Web Vulnerability Scanning with Nikto
Introduction to Nikto
Nikto is an open-source web vulnerability scanner widely used by cybersecurity professionals to identify security issues in web servers and applications. Created to be both comprehensive and user-friendly, Nikto quickly scans web applications for vulnerabilities, misconfigurations, and outdated components. As it is freely available, it is accessible to professionals, students, and hobbyists alike, providing a hands-on tool for real-world vulnerability assessment.

Key Features of Nikto
- Detection of Over 6,700 Vulnerabilities: Nikto scans for a vast array of issues, including server misconfigurations, insecure files, outdated versions, and more.
- Fast Scanning and Reporting: Nikto is designed to be thorough yet fast, providing detailed results in just a few minutes.
- Customizable Scan Options: Nikto allows custom configurations, such as choosing specific modules, target directories, or user agents, making it adaptable for different scanning needs.
Getting Started with Nikto
To use Nikto effectively, you’ll first need to install and configure it. Here is how to set up Nikto on different operating systems.
Installing Nikto
1. On Linux: Most Linux distributions allow you to install Nikto through package managers, or you can install it directly from the source.
Install using apt (Debian/Ubuntu)
| sudo apt update sudo apt install nikto |
Installing from source (for any Linux distribution)
| git clone https://github.com/sullo/nikto.git cd nikto sudo chmod +x nikto.pl |
On macOS: You can use Homebrew to install Nikto
| brew install nikto |
2. On Windows: Nikto is a Perl-based application, so you will need to install Perl first. Afterward, you can use Git Bash or any command line to run Nikto.
Step 1: Install Perl for Windows (ActivePerl)
Step 2: Clone the Nikto repository
| git clone https://github.com/sullo/nikto.git cd nikto |
Command to check the current version of Nikto’s plugins and database:
| nikto.pl -Version |

Nikto is now set up, and you’re ready to perform your first scan!
Core Functionalities of Nikto
Nikto offers a wide range of scanning capabilities, helping you detect various types of vulnerabilities, including:
- Outdated Software: Identifies outdated versions of software components on the server.
- Default Files and Directories: Checks for files like php or admin directories left from development.
- Configuration Issues: Detects common misconfigurations, such as HTTP methods (OPTIONS, TRACE), that may increase attack surfaces.
- Security Headers: Checks for missing or misconfigured security headers that could expose vulnerabilities.
Here are commands to use Nikto’s core scanning functionalities effectively.
Running Basic Scans with Nikto
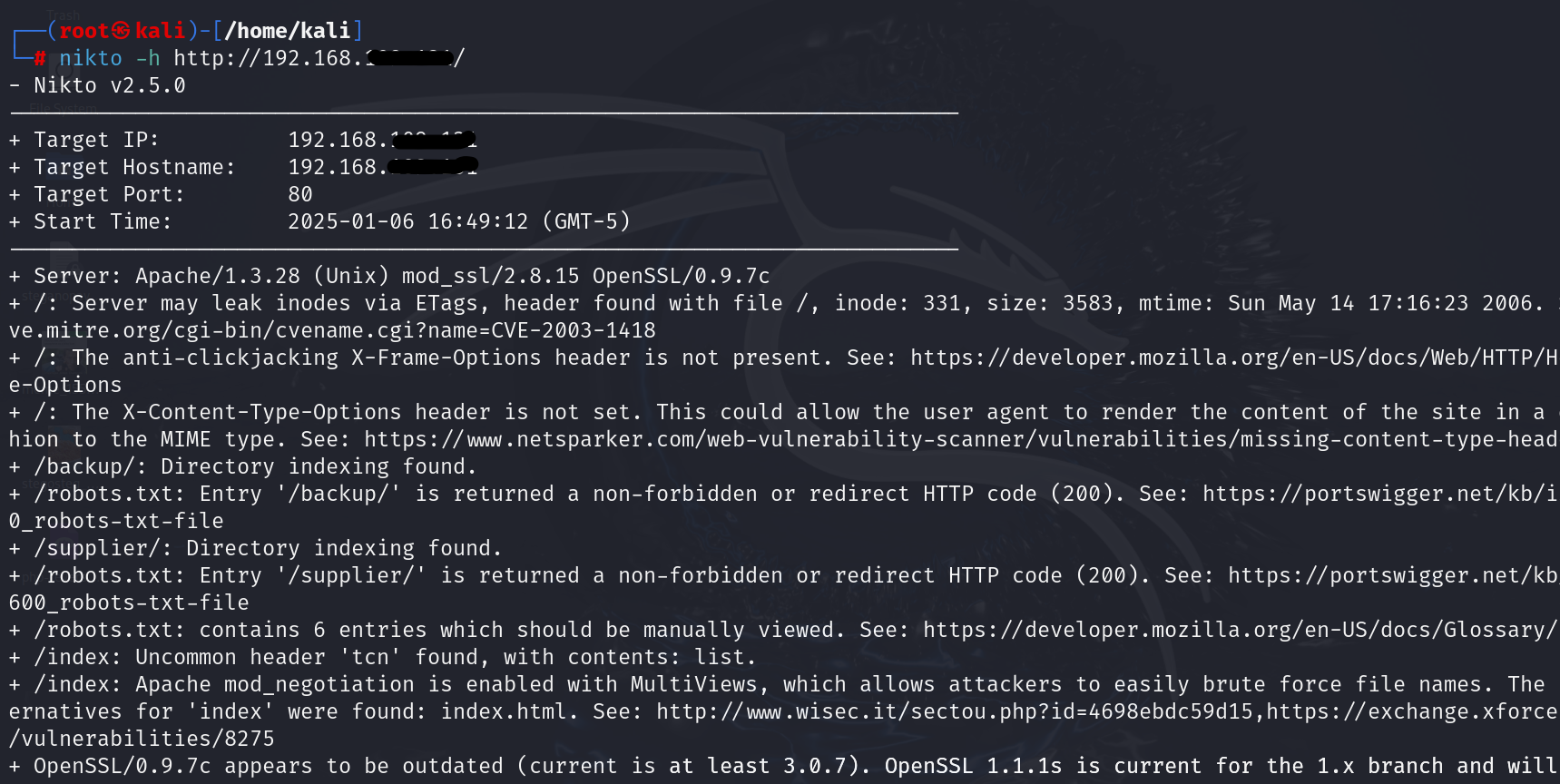
Basic Scan Command: The simplest command to scan a website is as follows:
| nikto -h <URL or IP address> |
Example
| nikto -h http://example.com |
This command initiates a basic scan, which will test the target for known vulnerabilities, misconfigurations, and outdated software.
Useful Parameters:
- -output: Saves the scan results to a file.
- -timeout: Sets a timeout for the scan.
- -ssl: Specifies SSL if the site doesn’t use HTTP.
- -C: Checks for HTTP-related vulnerabilities.
| nikto -h http://example.com -output example_scan.txt -timeout 10 -C all |

Scan for Specific Vulnerabilities: Nikto can target specific types of vulnerabilities by using the -Tuning option. The Tuning codes allow you to specify the scan focus.
- Scan for File Upload Vulnerabilities (Code 4)
| nikto -h -Tuning 4 |
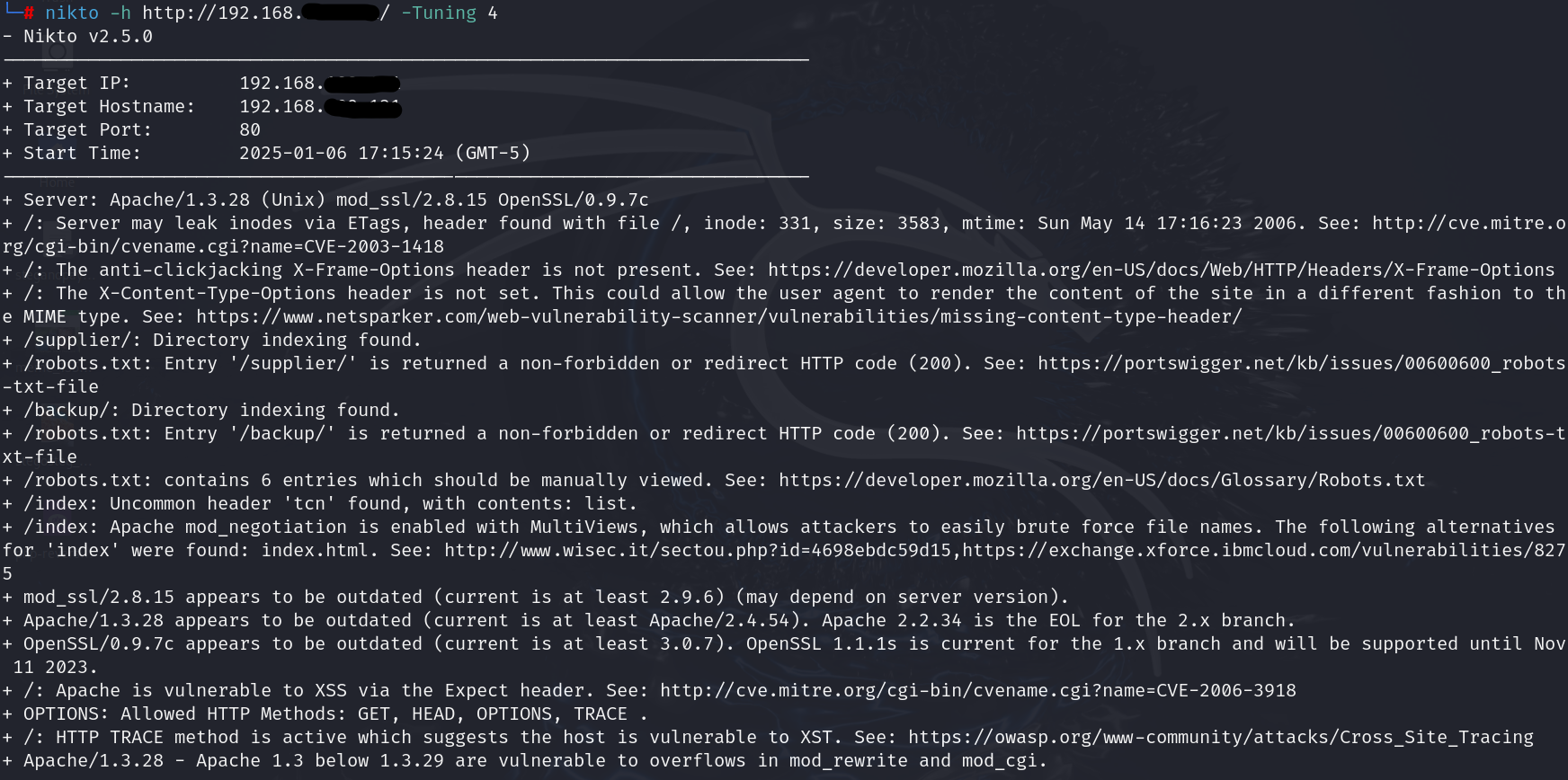
- Scan for Injection Vulnerabilities (Code 5)
| nikto -h -Tuning 5 |

Tuning codes reference
- 0: File upload
- 1: Interesting files / Seen in logs
- 2: Misconfiguration / Default files
- 3: Information disclosure
- 4: Injection (XSS/Script/HTML)
- 5: Remote file retrieval (shells)
Exporting Results to a Report: To export the results to a file, you can use the -o (output) option:
| nikto -h -o output.txt |


Advanced Scanning Options
Nikto also supports various advanced options for custom scans.
- Limiting Scan Scope: Use the -p option to specify a particular port (useful if the server runs multiple services):
| nikto -h -p 443 |

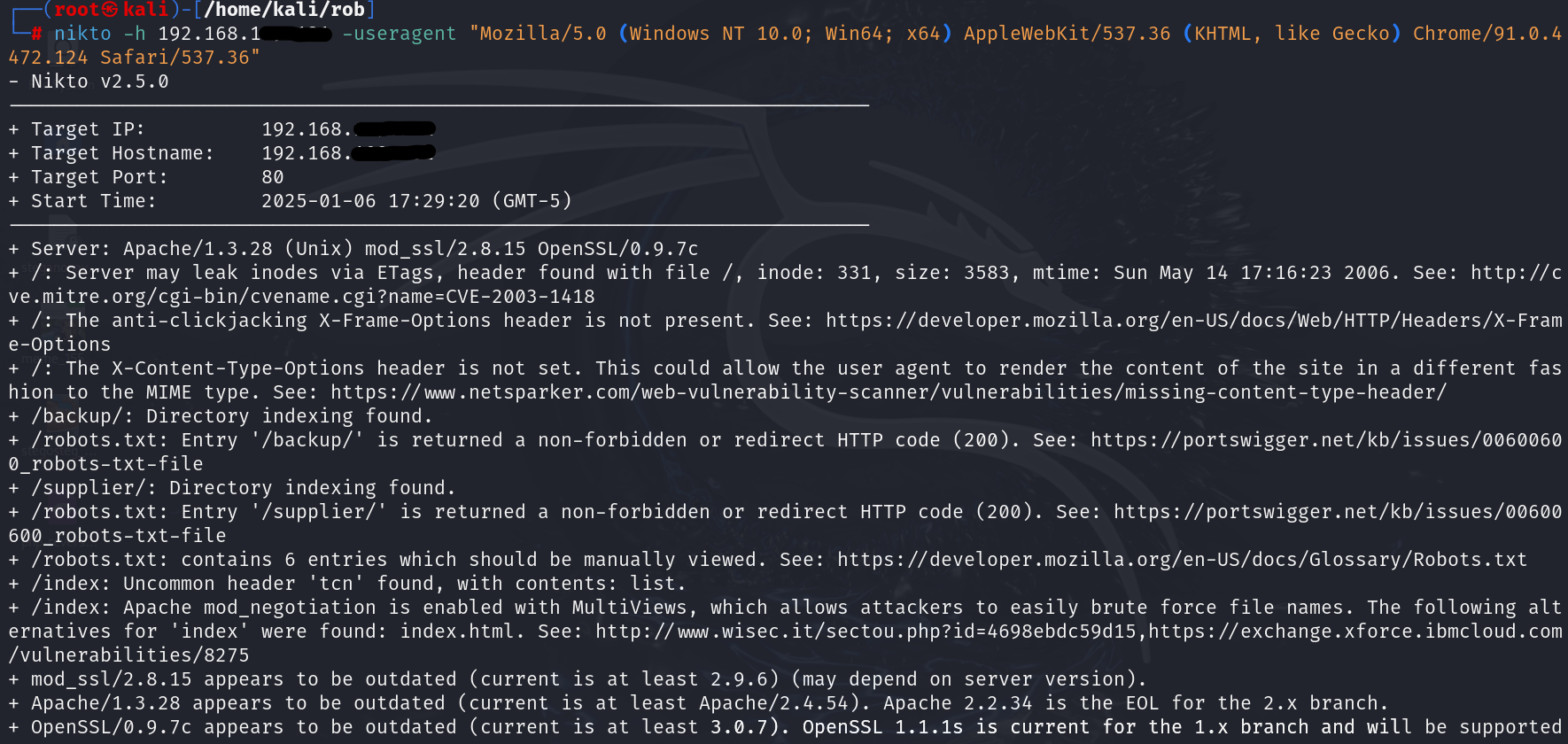
- Customizing the User-Agent: A great way to mimic legitimate browser traffic (Google Chrome browser on Windows 10) and avoid detection by simple monitoring tools.
| nikto -h -useragent “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36” |
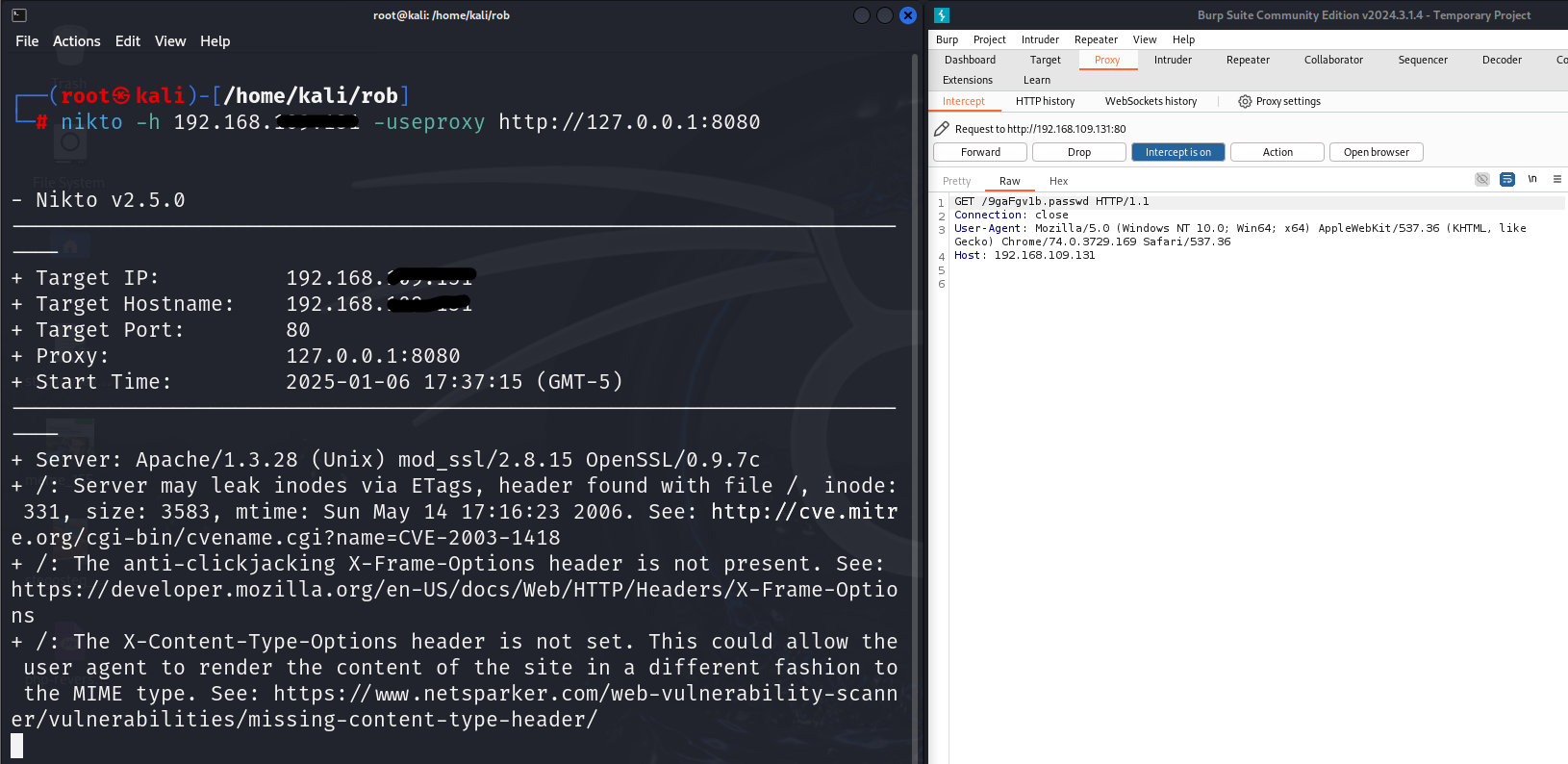
- Using Nikto with Burp Suite: You can proxy Nikto through Burp Suite for enhanced interception:
| nikto -h -useproxy http://127.0.0.1:8080 |
- Rate Limiting (Pause): The -Pause parameter adds a delay between requests during scans, minimizing server impact and reducing detection by IDS/IPS.
| nikto -h 192.168.xxx.xxx -Pause 3 |

-h 192.168.xxx.xxx: Specifies the target server’s IP address.
-Pause 3: Introduces a 3-second delay between each request sent during the scan.
Best Practices for Web Vulnerability Scanning with Nikto
- Schedule Regular Scans: Automate scans to ensure continuous monitoring.
- Avoid Scanning Critical Environments without Permission: Nikto is an intrusive tool that can generate a lot of traffic. Make sure you have authorization to avoid network disruptions or detection alerts.
- Use Scan Results to Guide Mitigation: Regularly update software, implement recommended security headers, and close access to exposed directories based on Nikto’s findings.
In Conclusion
Nikto is an excellent tool for identifying common vulnerabilities and misconfigurations in web applications. By understanding its features and limitations, you can incorporate it effectively into your cybersecurity toolkit.
Check out other related articles:
- Step-by-Step Guide for theHarvester Tool
- Steps for Effective DNS Footprinting
- The Ultimate Guide to SMTP and DNS Enumeration Practices
CEH v13 AI with InfosecTrain
Join InfosecTrain’s CEH v13 AI certification training to master tools like Nikto and other critical cybersecurity techniques. This hands-on course combines practical insights with real-world applications, empowering you to identify web vulnerabilities, strengthen security defenses, and tackle cyber threats effectively. Gain in-depth expertise, sharpen your ethical hacking skills, and become job-ready in the fast-evolving cybersecurity landscape. Take the next step in your career with InfosecTrain!
TRAINING CALENDAR of Upcoming Batches For CEH v13
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Jul-2025 | 31-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 16-Aug-2025 | 28-Sep-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |

 1800-843-7890 (India)
1800-843-7890 (India)