Understanding Cyberbullying: Types & Impacts
Cyberbullying has become a major global concern as online interactions become just as common as face-to-face conversations. In virtual environments, people from different backgrounds and ages may be targeted, which can lead them to engage in or experience negative behaviors. This phenomenon occurs when someone uses digital technology, like social media, emails, messaging apps, etc., to harass, threaten, or embarrass victims. Unlike traditional bullying, its digital nature means it can follow the victim anywhere, making it a 24/7 concern.

Understanding cyberbullying involves recognizing its various types, from posting harmful content and sharing sensitive information without consent to sending threatening messages and impersonation. This post delves into the complexities of cyberbullying, offering insights to help navigate and counteract this most pressing issue.
Where Cyberbullying is Most Commonly Encountered?
- Emails
- Social media platforms, including Instagram, Twitter, Facebook, etc.
- Messaging apps such as WhatsApp, iMessage, Messenger
- Online forums and message boards
- Online gaming communities
- Dating apps and websites
- Chat rooms on various websites or platforms
- Image-sharing platforms like Snapchat and Pinterest
- Online learning platforms like virtual classrooms or discussion boards
- Comments sections on websites and video-sharing platforms
Types of Cyberbullying
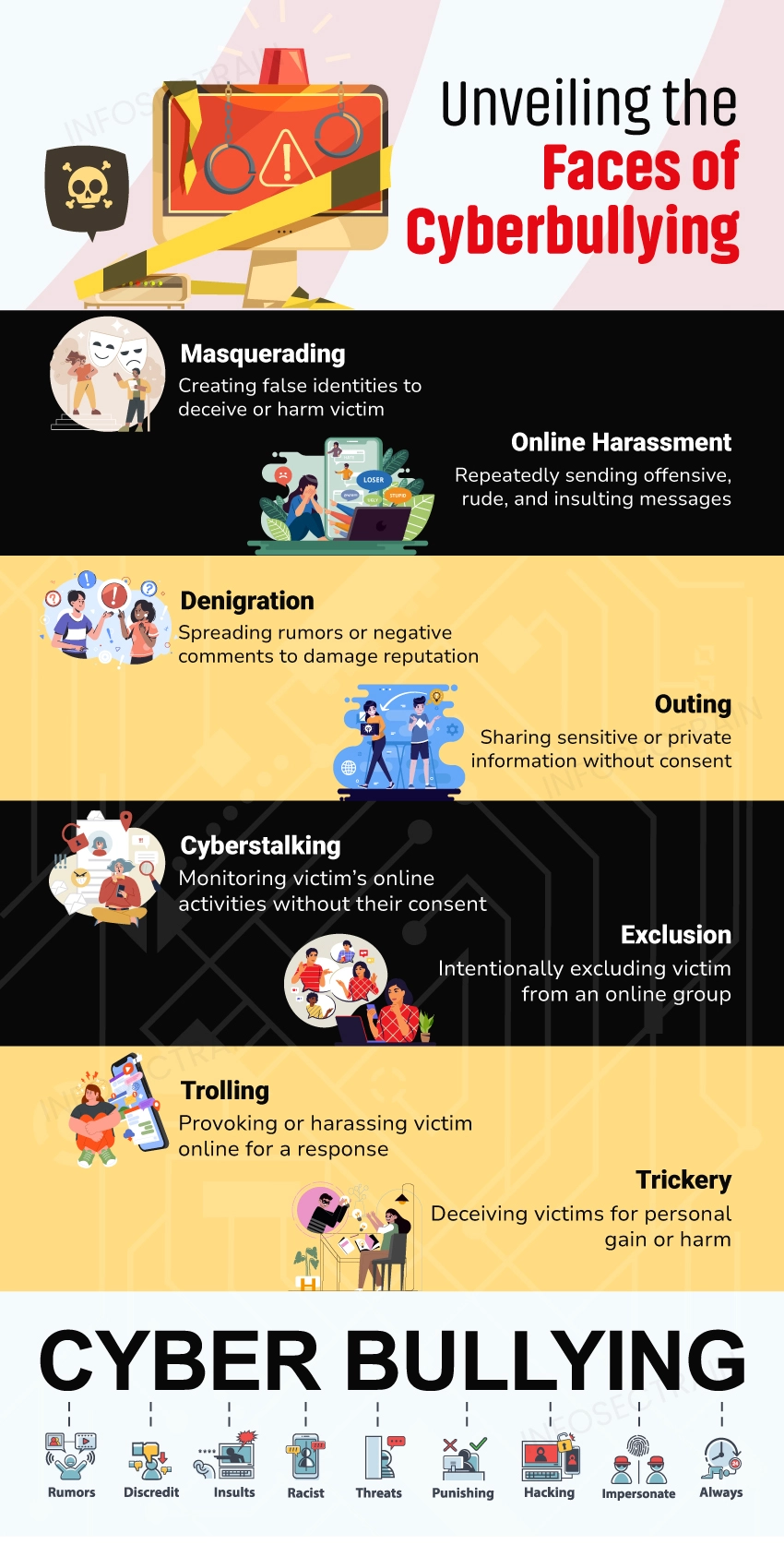
- Masquerading: Cyberbullies create fake profiles or impersonate someone else online to deceive, manipulate, or humiliate the victim. They may use these profiles to spread false information, manipulate others, or damage the victim’s reputation.
- Online Harassment: Cyberbullies repeatedly send offensive, rude, and insulting messages to a victim or a group of people. It may include threats, vulgar language, or insulting comments to demean the victim.
- Denigration/Dissing: Cyberbullies spread rumors or negative comments about victims online to damage their reputation or social standing. It can include posting embarrassing photos or videos, spreading false information, or making hurtful comments about the victim.
- Trolling: Cyberbullies intentionally provoke or disturb others online through inflammatory, irrelevant, or offensive comments or actions.
- Outing/Doxing: Cyberbullies publicly share private or sensitive information about a victim without their consent. It may include sharing personal photos, videos, or confidential details, invading privacy, and raising safety concerns.
- Cyberstalking: Cyberbullies or cyberstalkers use online platforms to monitor, harass, or intimidate the victims. They constantly monitor the victim’s online activity, their behavior, and send threatening messages that cause fear and distress.
- Exclusion: Cyberbullies intentionally target left-out individuals from online groups, chats, or social activities to isolate and hurt them emotionally. This can significantly impact a person’s mental health and social standing.
- Trickery: Cyberbullies may use deception or manipulation to trick the victims into revealing personal information, sharing embarrassing photos or videos, or engaging in harmful behavior. This can lead to feelings of shame and betrayal.
Impacts of Cyberbullying
Cyberbullying’s impacts can be severe and far-reaching:
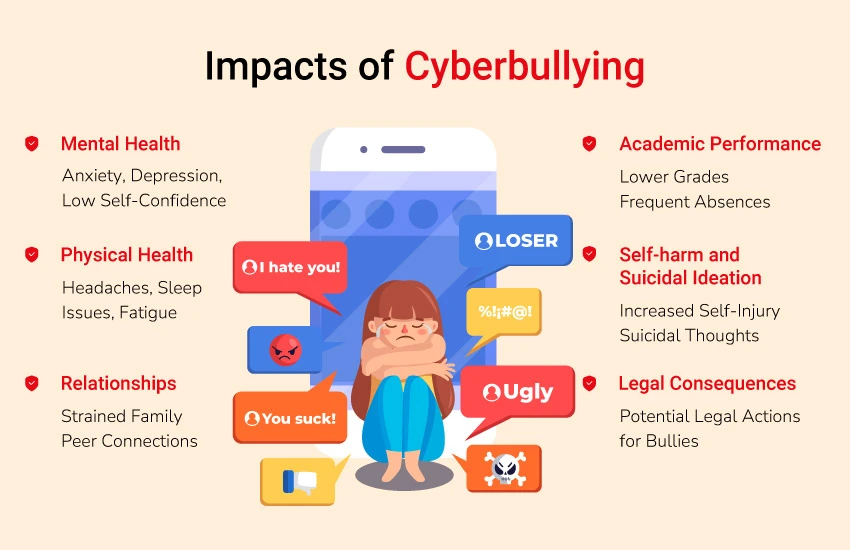
- Mental Health: Individuals who are the targets of cyberbullying may experience depression, anxiety, stress, and low self-confidence. They may also be dealing with symptoms of Post-traumatic Stress Disorder (PTSD) due to the continuous harassment and trauma they face online.
- Physical Health: Stress and anxiety can come out in physical symptoms like headaches, stomachaches, and sleeping disturbances.
- Relationships: Cyberbullying can impact the relationships with family, friends, and peers. Victims may feel alone and distant, which can make them hesitant to interact socially and struggle to form new connections.
- Academic Performance: Cyberbullying can have a negative impact on academic performance, such as absences from work, making it difficult to concentrate, and decreased motivation to participate in school and college activities.
- Self-harm and Suicidal Ideation: In extreme situations, cyberbullying can lead to self-harm, suicidal thoughts, or even suicide attempts. Victims may feel hopeless, overwhelmed, and powerless by the constant harassment and abuse.
- Legal Consequences: Cyberbullying can also lead to legal repercussions, especially when it involves threats, harassment, or the distribution of explicit or illegal content. People who commit crimes may be subject to criminal charges, civil lawsuits, or disciplinary actions from educational institutions.
How to Prevent Cyberbullying?
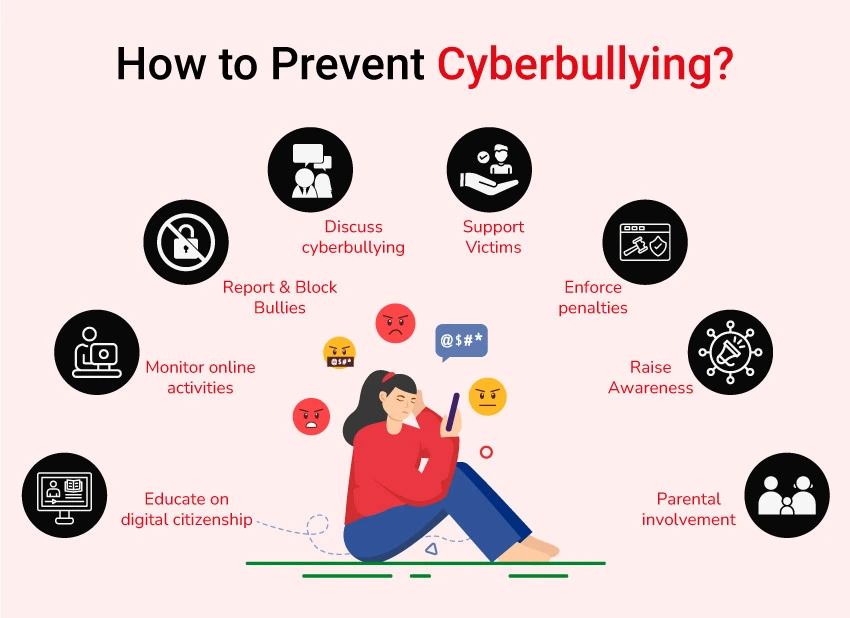
- Educate on digital citizenship and empathy
- Monitor online activities of minors
- Encourage victims to report incidents
- Use privacy settings to block bullies
- Start conversations about cyberbullying
- Offer emotional support to victims
- Enforce penalties for cyberbullying
- Raise awareness through campaigns
- Engage parents in monitoring and educating children about online behavior
Understanding the different facets of cyberbullying is essential for concerned parents, educators, and anyone interested in protecting themselves and others in an increasingly connected world.
How Can InfosecTrain Help?
To protect yourself and your personal information in cyberspace, it is crucial to have a good understanding of cybersecurity fundamentals. InfosecTrain offers a Cyber Security Orientation Program for newcomers interested in starting a career in this field. As a prominent training and consulting firm, InfosecTrain specializes in information security, providing courses taught by certified professionals with extensive experience.







 1800-843-7890 (India)
1800-843-7890 (India)