Pentester Combo Training & Certification Course
InfosecTrain offers Online Pentest Tester Combo Training & Certification Course to prepare for Certified Ethical Hacker (CEH),Advanced Penetration Testing . Know More
InfosecTrain offers Online Pentest Tester Combo Training & Certification Course to prepare for Certified Ethical Hacker (CEH),Advanced Penetration Testing . Know More
The EC-Council Certified Ethical Hacker is one of the most highly regarded security certifications in the world. The course will teach you about the most recent commercial hacking tools, practices, and methodologies used by real-world hackers. This course also improves your awareness of key security concepts and confirms your ability to spot vulnerabilities in an organization’s network architecture, allowing you to successfully battle cyber-attacks.
Advanced Penetration Testing is an important aspect of the security structure so, our course includes everything you’ll need to get started on your path of becoming a qualified Red Team cyber security specialist. We provide you with hands-on experience of reliable red teaming strategies including identifying, preventing, and mitigating attack vulnerabilities. You’ll learn how to adopt a hacker’s mindset and abuse/violate IT systems and infrastructure that are exposed to a future cyber-attack/threat.
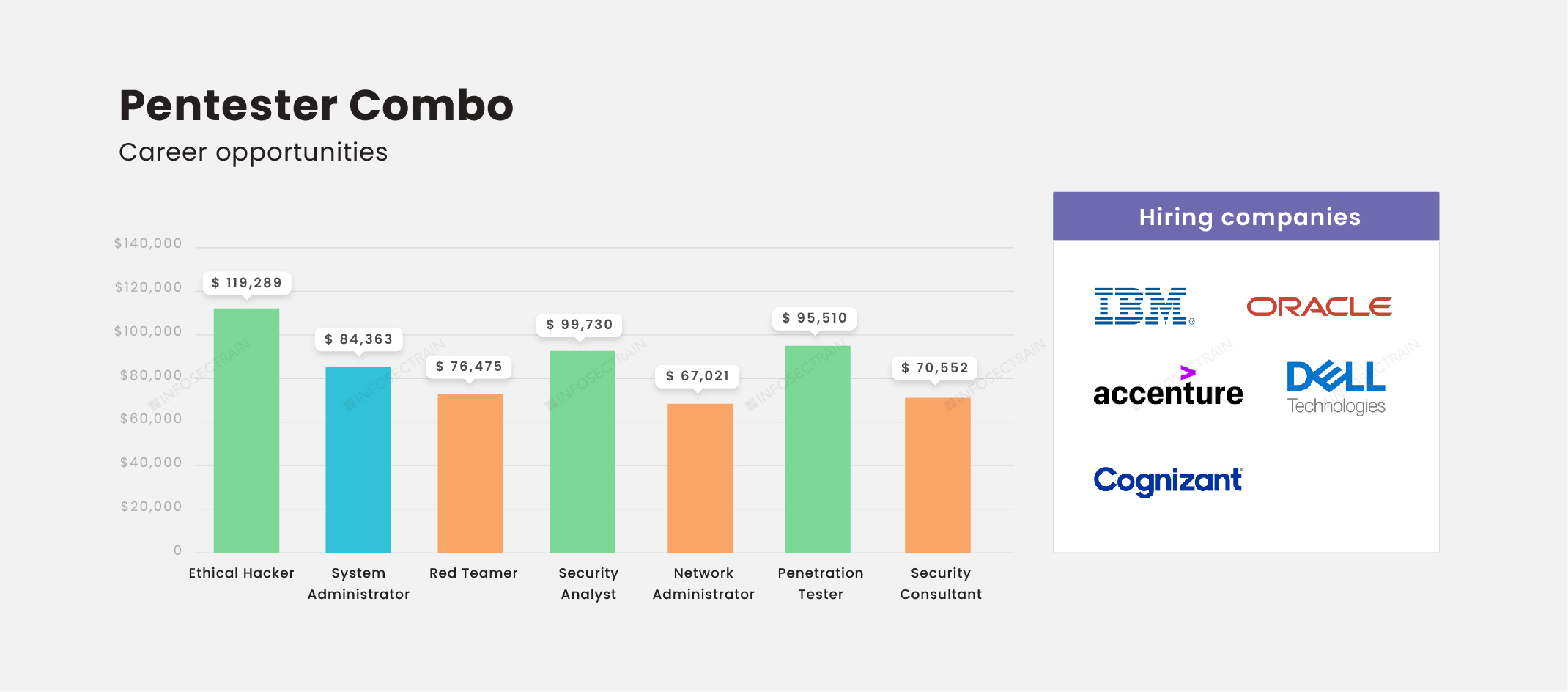
This combo course employs a simplified method of finding and fixing flaws, with everything from disclosure to compensation managed through a single dashboard.
There is no particular exam for bug bounty and Red Team but the exam details of CEH v12 is given below:
| Certification Name | 312-50 (ECC EXAM), 312-50 (VUE) |
| Exam Format | Multiple Choice |
| No. of Questions | 125 |
| Exam Duration | 4 Hours |
| Exam Delivery | ECC EXAM, VUE |
After completing the Pentester Combo Training course, you will have a thorough understanding of:
Null Sessions

18 + years of experience in Information Technology industry with specialization in Information Security A distinguished Information Security professional with comprehensive knowledge across all domains of Information Security. Expertise ranges from Vulnerability Assessment & Penetration Testing to Application Security, and encompasses Security Solutions as well as IT Governance, Risk & Compliance
18+ Years Of Experience
Sanyam is an Information Security Consultant & Trainer with 10+ years of hands-on experience in Security Testing, Cloud Security, Threat Hunting and DevOps. He is adept at designing tailored training programs and courseware on Security Solutions for various organizations.
10+ Years Of Experience

18 + years of experience in Information Technology industry with specialization in Information Security A distinguished Information Security professional with comprehensive knowledge across all domains of Information Security. Expertise ranges from Vulnerability Assessment & Penetration Testing to Application Security, and encompasses Security Solutions as well as IT Governance, Risk & Compliance
18+ Years Of Experience
Sanyam is an Information Security Consultant & Trainer with 10+ years of hands-on experience in Security Testing, Cloud Security, Threat Hunting and DevOps. He is adept at designing tailored training programs and courseware on Security Solutions for various organizations.
10+ Years Of Experience

18 + years of experience in Information Technology industry with specialization in Information Security A distinguished Information Security professional with comprehensive knowledge across all domains of Information Security. Expertise ranges from Vulnerability Assessment & Penetration Testing to Application Security, and encompasses Security Solutions as well as IT Governance, Risk & Compliance
18+ Years Of Experience
Sanyam is an Information Security Consultant & Trainer with 10+ years of hands-on experience in Security Testing, Cloud Security, Threat Hunting and DevOps. He is adept at designing tailored training programs and courseware on Security Solutions for various organizations.
10+ Years Of Experience

Customized schedule
Learn at your dedicated hour
Instant clarification of doubt
Guaranteed to run

Flexibility, Convenience & Time Saving
More Effective
Learning Cost Savings

Anytime, Anywhere – Across The Globe
Hire A Trainer
At Your Own Pace
Customized Corporate Training




 Thoroughly enjoyed the course and the continuous support from the entire team..
Thoroughly enjoyed the course and the continuous support from the entire team..


 It was a good experience. Looking forward to career growth with Infosectrain. Thank you
It was a good experience. Looking forward to career growth with Infosectrain. Thank you


 Really interesting courses are delivered by really knowledgeable instructors. Worth the fees
Really interesting courses are delivered by really knowledgeable instructors. Worth the fees


 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.


 I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.
I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.


 I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.
I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.


 Thoroughly enjoyed the course and the continuous support from the entire team..
Thoroughly enjoyed the course and the continuous support from the entire team..


 It was a good experience. Looking forward to career growth with Infosectrain. Thank you
It was a good experience. Looking forward to career growth with Infosectrain. Thank you


 Really interesting courses are delivered by really knowledgeable instructors. Worth the fees
Really interesting courses are delivered by really knowledgeable instructors. Worth the fees


 The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.
The training was awesome. Helped me clear my concepts and also reduced my preparation time to 1/3rd. Thank you, trainer, for all your dedication to bring your gladiators to pace.


 I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.
I loved the training. Coming for more soon. The trainer is easily reachable and helpful.. I loved the staggered payment option given.


 I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.
I must say the admin team is excellent and punctual. The trainers are actually the nerve of the team and know how to engage with the students across all the topics.
 Certified & Experienced Instructors
Certified & Experienced Instructors
 Post Training Support
Post Training Support
 Customized Training
Customized Training
 Flexible Schedule
Flexible Schedule
 Access to Recorded Sessions
Access to Recorded Sessions
