Understanding Advanced Persistent Threats (APT)
Advanced Persistent Threats is a dedicated subsection of CEH Module 7: Malware Threat, which breaks down the elements of APTs. These threats represent the convergence of advanced skills and strategies, persistent efforts by attackers to remain integrated within a network, and the significant threat posed to organizations across various sectors such as financial, healthcare, defense, aerospace, and business operations. In this article, we will discuss Advanced Persistent Threats (APT).

Understanding APT (Advanced Persistent Threats)
An APT (Advanced Persistent Threats) is a network attack that exploits a series of sophisticated methods to gain unauthorized access to a target network and establish a foothold for a long period. The ‘advanced‘ nature of these threats originated from the use of cutting-edge techniques designed to exploit vulnerabilities. These vulnerabilities are not known to the public or security experts, which is why they are also called ‘zero-day’ exploits.
The ‘persistent‘ aspect of APTs is characterized by the attacker’s relentless efforts to remain undetected within the network for as long as possible. This persistence is facilitated by a Command-and-Control (C&C) infrastructure that continuously extracts data while secretively monitoring the network’s activities. Unlike other forms of cyberattacks that seek immediate gratification through destruction or ransomware, APTs play the long game, focusing on the strategic extraction of valuable information.
Characteristics of APT (Advanced Persistent Threats)
Below are the main Characteristics of APT (Advanced Persistent Threats)
- Objectives: The attacker’s main goal is to steal important and confidential information or to achieve some big-picture business advantage.
- Timeliness: The attackers spend a lot of time, starting with looking for weak spots in a system to the point where they can come and go as they please without being noticed.
- Resources: To carry out an attack, attackers require a mix of expertise, fancy hacking gadgets, and secret strategies.
- Risk Tolerance: Attackers are willing to play a very long and patient game, staying under the radar for as long as it takes to get what they want without getting caught.
- Skills and Methods: Attackers have a toolbox of sophisticated skills and custom-built tools tailored for each mission.
- Actions: An APT is like a series of spy moves in a high-stakes movie; they have a set of technical tricks that make them stand out from your everyday hacking attempts.
- Attack Origination Points: They try time and again, in many different ways, to break into a system until they find a way in.
- Numbers Involved in the Attack: This is about the number of computers or devices that the attackers manage to compromise or control in their attack.
- Knowledge Source: Attackers do their homework online, gathering detailed information about their targets to tailor their attacks precisely.
- Multi-phased: These attacks don’t happen all at once. They’re like episodes in a series, each step carefully planned, from scoping out the place to grabbing the goods and getting away with it.
- Tailored to the Vulnerabilities: The attackers make special keys to fit the locks they find in the target’s system—no one-size-fits-all here.
- Multiple Points of Entry: Attackers set up several secret backdoors so they can always get back into the network, even if one gets closed.
- Evading Signature-Based Detection Systems: APTs are like stealthy ninjas that can slip past security alarms and cameras, which in the digital world are firewalls and antivirus programs.
- Specific Warning Signs: Strange things that might signal an APT could be happening, like unexpected activity in user accounts or weird database movements—kind of like finding mysterious footprints in a supposedly empty house.
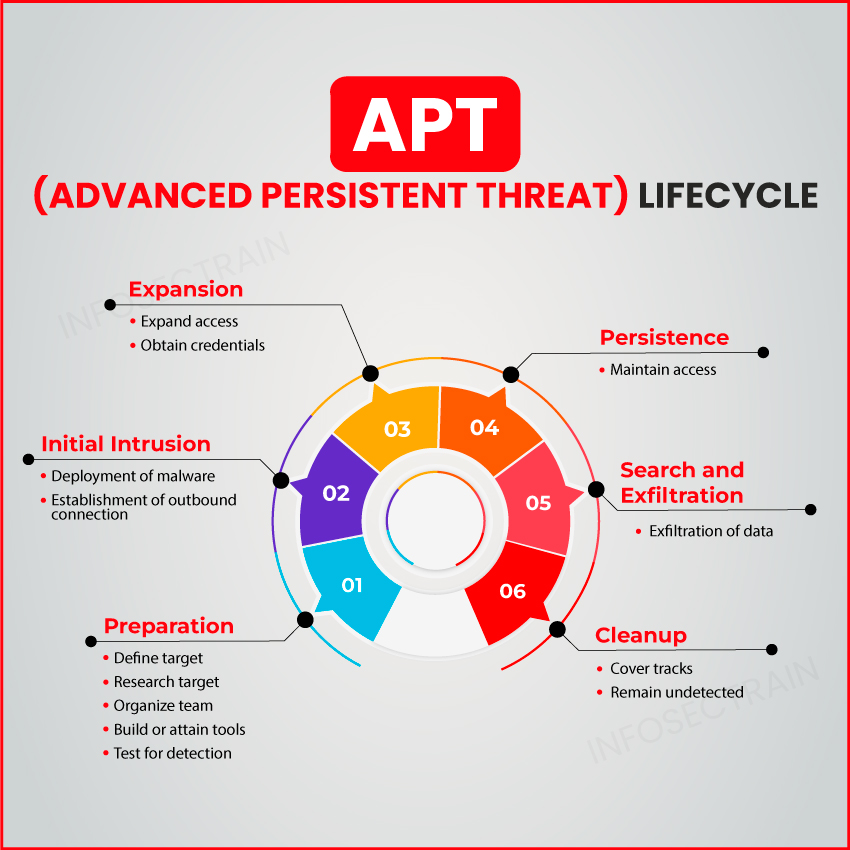
Phases of the Advanced Persistent Threats (APT) lifecycle
The Advanced Persistent Threats (APT) Lifecycle is like the story of a complex heist, meticulously executed from planning to escape. Here are the different phases of the Advanced Persistent Threats (APT) lifecycle:
1. Preparation: The Plotting Stage
Before the action begins, there’s a lot of groundwork to be done. This is where the attackers decide who they’re going to target and start gathering intel on them. They put together their team, equip themselves with the tools of the trade, and run drills to make sure they won’t get caught on the first try.
2. Initial Intrusion: The Break-In
This is where the cyber attackers make their first move, slipping their malware into the target’s system, like planting a bug in a secure building. It’s all about getting in without setting off the alarms and establishing a secret way to communicate back home.
3. Expansion: Spreading Out
Once they’re in, they start to explore, getting their hands on more credentials and access rights. It’s like finding more doors to open and more hidden paths within the building, making sure they can reach all the valuable stuff.
4. Persistence: Holding the Fort
The attackers set up shop. They make sure they can stay inside, maintain their access, and avoid getting kicked out. It’s about staying hidden in the shadows, continuing the heist without being noticed.
5. Search and Exfiltration: The Grab and Go
Now, they start looking for the treasure – the data. Once they find the valuable data, they begin sneaking it out. It’s a delicate process, moving the stolen goods out without raising the alarm.
6. Cleanup: Leaving No Trace
After they’ve got what they came for, they cover their tracks, cleaning up any clues they might have left behind. It’s like wiping down for fingerprints, ensuring they leave the scene as if they were never there, ready to strike again another day.
Master CEH with InfosecTrain
Ethical hacking is a detailed and challenging field that requires a deep understanding of cybersecurity. By taking courses like the Certified Ethical Hacker at InfosecTrain, learners can improve their skills in checking security and improving network systems. This training is designed to give learners the skills and knowledge to help organizations strengthen their security properly. Sign up for InfosecTrain’s CEH training to become a top expert in keeping information safe.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Apr-2025 | 01-Jun-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Close ] | |
| 11-May-2025 | 28-Jun-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 31-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 07-Jun-2025 | 13-Jul-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 27-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)