Cyber Security Orientation Program (Foundation Level) Online Training
40 hrs
Live Sessions
40 hrs
Live Sessions
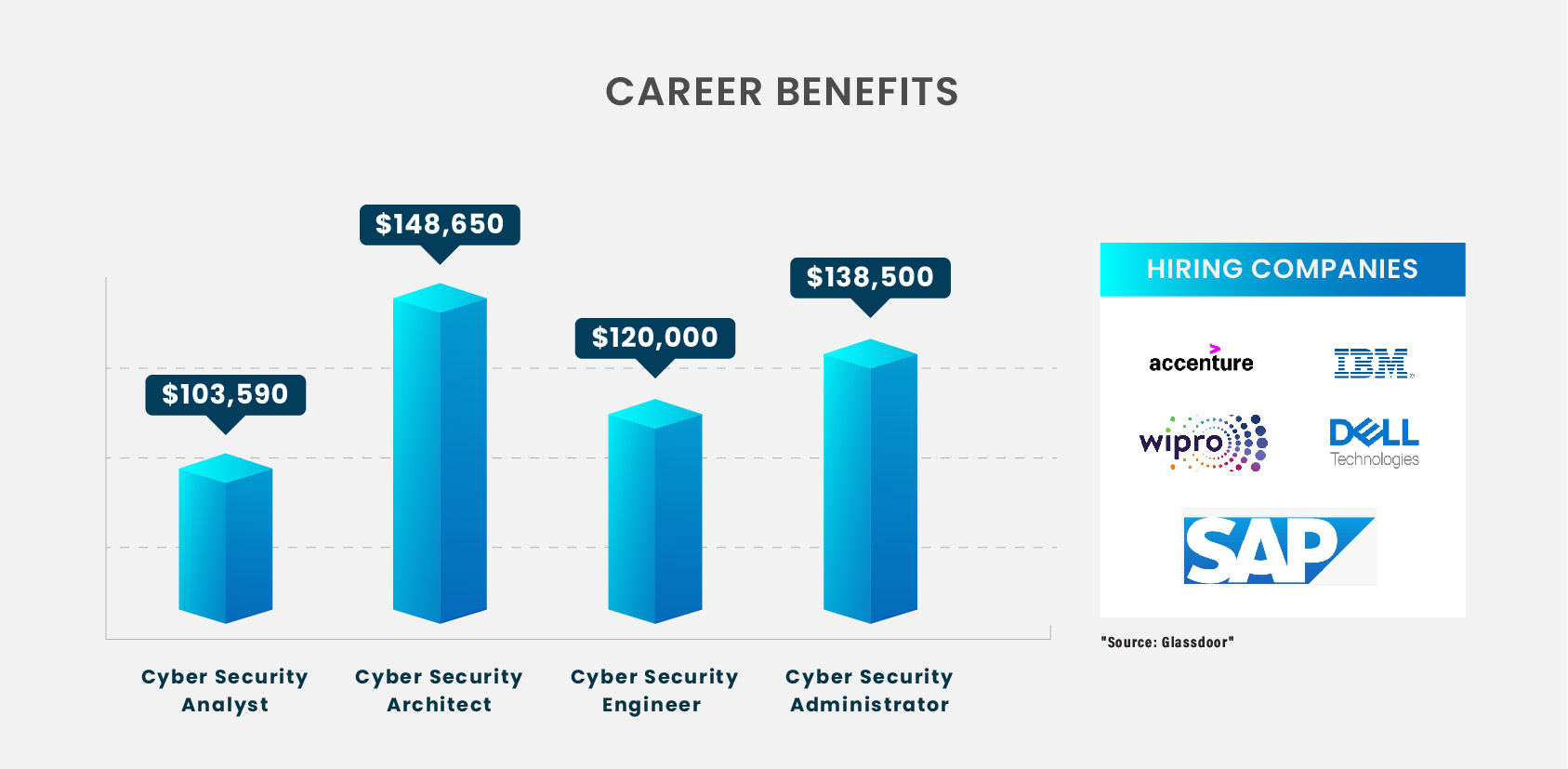
The Cyber Security Orientation Program is a full course designed for beginners in the cyber security field. It will consist of four different subjects, that are:
InfosecTrain is a proficient technology and security training and consulting organization across the globe, specializing in various IT security courses and services. Our CSOP training aims to develop advanced skills required in the domain of Cyber Security. You can leverage the following benefits with InfosecTrain:
There is no such prerequisite for this course but having an IT background will help you gain the concepts faster.
LEVEL 1: CompTIA A+
Hardware Fundamentals
Operating System Fundamentals
Networking and Security Fundamentals
Safety and Operational Procedures
Working with Other Operating Systems
LEVEL 2: Introduction to Networks
Introduction to Networks
The Open Systems Interconnection Specifications
Networking Devices
IP Adressing
WAN Infrastructure
Troubleshooting Network Issues
LEVEL 3: Linux Fundamentals
Exploring Linux Command-Line Tools
Managing Files
Administering the System
Writing Scripts, Configuring E-mail, and Using Databases
LEVEL 4: Security & Cloud Essentials
Understanding Threat Actors & Threat Intelligence
Understanding Security Assessments
Social Engineering and Malware
Understanding Authentication Controls
Understanding Identity and Account Management Controls
Understanding Physical Security
Cloud Essentials
Cloud Management

10+ years of experience as an Information Security Consultant and Trainer in delivering training to government and non-government organizations around the globe on different Information security verticals.
10+ Years Of Experience

10+ years of experience as an Information Security Consultant and Trainer in delivering training to government and non-government organizations around the globe on different Information security verticals.
10+ Years Of Experience

10+ years of experience as an Information Security Consultant and Trainer in delivering training to government and non-government organizations around the globe on different Information security verticals.
10+ Years Of Experience

10+ years of experience as an Information Security Consultant and Trainer in delivering training to government and non-government organizations around the globe on different Information security verticals.
10+ Years Of Experience

10+ years of experience as an Information Security Consultant and Trainer in delivering training to government and non-government organizations around the globe on different Information security verticals.
10+ Years Of Experience

Customized schedule
Learn at your dedicated hour
Instant clarification of doubt
Guaranteed to run

Flexibility, Convenience & Time Saving
More Effective
Learning Cost Savings

Anytime, Anywhere – Across The Globe
Hire A Trainer
At Your Own Pace
Customized Corporate Training




 Thoroughly enjoyed the course and the continuous support from the entire team..
Thoroughly enjoyed the course and the continuous support from the entire team..


 It was a good experience. Looking forward to career growth with Infosectrain. Thank you
It was a good experience. Looking forward to career growth with Infosectrain. Thank you


 Really interesting courses are delivered by really knowledgeable instructors. Worth the fees
Really interesting courses are delivered by really knowledgeable instructors. Worth the fees


 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.


 I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.
I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.


 I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.
I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.


 Thoroughly enjoyed the course and the continuous support from the entire team..
Thoroughly enjoyed the course and the continuous support from the entire team..


 It was a good experience. Looking forward to career growth with Infosectrain. Thank you
It was a good experience. Looking forward to career growth with Infosectrain. Thank you


 Really interesting courses are delivered by really knowledgeable instructors. Worth the fees
Really interesting courses are delivered by really knowledgeable instructors. Worth the fees


 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.


 I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.
I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.


 I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.
I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.
 Certified & Experienced Instructors
Certified & Experienced Instructors
 Post Training Support
Post Training Support
 Customized Training
Customized Training
 Flexible Schedule
Flexible Schedule
 Access to Recorded Sessions
Access to Recorded Sessions
The cloud security protections measures provide user and device authentication, data and resource access management, and data privacy protection. They also help with regulatory adherence. Because most businesses are currently adopting cloud computing in some way or another, cloud security is crucial.
In both the commercial and governmental sectors, the network is regarded as one of the most important resources in a company. Networks are built to help people achieve a goal or meet a need. Because these goals and requirements are usually vital, the network is also crucial.
To communicate with one another, computers require networking devices. Routers, hubs, switches, and bridges are all networking devices that may perform a variety of functions.
Cloud computing is a methodology for providing on-demand network access to a shared pool of programmable computing resources that can be quickly supplied and released with minimum administration effort and service provider contact.