What is SSDLC (Secure Software Development Lifecycle)?
As the rate of cybercrimes continues to increase, cyberattacks are becoming increasingly complex in how they take advantage of vulnerabilities. In the age of cyberattacks, it has been observed that hackers, cybercriminals, and other malicious users are continuously looking for vulnerabilities in software systems to gain access to their target systems. Cyberattacks affect everyone, from individuals to organizations, due to insecure software designs and implementations that do not adequately safeguard systems. Compromising software can have a catastrophic effect on the organization, resulting in financial losses and a damaged reputation, and because of this, ensuring software security during development should be a top priority nowadays.
So in this article, we will provide you an overview of how to implement security into the Software Development process.
What is Secure Software Development?
Secure Software Development is a process for developing secure software that integrates security into each stage of the Software Development Life Cycle (SDLC), such as in requirements, design, deployment, testing, and maintenance. The security is incorporated into every stage of the SDLC from the very beginning rather than being fixed after identifying significant product flaws. During the software development process, it performs continuous security checks. These checks are carried out before a single line of code has been written and identify and mitigate vulnerabilities during the very early stages of the software development process.
Advantages of Secure Software Development
There are several advantages to optimizing software security; by implementing it, you will protect your organization from reputation loss, financial risk, and legal penalties. Here are some of the advantages:
- Helps to identify critical issues at an early stage
- Minimizes business risks
- Enhances the overall functionality of the software
- Reduces the number of vulnerabilities present in software that has been released
- Reduces potential issues for a business
- Improves safety and security procedures inside the organization
- Lowers the cost of identifying and fixing software vulnerabilities
- Consistent adherence to security-related laws and regulations and financial savings from penalties
Stages of Secure Software Development Lifecycle
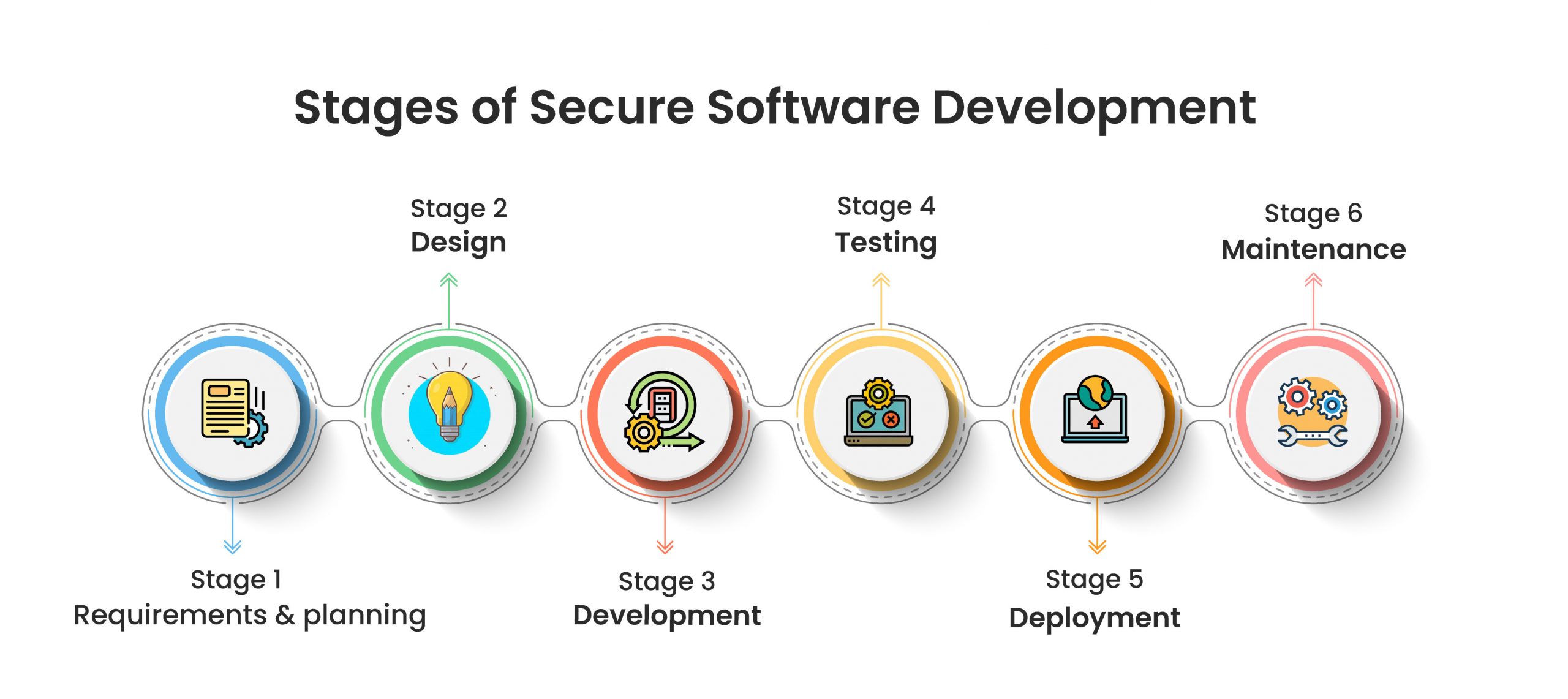
1. Requirements gathering and planning : The first stage of the Secure SDLC is to precisely define the software’s application security requirements and compliance goals. During this stage, you will develop a software plan, write down software security requirements, select a secure SDL methodology, and assign human resources with expert knowledge and application security abilities. During this phase, the security requirements help in rapidly detecting and resolving any potential vulnerabilities or bugs that have been found.
2. Design: Secure Design is also referred to as Threat Modeling. It comes into action after you’ve completed the first stage. In this stage, you can start designing secure software; software should be designed in accordance with the requirements analysis and planning. During this stage, you can implement and code the security requirements in compliance with the secure coding standards. In which you can identify potentially malicious activities, incorporate necessary countermeasures inside software architecture, and select third-party components that help speed up development.
3. Development: Following the software design stage, the actual development of the software design is now beginning. In this stage, the design is turned into well-written secure code. After the coding has been written, the code review process is initiated, which is necessary for secure coding. This stage includes the Static Application Scanning Tool (SAST) that analyzes newly created code to identify potential vulnerabilities without executing the application. The development process delivers the best outcomes using secure coding standards and effectively implements safe design patterns and frameworks.
4. Testing: After the software development, you can now conduct automatic and manual software testing using a wide range of technologies and find and fix application errors in this stage. In this stage, you can perform a more in-depth analysis of the application’s security using more comprehensive security scanning tools and technologies such as Static Application Security Testing (SAST), also known as code review and Dynamic Application Security Testing (DAST). There are many other ways to conduct security testing, including penetration testing and fuzz testing by Certified Ethical Hackers (C|EH) or Penetration Testers.
5. Deployment: In this stage, the software is prepared to be formally deployed into the real world once it has completed quality assurance and testing. But, before being used in the real-world environment, the software may be installed in a specific primary market sector. This will allow the developers to determine whether or not the software’s design suits the circumstances.
6. Maintenance: The deployment of software does not mark the end of your responsibilities. In fact, deployed software needs to be maintained regularly because, even after extremely extensive testing procedures have been performed, newly released vulnerabilities may still affect your software. Because of this, you should continue working on the software’s security once it has been released, and you will need to conduct continuous security checks and implement an incident response plan into action.
Feel free to check out related articles:
- Secure Software Development Concepts and Methodologies
- What is Data Classification and Its Components?
- What is the Principle of Least Privilege?
How Can InfosecTrain Help?
Advanced security is necessary to safeguard today’s sophisticated technology against software vulnerabilities that lead to malfunctions and breakdowns. The six stages of the Secure Software Development Lifecycle can assist you and your company in developing a perfect software solution.
Enroll in InfosecTrain’s Certified Secure Software Lifecycle Professional (CSSLP) certification training course if you want to build your career in secure software development. The CSSLP certification is intended for software and security professionals who wish to apply best practices to each stage of the Software Development Lifecycle (SDLC). This certification verifies that you have the required skills and abilities to design, develop, and execute security practices throughout each stage of the SDLC.


 1800-843-7890 (India)
1800-843-7890 (India)