Understanding the Basics of NetBIOS Enumeration
In the Certified Ethical Hacker (CEH) curriculum, Module 4 focuses on Enumeration, where NetBIOS Enumeration is a key area of study. This sub-section of CEH module 4 delves into the details of NetBIOS enumeration, outlining the various techniques and methods used to gather information from systems within a Windows network. Through this subsection, you will explore how to utilize NetBIOS, a pivotal protocol for network services, to uncover valuable data such as user names, machine names, network shares, and services running on the target hosts.

What is NetBIOS Enumeration?
NetBIOS enumeration is a method covered in CEH (Certified Ethical Hacker) Module 4, focusing on the ‘Enumeration‘ phase of ethical hacking. It involves extracting information about Windows networks via the NetBIOS protocol, which facilitates network communication for services like file sharing and printing.
Techniques in NetBIOS enumeration can reveal network resources, user accounts, and other critical details that could be leveraged for network mapping or vulnerability assessment. Ethical hackers use this process to identify potential security risks in a network’s configuration and to strengthen defenses against potential attackers who could use the same information for malicious purposes.
Nbtstat Utility
The Nbtstat utility is a tool provided by Windows for resolving problems associated with NetBIOS name resolution. It uses the nbtstat command to remove and rectify preloaded entries, applying a variety of case-sensitive switches. Attackers might use Nbtstat to gather details such as NetBIOS over TCP/IP statistics, NetBIOS name tables of both local and remote computers, and the contents of the NetBIOS name cache.
The command structure for nbtstat is as follows:
| nbtstat [-a RemoteName] [-A IP Address] [-c] [-n] [-r] [-R] [-RR] [-s] [Interval] |
The Nbtstat utility features various parameters and their corresponding functions as follows:
| Nbtstat Function | Parameters |
| -a RemoteName | Shows the NetBIOS name table for a specified remote computer, where ‘RemoteName’ is the NetBIOS name of that computer. |
| -A IP Address | Reveals the NetBIOS name table of a remote computer identified by its IP address in dotted decimal format. |
| -c | Enumerates the NetBIOS name cache contents, including the table of NetBIOS names and their associated resolved IP addresses. |
| -n | Displays names that have been locally registered by NetBIOS applications like servers and redirectors. |
| -r | Counts all names that have been resolved either by broadcast or by a WINS server. |
| -R | Clears the name cache and refreshes all entries with the #PRE tag from the Lmhosts file. |
| -RR | Releases and then re-registers all names with the name server. |
| -s | Lists the NetBIOS session table, converting destination IP addresses into their corresponding NetBIOS names. |
| -S | Outputs the current NetBIOS sessions and their status along with the IP addresses. |
| Interval | Repetitively shows selected statistics, pausing for a defined number of seconds between displays as indicated by ‘Interval’. |
Some of the Nbtstat utility commands include:
1. Run to retrieve the NetBIOS name table from a remote computer
| nbtstat -a |
2. Details of the NetBIOS name cache, which includes the NetBIOS names and their corresponding resolved IP addresses.
| nbtstat -c |
NetBIOS Enumeration Tools
NetBIOS Enumeration Tools probe and scan networks across a specific spectrum of IP addresses and compile lists of computers to uncover security gaps or vulnerabilities in networked systems. These tools can identify various aspects such as operating systems (OS), user accounts, groups, Security Identifiers (SIDs), password policies, services, service packs, hotfixes, NetBIOS shares, transport protocols, sessions, disk drives, and security event logs.
1. NetBIOS Enumerator : NetBIOS Enumerator is one such tool for enumeration that facilitates the use of remote network support and interacts with other web protocols, including SMB. Attackers employ NetBIOS Enumerators to gather information such as NetBIOS names, user account names, domain names, and Media Access Control (MAC) addresses across a defined range of IP addresses.
| nmap -sU -p 137 –script nbstat.nse |
- nmap: This is the network mapping tool itself.
- -sU: This flag tells Nmap to perform a UDP scan.
- -p 137: This specifies that the scan should be conducted on port 137, which is the NetBIOS name service port.
- –script nbstat.nse: This instructs Nmap to use the nbstat script from its NSE (Nmap Scripting Engine) system, which is designed to enumerate NetBIOS information.
Output of the command
- NetBIOS name: It indicates the NetBIOS name of the server, for example “SERVER2022”.
- NetBIOS user: The user of the NetBIOS session
- NetBIOS MAC: The MAC address associated with the NetBIOS name
The <target> placeholder would be replaced with the IP address or hostname of the system you’re scanning.
SNMP (Simple Network Management Protocol) Enumeration
SNMP (Simple Network Management Protocol) enables network managers to control network devices remotely. Despite its utility, SNMP is prone to security issues, notably in auditing, which can be exploited for unauthorized data collection.
This section provides insights into how SNMP is used for enumerating accounts and devices, and outlines the various tools for performing SNMP enumeration in the context of network security.
SNMP (Simple Network Management Protocol) is a protocol used at the application layer, operating over UDP to manage and oversee network components like routers, hubs, and switches across IP networks.
It is implemented on various network devices across platforms like Windows and Unix. The protocol facilitates SNMP enumeration, which involves compiling an inventory of user accounts and network devices through SNMP. This process involves the interaction between two key software elements: the SNMP agent, which resides on the network devices, and the SNMP management station, which sends out requests and receives responses from the agent. Network infrastructure components, such as routers and switches, typically have SNMP agents that help manage the system.
The management station issues requests and the agent responds with the relevant configuration details. Additionally, SNMP management stations can send instructions to modify certain configurations on the agent. They also receive notifications, known as traps, from the agent in case of unusual events, like a system reboot or an interface failure.
- Two types of SNMP community strings exist:
– Read community string: Public by default, used for viewing device/system configurations.
– Read/write community string: Private by default, permits remote configuration changes. - Attackers may exploit default community strings to gather details about a device.
- Through SNMP enumeration, attackers can obtain data about network resources (hosts, routers, devices, shares) and network details (ARP tables, routing tables, traffic patterns).
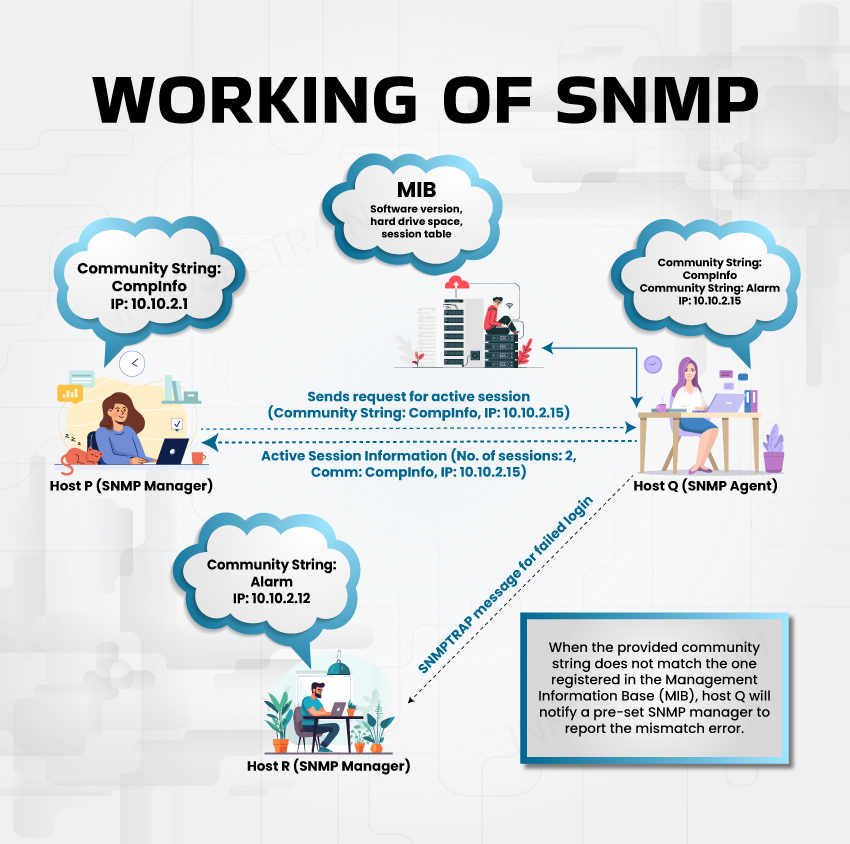
Working of SNMP
- GetRequest: An SNMP manager uses this to request data from an agent.
- GetNextRequest: This allows an SNMP manager to sequentially fetch data from an array or table in an agent’s database.
- GetResponse: An SNMP agent uses this to deliver the requested information back to the manager.
- SetRequest: With this command, an SNMP manager can alter the value of a parameter in an agent’s Management Information Base (MIB).
- Trap: This is sent by an SNMP agent to notify the manager about specific events or irregularities detected on the network device.
LDAP Enumeration
Multiple protocols facilitate communication and the transfer of data across network entities, transporting crucial details about network resources and associated data. If an outsider manages to enumerate this data by manipulating these protocols, it could lead to unauthorized access and potential exploitation of network services. Lightweight Directory Access Protocol (LDAP) is a specific protocol for retrieving directory listings. This section is dedicated to discussing LDAP enumeration, detailing the information that can be extracted through LDAP enumeration, and exploring the tools used in the process.

LDAP Enumeration Tools
Several tools are available for LDAP enumeration, which is the process of extracting information from LDAP directories:
- Nmap: This network scanning tool includes LDAP enumeration scripts such as LDAP-search and LDAP-brute, which can be used to discover and interact with LDAP services.
- enum4linux and windapsearch: These are tools mentioned alongside ldapsearch and Jxplorer as part of the LDAP enumeration toolkit available to security professionals.
- ad-ldap-enum: A Python script used for enumerating Active Directory objects like users, groups, and computers. It is especially useful in large Active Directory environments where other tools may not be as efficient.
- JXplorer: An open-source LDAP browser and editor that works across different platforms. This tool allows users to search, read, and edit any LDAP directory service with an LDAP or DSML interface.
- msLDAPDump: This tool is designed to facilitate LDAP enumeration within domain environments. It offers an easy-to-use interface that wraps the lpap3 library from Python.
CEH with InfosecTrain
Ethical hacking is a complex and multi-phase process that requires deep knowledge and security certifications. Professionals can improve their security assessment and network architecture skills through ethical hacking courses, such as the Certified Ethical Hacker (CEH v12) training provided by InfosecTrain. This training provides individuals with the essential skills and methods needed to perform sanctioned hacking into organizations.
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 16-Aug-2025 | 28-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 06-Sep-2025 | 12-Oct-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 20-Sep-2025 | 26-Oct-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)