What is Digital Forensics and Incident Response (DFIR)?
Imagine being able to detect a cyber threat before it inflicts significant damage, respond quickly to mitigate damage, and gain valuable insights to prevent future attacks. This is precisely what Digital Forensics and Incident Response (DFIR) offers. DFIR not only helps organizations respond to cyber incidents but also enhances their overall security posture. With DFIR, organizations can safeguard their systems’ integrity, secure sensitive information, and maintain customer trust.

“An effective cybersecurity strategy is incomplete without a robust DFIR (Digital Forensics and Incident Response) plan,” says cybersecurity expert Jane Doe.
What is DFIR in Cybersecurity?
In the early days of cybersecurity, responding to a breach was often a chaotic and reactive process. However, the evolution of DFIR (Digital Forensics and Incident Response) has transformed how organizations handle cyber threats. DFIR is a critical discipline within cybersecurity, focusing on identifying, analyzing, and responding to cyber threats. As cyber-attacks become increasingly sophisticated, the role of DFIR in safeguarding digital assets has never been more important.
DFIR involves two main components:
1. Digital Forensics: This is the process of collecting, analyzing, preserving, and presenting digital evidence from devices. It involves examining data from computers, mobile devices, networks, and other digital storage media to uncover details about cybercrimes or security breaches. The primary goal is to reconstruct events, recover deleted files, and interpret data to support legal proceedings or internal investigations. It provides critical insights into how breaches occurred and helps in identifying the perpetrators and methods used.
Digital Forensics Process
This process involves systematic steps to collect, preserve, analyze, and present digital evidence:
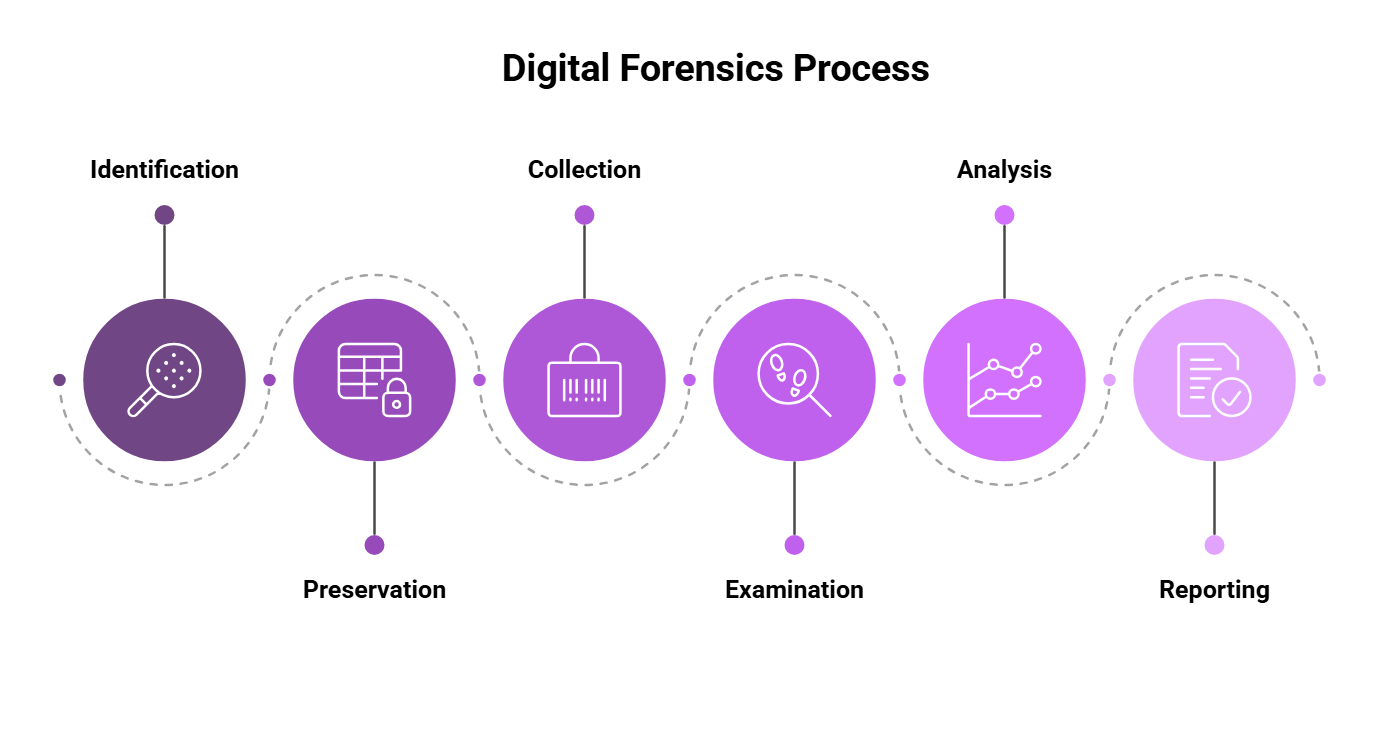
1. Identification
- Define the scope and locate potential sources of digital evidence, such as computers and network logs.
2. Preservation
- Ensure the integrity of evidence using forensically sound methods.
- Create forensic copies and maintain a clear chain of custody.
3. Collection
- Gather evidence from identified sources using appropriate tools.
- Log details about the collected evidence.
4. Examination
- Use forensic software to analyze data for relevant information.
- Identify and extract digital artifacts and recover deleted files.
5. Analysis
- Correlate data to build a timeline of events.
- Interpret data to understand actions and methods used by potential attackers.
6. Reporting
- Document findings and prepare evidence for presentation.
- Review and revise reports for accuracy.
2. Incident Response: This is the structured approach to detecting, managing, and mitigating the impact of cybersecurity incidents. It involves quickly detecting security breaches, containing the threat to prevent further damage, eradicating the root cause, and recovering affected systems. Effective incident response aims to minimize disruption, reduce recovery time and costs, and enhance the overall security posture of an organization.
Incident Response Process
This process involves several key steps to help organizations quickly address security breaches, minimize damage, and restore normal operations:

1. Preparation
- Establish an incident response plan.
- Set up a dedicated incident response team.
- Ensure proper tools and resources are in place.
2. Identification
- Detect potential security incidents through monitoring and alerts.
- Verify and prioritize incidents based on severity.
3. Containment
- Isolate affected systems immediately.
- Develop a comprehensive containment strategy.
4. Eradication
- Identify the root cause of the incident.
- Remove malicious elements from the affected systems.
- Apply patches and updates to prevent recurrence.
5. Recovery
- Restore affected systems and data from clean backups.
- Monitor systems for any signs of residual threats.
- Validate the integrity of restored systems.
6. Lessons Learned
- Conduct a thorough post-incident review.
- Document findings and update the incident response plan.
- Provide training and awareness programs to prevent future incidents.
Importance of DFIR in Cybersecurity
When a cyber attack happens, the first step is to recover from it. However, recovery alone is not sufficient. To fully eliminate the threat and prevent it from recurring, it is crucial to understand the specifics of the attack and the attackers. DFIR (Digital Forensics and Incident Response) plays a key role here by conducting a detailed forensic analysis. DFIR experts perform detailed forensic analysis, collecting and examining extensive data to identify an attacker’s identities, entry methods, and actions within the compromised systems. This process helps detect any data loss or specific damage caused by the breach, ensuring thorough threat elimination and strengthening future security measures.
Benefits of DFIR
Combining these two disciplines into DFIR offers several benefits:
- Threat Mitigation and Evidence Preservation: DFIR teams are trained to collect and preserve digital evidence while actively containing and eradicating threats. This ensures that valuable evidence is not lost or tampered with during incident response efforts.
- Enhanced Threat Prevention and Detection: DFIR teams leverage detailed forensic investigations to improve threat detection and prevention strategies. This approach helps organizations create more effective incident response plans and streamline threat-hunting activities.
- Comprehensive Post-Incident Analysis: By integrating digital forensics with incident response, DFIR teams can conduct thorough investigations to understand the attack scope, identify root causes, and develop strategies to prevent future incidents.
- Faster and More Robust Recovery: DFIR investigations often uncover hidden malware or system damage that might be overlooked in traditional incident response processes, leading to more thorough threat eradication and system recovery.
- Support for Legal and Regulatory Requirements: The adherence to a strict chain of custody in DFIR processes ensures that the collected evidence can be used in legal proceedings, regulatory audits, and insurance claims, providing robust support for prosecuting cybercriminals.
Advanced Cyber Threat Hunting and DFIR Training with InfosecTrain
Enroll in InfosecTrain‘s Advanced Cyber Threat Hunting and DFIR Training course to gain comprehensive knowledge and hands-on experience in detecting and addressing cyber threats. This course covers some very important topics such as digital forensics, incident response methodologies, threat hunting techniques, and advanced analysis tools. Taught by industry experts, the training equips individuals with the skills needed to protect organizations from sophisticated cyber-attacks and enhance their overall cybersecurity posture. Prepare for a successful career in cybersecurity with InfosecTrain.

 1800-843-7890 (India)
1800-843-7890 (India)