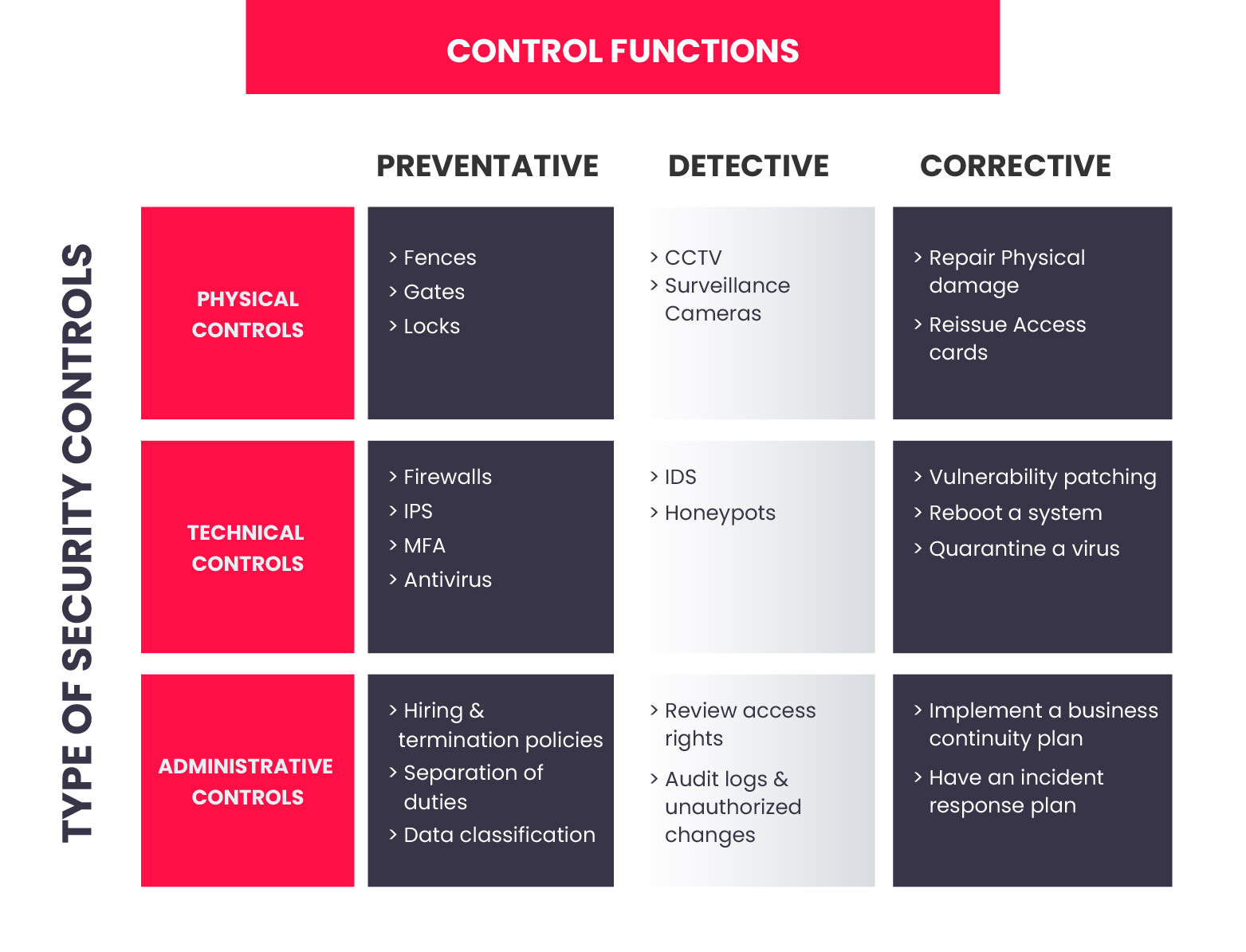
1. Administrative Control: Administrative Control is a set of security rules, policies, procedures, or guidelines specified by the management to control access and usage of confidential information. It includes all the levels of employees in the organization and determines the privileged access to the resources to access data.
- User Management
- Privilege Management
- Employee Security, Clearance, and Evaluation
- Employee training and awareness, etc.
2. Physical Control: Physical Control is a set of IT security controls implemented physically to prevent unauthorized access to the data and security risks. Some examples of physical controls in cyber security controls are:
- Surveillance cameras
- Biometrics
- Identity Cards
- Alarm systems, etc.
3. Technical Control: Technical Control is to control the access of confidential information over the network using technology. Technical functions are involved in managing and controlling the access of the employee. Some examples of technical controls are:
- Access controls
- Firewalls
- Network Authentication
- Encryption, etc.
Functions of Security controls
While implementing security controls, the function of the cyber security control is broadly specified into seven categories:
1. Directive Controls
Directive Controls are the mandatory controls that are implemented to monitor the regulations. It provides guidance primarily aligned with the organizations required to follow, like policies, regulations, etc.
2. Deterrent Controls
Deterrent Controls are deployed to discourage the violation of a security function, and it helps to reduce the chances of a deliberate attack. Deterrent Controls help to make intelligent decisions and deter the way that is not secure to use.
3. Preventive Controls
Preventive Controls are used to prevent or avoid security incidents in the organization. It helps to mitigate unauthorized activities by indulging preventive methods in the organization.
4. Compensating Controls
Compensating Controls are the alternative methods that support the requirement of actual security control implemented. The role of the compensating Control is to provide a similar level of assurance even if the attacker has compromised the actual security control.
5. Detective Controls
Detective controls are used to detect and alert unauthorized or unwanted activities within the organization. It helps to detect and react to security violations using tools, processes, and best practices.
6. Corrective Controls
Corrective Controls are used to remediate or mitigate the effect of a security incident. It includes measures to mitigate and prevent the same security incident from recurrence.
7. Recovery Controls
Recovery Controls are deployed to recover and restore the operating system to normal condition after the security incident.
Become a Security Administrator with InfosecTrain
Implementing a security control framework is crucial for organizations of all sizes to safeguard their critical data and assets. By combining administrative, physical, and technical controls, organizations can proactively mitigate risks, deter attacks, and ensure swift recovery from security incidents. Regularly evaluating and updating security controls is essential to maintain their effectiveness against emerging threats.
InfosecTrain has benefitted many professionals who cleared their CompTIA Security+ certification seamlessly. It provides an expert-curated CompTIA Security+ online training course that covers the latest security trends, vulnerabilities, risk management, and incident response concepts. If you want to become a Security Administrator, get enrolled, trained, and certified.







 1800-843-7890 (India)
1800-843-7890 (India)