What is Information Security Lifecycle Management?
Security professionals can use a lifecycle model throughout their daily work lives, similar to most IT industries. As a security expert, using a lifecycle model gives direction and ensures that improvements are being made to the enterprise’s security posture. Security programs are something you can only set up and remember about. They must be taken care of and improved regularly because new security risks and threats are constantly emerging. This means regularly checking for security risks, training employees, testing and evaluating the program, and keeping software and systems up to date. Ongoing care, maintenance, and improvement are essential to keeping your security program strong and effective.
What is Information Security Lifecycle?
Information security is locating, managing, and safeguarding confidential company data using various online and offline procedures and tools. So, the information security lifecycle is the process of protecting sensitive business information through several steps or activities from being misused or stolen by unauthorized sources. Protecting confidential business information from falling into the wrong hands is done through the information security lifecycle process. It might be digital or printed on paper, or it might be in another format entirely.
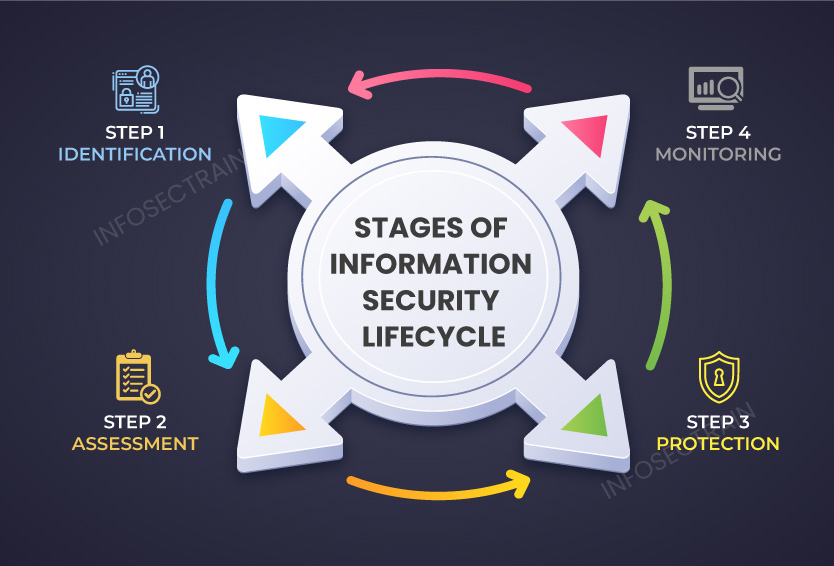
Step 1: Identification-
The identification of various kinds of data and information that need to be secured is the first step in the lifecycle of an information security process. After all, you can only protect data or information if you know how sensitive or confidential the information is that you’re handling. Starting at a high level, this identification stage should work down to a more detailed level. You must recognize and comprehend the available resources and the assets you need to safeguard to establish an appropriate security posture.
Step 2: Assessment-
The information security lifecycle’s assessment phase aims to build on the knowledge gathered in the preceding step. Once each one of your assets has been properly located and listed, the next step is to evaluate their security thoroughly. This stage includes every assessment aspect, from examining your current practices to running vulnerability scans, and it involves system, server, and vulnerability assessments.
- System Assessment-
System Assessment-System assessment entails a comprehensive examination of the system or ICT infrastructure. It involves examining:- Types of Software
- Malware and security alerts
- Protective measures
- Incompatible software versions
- Additional details to find vulnerabilities
- Server Assessment-
A server assessment entails thoroughly examining the server to gather the necessary information and examine its configurations, such as the RAM size, the operating system, license, and hard disc. The IT team examines configurations, User IDs, login protocols, password security, and remote access. - Vulnerability Assessment-
Finding vulnerabilities comes after a thorough examination of the server and the system. The focus of attention is the area that contains sensitive data and is most vulnerable to attacks.
Step 3: Protection-
It’s crucial to safeguard your network by bringing systems up to date with your previously established policy and standards after assessing your network and obtaining more detailed information about it. It’s time to secure your systems at this point. Since the actual goal of this step is to mitigate every risk identified during the assessment period, this phase in the information security lifecycle is occasionally referred to as the “mitigation” step. Configuring and supporting every device and network component you have should be the main focus of this phase. Your infrastructure and systems should become more robust due to this step, aligning them with the company’s guidelines before the lifecycle starts.
Step 4: Monitoring-
Monitoring the security already in place and the recently modified and updated security is the final stage of the information security lifecycle. It’s crucial to make sure your security posture continues to improve once you’ve, in your mind, confirmed it overall. Monitoring new systems that are integrated into the overall structure of your company’s network is just as crucial as monitoring changes you’ve made. Because servers and computer systems are updated frequently, a process that checks on security across the enterprise must be implemented.
About InfosecTrain
InfosecTrain is a company that provides training and consulting services in cybersecurity. Their certified instructors have years of experience in the industry, and they offer courses that can help you pass certification exams. They provide various services, including cybersecurity consulting and various certification courses. If you want to get certified in CompTIA CySA+, they have a training course to help you prepare. They strive to simplify the enrollment process for you, so you can quickly research and enroll in the course that best suits your needs. Overall, InfosecTrain is a reliable source for all your IT and cybersecurity training needs.







 1800-843-7890 (India)
1800-843-7890 (India)