What Is a Data Retention Policy?
As organizations generate and rely on more data than ever before, the real challenge lies in determining how long to keep it and when to securely dispose of it. Every piece of data has a lifecycle, including customer records, financial transactions, internal communications, and compliance documentation. That’s where a Data Retention Policy comes into play.
A Data Retention Policy is not just a set of guidelines; it serves as a roadmap for protecting sensitive information, maximizing storage, and promoting operational efficiency. Whether you are a business executive, IT professional, or cybersecurity enthusiast, understanding the principles of a DRP is crucial for risk management, cost reduction, and protecting sensitive data.
So, why should you take the time to learn about it? Because in an age where data breaches and compliance penalties are on the rise, knowing how to properly handle and dispose of data is not just a best practice but a necessity.
Introduction to Data Retention Policy (DRP)
A Data Retention Policy (DRP) is a formalized document that outlines an organization’s rules and procedures for storing and disposing of data. It ensures compliance with regulatory standards and supports operational requirements. It minimizes data security risks by maintaining control over how long data is retained, where it is stored, and how it is securely destroyed when no longer needed.
Importance of Data Retention Policy
- Regulatory Compliance: Ensure compliance with legal and industry-specific regulations such as GDPR, HIPAA, PCI DSS, and SOX, which mandate data retention timelines and proper disposal methods.
- Risk Mitigation: Mitigate the risk of data breaches and unauthorized access by securely managing sensitive information and limiting retention to what is necessary.
- Cost Management: Optimize storage resources by permanently deleting data, thus lowering storage costs and improving operational efficiency.
- Business Continuity: Facilitate data recovery and business continuity by identifying which data must be retained for critical operations.
- Litigation Readiness: Retain relevant records to support potential legal proceedings or audits, reducing exposure to penalties or legal risks.
Key Components of a Data Retention Policy
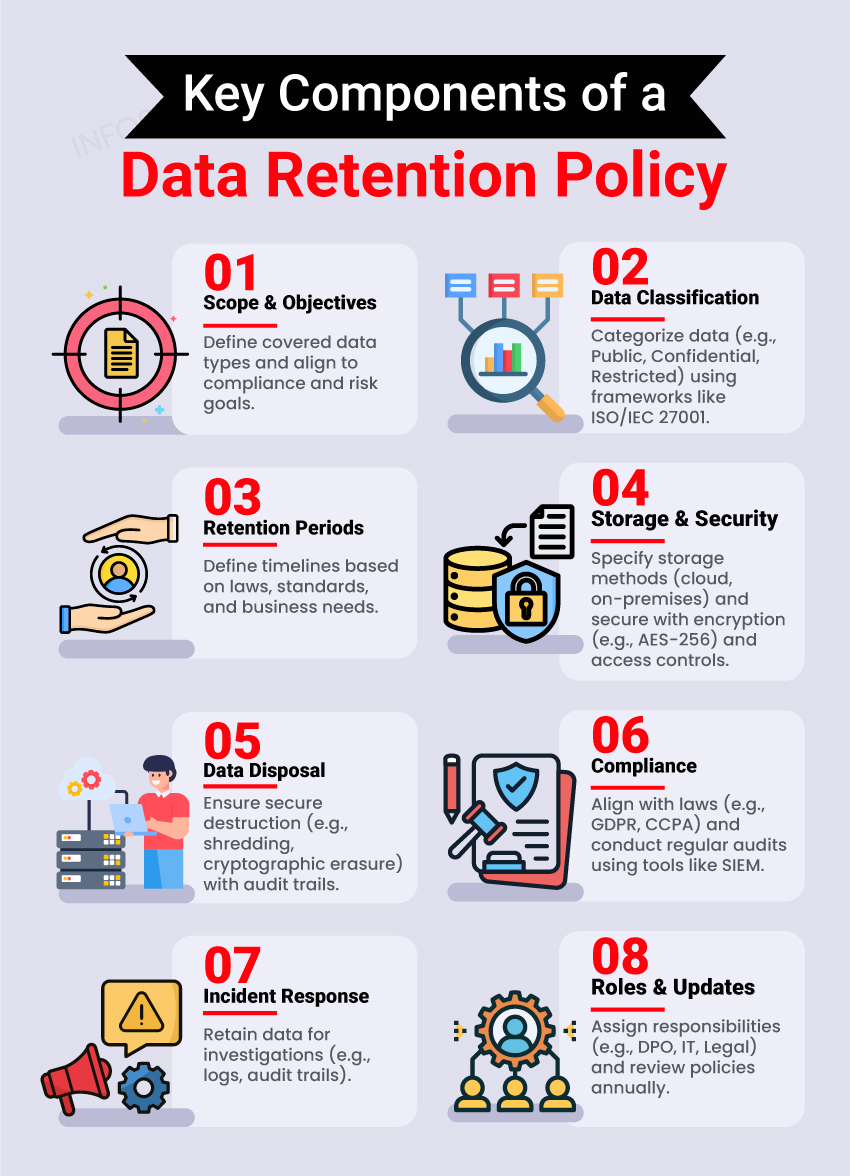
1. Scope and Objectives
- Define the scope of the policy, including the types of data it covers (e.g., personal data, financial records, intellectual property).
- State the purpose of the policy, linking it to compliance, operational needs, and risk management.
2. Data Classification
- Categorize data according to its sensitivity level and applicable regulatory requirements, for example:
- Public: Marketing material, press releases.
- Confidential: Employee records, customer PII.
- Restricted: Trade secrets, encryption keys.
- Use frameworks like ISO/IEC 27001 or NIST for consistent classification.
3. Retention Periods
- Specify retention timelines for each data category, referencing applicable laws, industry standards, and business needs.
4. Data Storage and Security Controls
- Specify where and how data will be stored (e.g., on-premises, cloud, hybrid environments).
- Include security measures:
- Encryption (e.g., AES-256 for sensitive data).
- Access controls (e.g., role-based or attribute-based).
5. Data Disposal Procedures
- Detailed secure disposal practices to ensure complete data destruction:
- Digital Data: Overwriting (NIST SP 800-88), degaussing, cryptographic erasure.
- Physical Data: Shredding, incineration.
- Maintain an audit trail for disposal processes.
6. Compliance and Audit
- Schedule periodic audits to verify adherence to the policy.
- Use tools like SIEM (Security Information and Event Management) for log retention and monitoring.
7. Legal and Regulatory Alignment
- Refer to applicable laws, such as:
- GDPR: Right to erasure and time-bound retention.
- CCPA: Consumer rights to access and delete data.
- SOX: Financial record retention mandates.
- Include guidelines for cross-border data transfers, ensuring compliance with data sovereignty laws.
8. Incident Response Integration
- Include data retention needed for incident investigations, such as logs or audit trails, to support cybersecurity forensics.
- Define retention periods for these specific data types.
9. Stakeholder Roles and Responsibilities
- Assign ownership for policy implementation and monitoring to:
- Data Protection Officer (DPO): Oversees compliance and policy adherence.
- IT Security Team: Implements technical measures for secure storage and deletion.
- Legal Team: Ensures alignment with regulatory frameworks.
- Engage cross-functional teams such as legal, HR, and IT to ensure holistic coverage.
10. Policy Review and Updates
- Schedule periodic reviews (e.g., annually) to adapt to evolving regulations and organizational changes.
- Document changes to ensure traceability.
Data Retention Policy Best Practices
1. Automation: Use data lifecycle management tools to automate data retention and deletion.
2. Data Minimization: Avoid unnecessary data collection to reduce retention complexity and compliance risks.
3. Regular Audits: Perform audits to ensure policy adherence and identify vulnerabilities.
4. Incident Preparedness: Integrate the policy with the organization’s incident response plan for effective forensic investigations.
5. Employee Training: Conduct training sessions for employees to understand the importance of the policy and their responsibilities.
How Can InfosecTrain Help?
A robust Data Retention Policy is not just a compliance requirement but a strategic component of effective data governance and cybersecurity. By implementing a DRP, organizations can reduce risks, optimize operations, and uphold trust with stakeholders.
At InfosecTrain, we offer expert-led training for certifications like CCSP, CISSP, CompTIA DataSys+, and CSSLP, focusing on critical topics like Data Retention and Data Retention Policy. With real-world scenarios, interactive sessions, and exam-focused guidance, InfosecTrain equips professionals to master compliance, data lifecycle management, and secure storage practices, ensuring both certification success and enhanced cybersecurity skills.
TRAINING CALENDAR of Upcoming Batches For CCSP
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 24-May-2025 | 06-Jul-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 21-Jun-2025 | 03-Aug-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] | |
| 26-Jul-2025 | 31-Aug-2025 | 19:00 - 23:00 IST | Weekend | Online | [ Open ] | |
| 30-Aug-2025 | 12-Oct-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)