What are the Information Security Program Metrics?
Overview of Information Security Program Metrics
Information security program metrics are measurable indicators that are used to access, track, and enhance the efficiency of any organization’s information security program. These metrics provide valuable insights for management, security teams, or stakeholders to understand how well the organization’s strategies and security controls perform. These program metrics help to detect critical risk areas, allowing organizations to achieve several critical objectives that enhance their overall information security posture and align their security efforts with business goals.

Types of Information Security Metrics
Here are the different types of metrics for information security:
- Risk Management Metrics: Risk management metrics evaluate and manage the risk level across the organization. Common metrics include the number of identified vulnerabilities, the severity and likelihood of those vulnerabilities being exploited, risk exposure, and the effectiveness of controls in reducing residual risk.
- Operational Metrics: Operational metrics measure specific security operations performance, such as the time to detect and respond to security incidents.
- Compliance Metrics: Compliance metrics track the adherence to regulatory requirements, standards, and internal policies, such as the percentage of systems compliant with a specific standard (e.g., PCI-DSS).
- Qualitative Metrics: Qualitative metrics provide descriptive insights into information security factors that are not easily measurable. They often require subjective judgment and are useful for assessing security aspects that are difficult to measure numerically.
- Quantitative Metrics: Quantitative metrics provide measurable, numerical data to assess various information security factors objectively. They are useful for tracking performance over time and for comparing it to the industry standards.
Common Information Security Program Metrics
Here are some examples of effective security metrics:
- Mean Time to Detect (MTTD): The MTTD metric measures the mean time it takes to detect a security breach or incident after it happens.
Formulas:
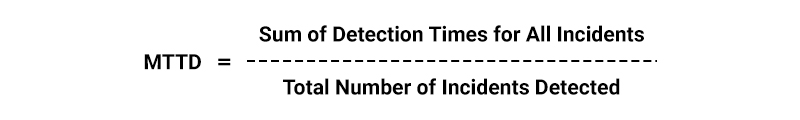
- Mean Time to Respond (MTTR): The MTTR metric measures the average time taken to respond to and reduce a security incident after detection.
Formulas:

- Patch Management Metrics: These metrics measure the percentage of systems patched within a specific timeframe or the time it takes to apply patches after they are released.
Formulas:

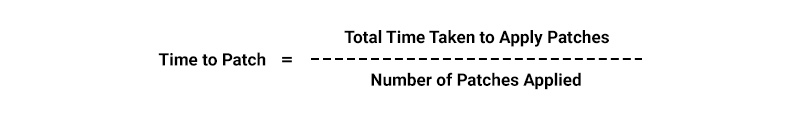
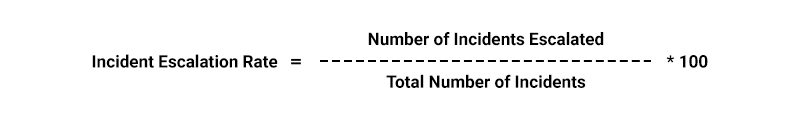
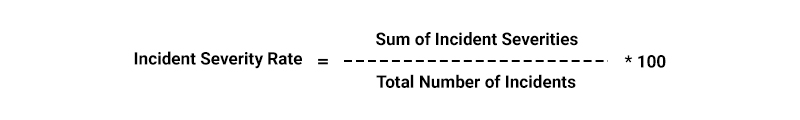
- Incident Response Metrics: These metrics assess the effectiveness of the incident response process, from incident detection to successful containment and escalation to higher management levels.
Formulas:
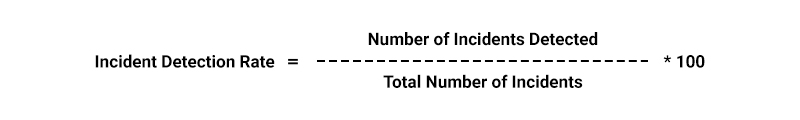
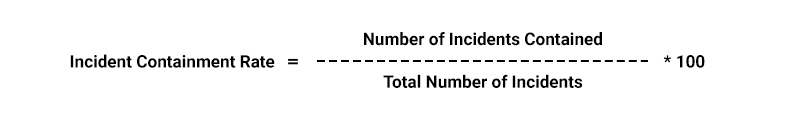
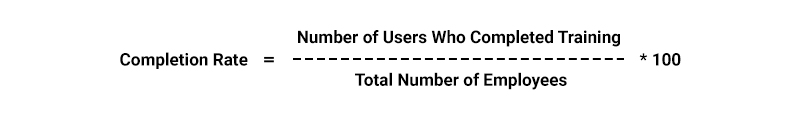
- Security Awareness Metrics: These metrics measure the percentage of users who have completed security training and the reduction in security incidents due to human error.
Formula:

- Vulnerability Management Metrics: These metrics assess the effectiveness of a vulnerability management program and ensure that security teams mitigate risks efficiently.
Formula:


- Security Incident Trends: These metrics track the number and types of incidents over time to identify patterns or emerging threats.
Formula:
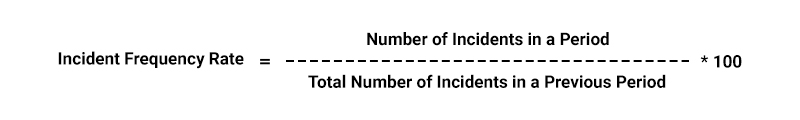
- Compliance Status: This metric measures the percentage of systems that are compliant with relevant standards and regulations, such as GDPR, HIPAA, or ISO 27001.
Formula:

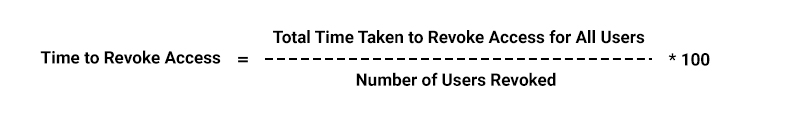
- Access Control Metrics: These metrics assess the effectiveness of access control measures and how quickly access is revoked when necessary for departing employees.
Formula:

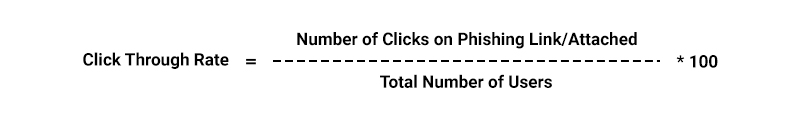
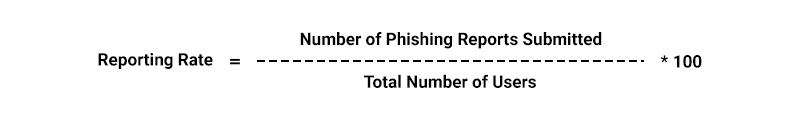
- Phishing Simulation Metrics: These metrics measure the effectiveness of phishing awareness training and programs by tracking user behavior during simulations.
Formula:

 Security Return on Investment (ROI): This metric calculates the financial return on investment in security measures by comparing the cost of security initiatives to the value of potential losses prevented.
Security Return on Investment (ROI): This metric calculates the financial return on investment in security measures by comparing the cost of security initiatives to the value of potential losses prevented.
Formula:

Benefits of Information Security Program (ISP) Metrics
- Visibility: ISP metrics provide precise and objective insights into the state of the security program.
- Accountability: ISP metrics help assign responsibilities and measure the effectiveness of individuals or teams in handling security tasks.
- Decision-Making: ISP metrics enable organizations to make informed decisions to strengthen their security controls, optimize resource allocation, and prioritize risk mitigation efforts.
- Continuous Improvement: ISP metrics facilitate the continuous analysis and improvement of the security program by detecting weaknesses as well as strengths.
- Communication: ISP metrics provide a way to communicate the security program’s effectiveness to stakeholders, including senior management and auditors.
Best Practices for Implementing Information Security Program (ISP) Metrics
- Align with Business Goals: Ensure metrics support the organization’s broader objectives and priorities.
- Keep It Simple: Focus on a manageable number of metrics that provide the most value.
- Ensure Accuracy: Use reliable data sources and regularly validate the accuracy of the metrics.
- Continuously Review: Regularly review and update metrics to reflect changes in the threat and business environment.
- Communicate Effectively: Present metrics in a way that is understandable and meaningful to all stakeholders.
Related Articles:
CISM Certification Training with InfosecTrain
Are you interested in learning more about these metrics? You can consider enrolling in InfosecTrain’s CISM certification training course. Led by experienced instructors, this course provides you with valuable insights into the information security program and its metrics. With practical insights and real-world scenarios, this course prepares you to tackle complex security challenges and aligns you with the CISM certification requirements, boosting your career in cybersecurity management.
TRAINING CALENDAR of Upcoming Batches For CISM
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 02-Aug-2025 | 24-Aug-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Close ] | |
| 13-Sep-2025 | 05-Oct-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] |







 1800-843-7890 (India)
1800-843-7890 (India)