What is ‘Ransomware’ and how does it work?
What is ‘Ransomware’ and how does it work?
With advances in technology, it has become a big battle to keep our environment safe. There are new kinds of threats being created everyday which aim to target servers and network systems. The managers need to be prepared against these threats, using support tools such as:
Firewalls, IPS (Intrusion Prevention systems), IDS(Intrusion detection systems), WAF, Proxy and SIEM. Currently, one of the most dangerous and time consuming malware is ‘ransomware’.
What is ‘ransomware’? How does it work? How does it infect an environment? Let us see…
Ransomware is a malware that can block a device or encrypt the content. The hacker then demands a ransom to get his data back. Normally the attackers promise to restore the access or the data of the infected machines.
You can also define ransomware as a type of software that restricts access to an infected system and charges a redemption price for that access to be restored. If the redemption price is not paid, the files would be lost or published.

According to a technician, ransomware is also called as a type of cryptography. Let us see why:
‘Cryptography’, is the ability to secure communications in the presence of third parties, called adversaries. The cryptography term came from the fusion of the words “Kryptós” and “gráphein”, which means “hidden” and “to write”. It is a conjunction of rules that encrypts the original message and sends it to the receiver. The receiver then decrypts it to view it. Encryption is the key element of cryptoransomware, as your entire business plan depends on the successful use of cryptography to block files or file systems of victims without recovery plans, such as data backups. This does not mean that cryptography is intrinsically malicious.
The ransomware attack is around for long time. Attackers use several known distribution methods. Malware are often spread through phishing schemes involving malicious links, email attachments, or downloaded files that are installed on the server from compromised sites. In spite of knowing the risks, one in four recipients opens phishing messages and, surprisingly, one in 10 clicks on attachments received in those messages.
Anatomy of a ransomware attack:
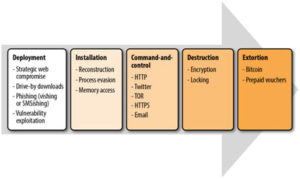 Credit of image: Ransomware by Timothy Gallo, Allan Liska
Credit of image: Ransomware by Timothy Gallo, Allan Liska
The first know virus that encrypted user files was Dirty Decrypt, after it came CryptoLocker, PowerLocker, Citroni, CryptoWall, CryptoWall 2, CryptoWall 3, Torrent Locker, Cryptographic Locker others. Every day a new kind is emerging that aims to hamper the services of the security tools.
Below some the 10 cases famous of attack of ransomware in 2017:
10 – UNKNOWN
https://goo.gl/oBLsL1
9 – REYPTSON
https://goo.gl/PWmQfo
8 – LEAKERLOCKER
https://goo.gl/h6XWda
7 – WYSIWYE
https://goo.gl/iGyYmk
6 – OSIRIS
https://goo.gl/BQMBpu
5 – CERBER
https://goo.gl/kxBGtu
4 – LOCKY
https://goo.gl/XzMYft
3 – BADRABBIT
https://goo.gl/Hw21gG
2 – NOTPETYA
https://goo.gl/A8US7f
1 – WANNACRY
https://goo.gl/oHpNx2
It is good to follow these tips to secure yourself from these threats:
- Keep all of your software including operating systems patched and up-to-date. This
can prevent the hacker from attempting to exploit any known vulnerabilities. - Backup your data on a regular basis and keep at least one full backup offline or
outside the company environment. - Reduce the attack surface by disabling or uninstalling any unneeded services and
software - Restrict or ban the use of Remote Desktop Protocol (RDP) from outside the network
or allow Network Level Authentication - Secure your backups with dual or multiple authentication
- Regularly train your team to recognize and deal with phishing attacks






 1800-843-7890 (India)
1800-843-7890 (India)